Cybercriminals Exploit Microsoft Teams to Deliver Deceptive Billing Scams
In a recent wave of cyberattacks, malicious actors have been exploiting Microsoft Teams’ legitimate features to distribute fraudulent billing notifications, deceiving users into divulging sensitive information. By manipulating the platform’s Invite a Guest functionality and crafting deceptive team names, these attackers bypass traditional email security measures, delivering scams that appear to originate from trusted Microsoft services.
Exploiting Trust in Collaboration Platforms
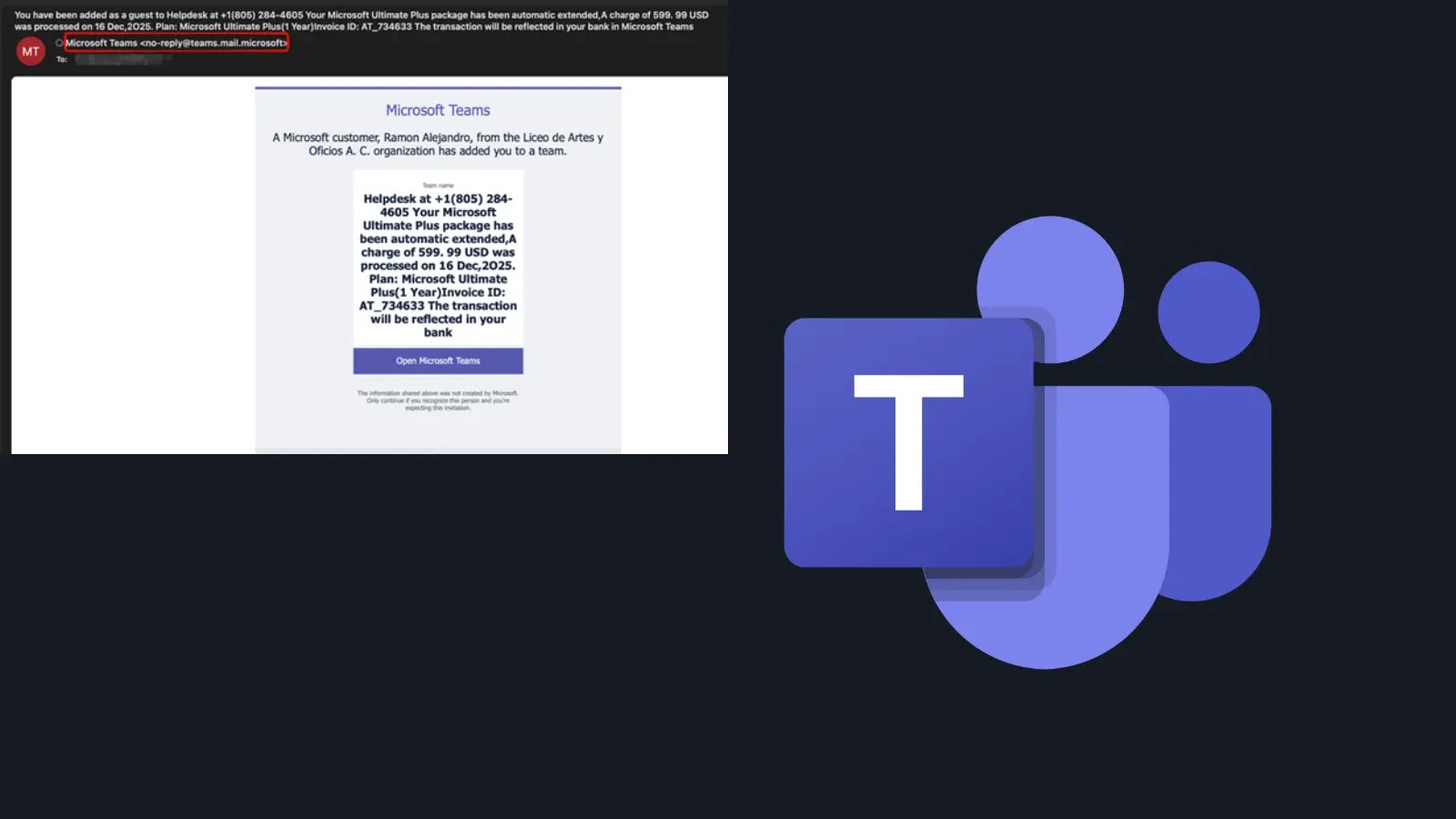
The attackers’ strategy hinges on the inherent trust users place in automated notifications from collaboration tools like Microsoft Teams. Instead of employing conventional phishing tactics such as email spoofing or embedding malicious links, these cybercriminals create new teams within Microsoft Teams, assigning them names that mimic urgent financial alerts. These deceptive names often reference subscription renewals or auto-payment notices to instill a sense of urgency and prompt immediate action from the recipient.
Anatomy of the Attack
A typical instance of this scam involves team names designed to alarm the recipient, such as:
Subscription Auto-Pay Notice (Invoice ID: 2025_614632PPOT_SAG Amount 629.98 USD). If you did not authorize or complete this monthly Payment, please contact our support team urgently.
Once the fraudulent team is established, the attacker utilizes the Invite a Guest feature to send invitations to external targets. The recipient receives an email from a legitimate Microsoft address (e.g., [email protected]), which easily passes email authentication protocols like SPF, DKIM, and DMARC. The email prominently displays the malicious team name containing the fraudulent billing message and a support phone number, lending an air of credibility to the scam.
Leveraging Social Engineering
This campaign distinguishes itself by employing voice-based social engineering, commonly known as vishing. Instead of directing victims to a counterfeit website to harvest credentials, the attackers instruct them to call a fraudulent support line to resolve the alleged billing issue. This method exploits the victim’s trust in voice communication, making them more susceptible to divulging sensitive information over the phone.
Obfuscation Techniques to Evade Detection
To circumvent automated content filters, the attackers employ various obfuscation techniques within the team names. These include character substitutions, mixing Unicode characters, and using visually similar glyphs to disguise the true nature of the message. Such tactics make it challenging for security systems to detect and block these malicious invitations effectively.
Scale and Impact of the Campaign
The scale of this operation is significant, indicating a broad, indiscriminate approach rather than targeted espionage. Security researchers recorded a total of 12,866 phishing messages distributed during the campaign’s peak, averaging 990 messages daily. These attacks reached approximately 6,135 distinct customers, underscoring the widespread nature of the threat.
Targeted Sectors and Geographic Distribution
The attackers aimed to exploit the widespread adoption of Microsoft Teams across various industries. The manufacturing, engineering, and construction sectors bore the brunt of the activity, accounting for 27.4% of affected organizations. This was followed by the Technology/SaaS/IT sector at 18.6% and the Education sector at 14.9%. Other affected verticals included professional services, government, and finance.
Geographically, the campaign demonstrated a global reach, with a primary focus on North American targets. Organizations in the United States comprised 67.9% of the victim pool. European entities accounted for 15.8%, followed by Asia at 6.4%. Within the Latin American (LATAM) region, the distribution was as follows:
– Brazil: 44%
– Mexico: 31%
– Argentina: 11%
– Colombia: 8%
– Chile: 4%
– Peru: 2%
Addressing the Security Gap
This campaign highlights a critical vulnerability in collaboration platform security: the reliance on content inspection within invitations generated by trusted platforms. Since the email delivery mechanism is legitimate, organizations cannot depend solely on email authentication protocols to block these threats.
Recommendations for Mitigation
To protect against such sophisticated phishing attacks, organizations should consider the following measures:
1. User Education: Train employees to scrutinize unexpected Teams invitations, especially those containing urgent financial language, phone numbers, or unfamiliar team names.
2. Verification Protocols: Encourage users to verify the legitimacy of unexpected billing notifications by contacting known support channels directly, rather than using contact information provided in unsolicited messages.
3. Enhanced Monitoring: Implement monitoring systems to detect and alert on unusual team creation activities or a high volume of guest invitations, which may indicate a phishing campaign in progress.
4. Access Controls: Review and adjust Microsoft Teams’ external collaboration settings to limit the ability of external users to create teams or send invitations without proper oversight.
5. Content Filtering: Develop and deploy advanced content filtering mechanisms capable of detecting obfuscation techniques used in phishing attempts, such as character substitutions and mixed Unicode characters.
Conclusion
The exploitation of Microsoft Teams’ functionalities by cybercriminals to deliver deceptive billing scams underscores the evolving nature of phishing attacks. By leveraging trusted platforms and sophisticated social engineering tactics, attackers can bypass traditional security measures, making it imperative for organizations to adopt a multi-layered approach to cybersecurity. Continuous user education, vigilant monitoring, and robust access controls are essential components in defending against such insidious threats.