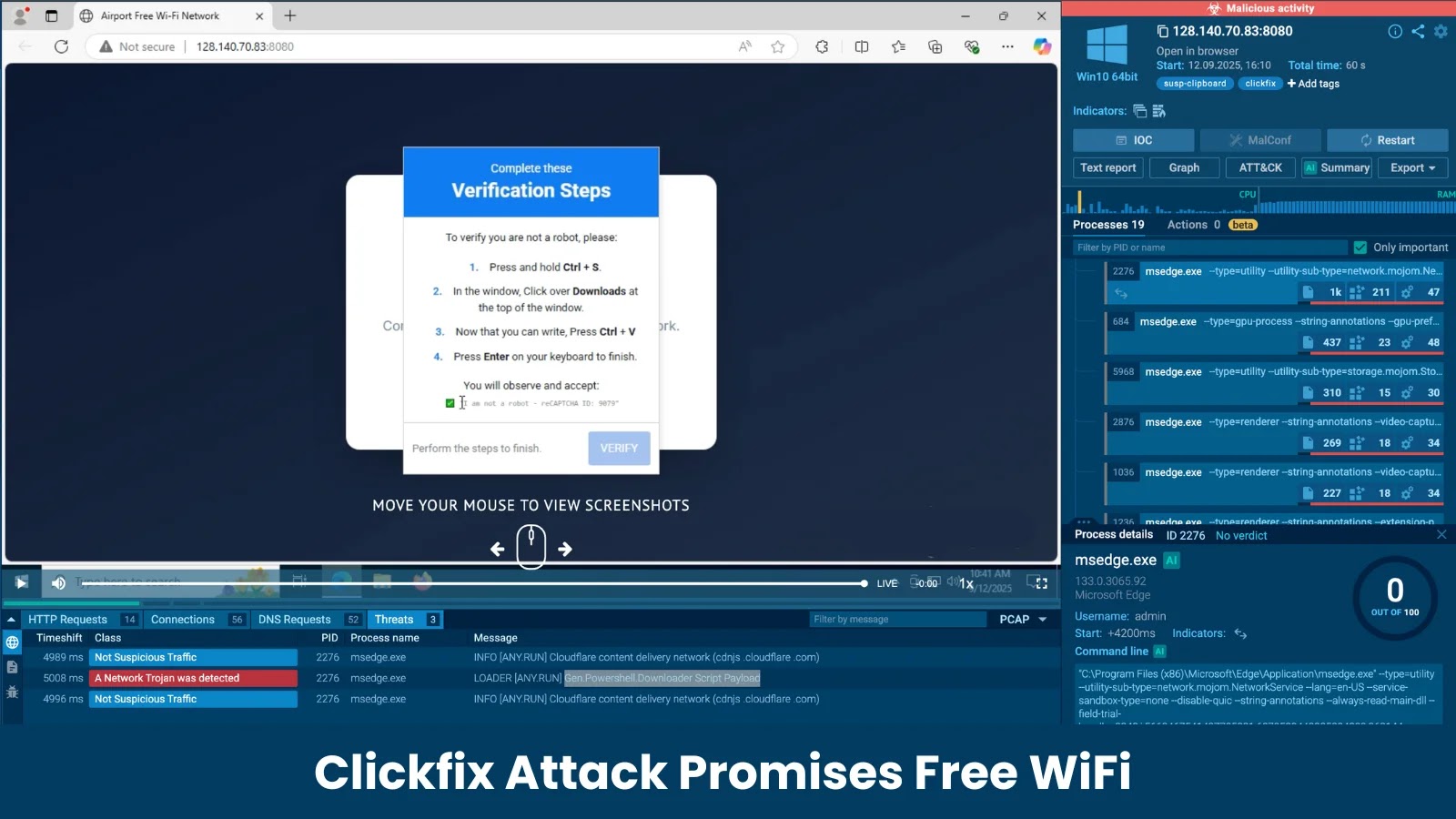
In a recent cybersecurity investigation, researchers have uncovered a sophisticated social engineering campaign that preys on individuals seeking free internet access in public spaces. This deceptive strategy, known as the ClickFix attack, manipulates users into executing malicious PowerShell scripts under the guise of routine human verification processes.
The Lure of Free Wi-Fi
Public venues such as airports, cafes, and hotels often provide complimentary Wi-Fi services, making them prime targets for cybercriminals. In this campaign, unsuspecting users attempting to connect to what appears to be free Wi-Fi are redirected to counterfeit captive portals. These portals are meticulously designed to resemble legitimate network login pages, complete with familiar logos and CAPTCHA prompts intended to establish a false sense of security.
Deceptive Verification Process
The core of the ClickFix attack lies in its manipulation of user behavior through a deceptive verification process. After interacting with the fake CAPTCHA, users are presented with a pop-up window detailing a series of Verification Steps. These instructions guide the user through specific keyboard shortcuts:
1. Press `Ctrl+S` to save the web page.
2. Navigate to the browser’s downloads window.
3. Press `Enter` to open the downloaded file.
This sequence is a calculated social engineering tactic designed to bypass standard browser security warnings associated with downloading executable files. By instructing users to save and run the file themselves, attackers effectively obtain consent to execute malicious code. The downloaded file, contrary to user expectations, is not a benign image or document but a script that initiates the infection process.
Execution of Malicious PowerShell Script
Upon execution of the downloaded file, a malicious PowerShell script is launched. Analysis of the attack chain reveals that this script acts as a downloader, establishing a connection to a command-and-control server to fetch the primary malware payload. In this campaign, the payload has been identified as a network trojan.
PowerShell is a powerful tool for attackers because it is integrated into Windows and can execute commands, scripts, and payloads directly in memory, often evading detection by traditional antivirus solutions. This type of fileless malware can be used for a wide range of malicious activities, including stealing sensitive information, deploying ransomware, or providing a persistent backdoor for remote access to the compromised device.
Broader Implications and Variants of ClickFix Attacks
The ClickFix technique represents a significant evolution in social engineering attacks, exploiting user trust and familiarity with routine verification processes. Beyond the free Wi-Fi lure, similar tactics have been observed in various contexts:
– Fake Cloudflare Verification Pages: Attackers create convincing replicas of Cloudflare security verification pages, prompting users to execute malicious commands under the pretense of verifying their humanity. ([cybersecuritynews.com](https://cybersecuritynews.com/new-clickfix-attack-exploits-fake-cloudflare-human-check/?utm_source=openai))
– Impersonation of Trusted Platforms: Malicious actors have been known to mimic platforms like Google Meet and Zoom, presenting users with fake error messages that lead to the execution of harmful scripts. ([cybersecuritynews.com](https://cybersecuritynews.com/clickfix-leveraging-gmeet-and-zoom/?utm_source=openai))
– Exploitation of Government Websites: Some campaigns have involved the creation of counterfeit Ministry of Defense websites, tricking users into downloading what appear to be official documents but are, in fact, malware. ([cybersecuritynews.com](https://cybersecuritynews.com/new-clickfix-attack-mimics-ministry-of-defense-website/?utm_source=openai))
Protective Measures Against ClickFix Attacks
To safeguard against ClickFix and similar social engineering attacks, users should adopt the following practices:
1. Exercise Caution with Public Wi-Fi: Be vigilant when connecting to public Wi-Fi networks. Verify the legitimacy of the network with the establishment’s staff and avoid accessing sensitive information over unsecured connections.
2. Scrutinize Verification Prompts: Be wary of unexpected verification prompts, especially those that require unusual actions such as executing commands or downloading files. Legitimate services typically do not require such steps for verification.
3. Keep Software Updated: Regularly update your operating system and software to patch known vulnerabilities that attackers might exploit.
4. Employ Security Solutions: Utilize reputable antivirus and anti-malware programs that can detect and prevent malicious activities.
5. Educate Yourself and Others: Stay informed about common social engineering tactics and share this knowledge with peers to collectively enhance cybersecurity awareness.
Conclusion
The ClickFix attack underscores the evolving nature of cyber threats, where attackers increasingly rely on psychological manipulation rather than technical exploits. By understanding the mechanisms of such attacks and adopting proactive security measures, individuals can significantly reduce their risk of falling victim to these deceptive schemes.