In a sophisticated cyberattack campaign, threat actors are impersonating recruiters to target Chief Financial Officers (CFOs) and financial executives across multiple global regions, including Europe, Africa, Canada, the Middle East, and South Asia. The attackers employ a legitimate remote access tool, NetBird, to infiltrate and persist within victims’ systems.
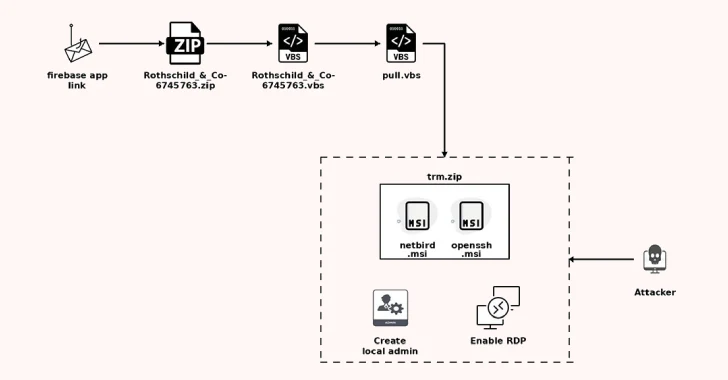
The campaign begins with phishing emails that appear to come from reputable recruitment firms, such as Rothschild & Co., offering enticing strategic opportunities. These emails contain links disguised as PDF attachments, which redirect recipients to malicious URLs hosted on platforms like Firebase. To access the next stage, victims are prompted to solve a CAPTCHA, a tactic designed to evade automated security defenses.
Upon completing the CAPTCHA, victims download a ZIP archive containing a Visual Basic Script (VBScript). Executing this script initiates a multi-stage infection process:
1. First-Stage VBScript: Downloads and executes a second-stage VBScript from an external server.
2. Second-Stage VBScript: Retrieves a payload named trm.zip, extracting two MSI installer files for NetBird and OpenSSH.
3. Installation and Persistence: Installs both programs, creates a hidden local account, enables remote desktop access, and sets up scheduled tasks to ensure NetBird launches upon system reboot. Desktop shortcuts for NetBird are removed to minimize detection.
This method of using legitimate tools for malicious purposes highlights a growing trend among cybercriminals. By leveraging trusted applications like NetBird, attackers can establish persistent access while evading traditional security measures.
The campaign’s sophistication is evident in its multi-stage approach, combining social engineering with advanced evasion techniques. The use of CAPTCHAs and encrypted redirect URLs demonstrates a deliberate effort to bypass automated security systems and engage victims directly.
This incident underscores the importance of vigilance among financial executives and organizations. To mitigate such threats, it is crucial to:
– Verify Sender Identities: Scrutinize unsolicited emails, especially those offering unexpected opportunities.
– Exercise Caution with Attachments and Links: Avoid opening attachments or clicking on links from unknown or unverified sources.
– Implement Robust Security Measures: Utilize advanced email filtering, endpoint protection, and regular security training for staff.
By adopting these practices, organizations can enhance their defenses against increasingly sophisticated phishing campaigns targeting high-level executives.