Cybercriminals Enhance ClickFix Attacks with Fake CAPTCHAs and Trusted Web Services
Cybersecurity experts have recently uncovered a sophisticated campaign that leverages the ClickFix social engineering technique, integrating fake CAPTCHA prompts with signed Microsoft Application Virtualization (App-V) scripts to deploy the Amatera information stealer. This method represents a significant evolution in cyberattack strategies, utilizing trusted components to evade detection and compromise enterprise systems.
Understanding ClickFix and Its Evolution
ClickFix is a deceptive tactic where attackers present users with fake error messages or prompts, urging them to execute specific commands to resolve non-existent issues. Traditionally, this involved direct execution of PowerShell commands. However, the latest campaign introduces a more intricate approach by incorporating fake CAPTCHA verifications and exploiting legitimate Microsoft scripts.
The Attack Sequence
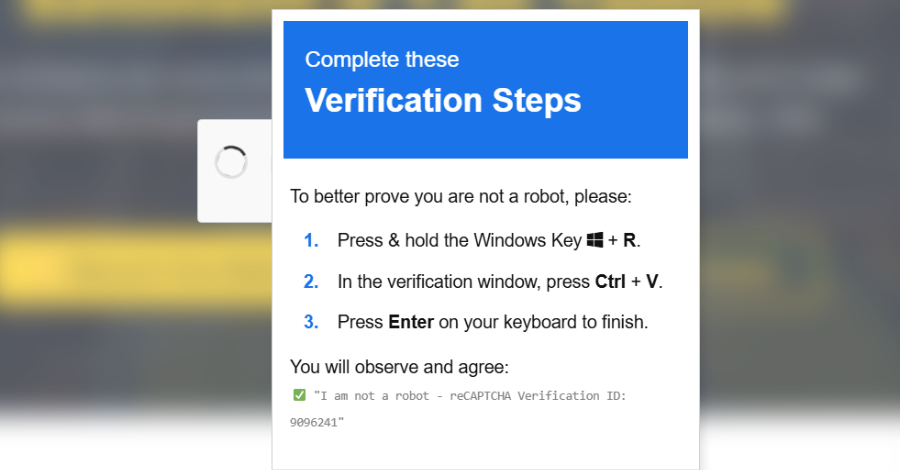
The attack initiates when a user encounters a counterfeit CAPTCHA verification prompt. Believing it to be legitimate, the user is instructed to copy a command and execute it via the Windows Run dialog. Unlike previous ClickFix attacks that directly invoked PowerShell, this command exploits SyncAppvPublishingServer.vbs, a signed Visual Basic Script associated with Microsoft’s App-V. This script acts as a proxy, executing PowerShell commands through a trusted Microsoft component, thereby concealing the malicious activity.
Exploiting Trusted Components
By utilizing SyncAppvPublishingServer.vbs, attackers effectively bypass PowerShell execution restrictions and evade defensive measures. This method, known as living-off-the-land (LotL), involves abusing legitimate system tools for malicious purposes. The use of App-V scripts is particularly noteworthy, as this virtualization solution is integrated into Enterprise and Education editions of Windows 10 and 11, as well as modern Windows Server versions. Consequently, systems lacking App-V support are immune to this specific attack vector.
Targeting Enterprise Systems
The reliance on App-V indicates that enterprise-managed systems are the primary targets of this campaign. In environments where App-V is absent or disabled, the malicious command fails to execute, highlighting the attackers’ focus on infiltrating corporate networks.
Advanced Evasion Techniques
Once the initial command is executed, the obfuscated loader performs checks to ensure it’s not running within sandboxed environments, a common tactic to evade detection by security researchers. Subsequently, it retrieves configuration data from a public Google Calendar (ICS) file, effectively turning a trusted third-party service into a dead drop resolver. This approach allows attackers to rapidly adjust delivery parameters or rotate infrastructure without redeploying earlier stages of the attack chain, thereby extending the lifespan of the initial infection vector.
Multi-Stage Payload Delivery
Parsing the calendar event file leads to the retrieval of additional loader stages, including a PowerShell script that functions as an intermediate loader to execute the next stage directly in memory. This step results in the retrieval of a PNG image from domains like gcdnb.pbrd[.]co and iili[.]io via WinINet APIs. The image conceals an encrypted and compressed PowerShell payload, which is decrypted, decompressed in memory, and executed using Invoke-Expression. Ultimately, this sequence culminates in the execution of a shellcode loader designed to launch the Amatera Stealer.
The Amatera Stealer
Amatera is an information-stealing malware capable of exfiltrating sensitive data from infected systems. Its deployment through such a sophisticated attack chain underscores the evolving tactics of cybercriminals and the increasing complexity of modern cyber threats.
Broader Implications and Related Campaigns
This campaign is part of a broader trend where attackers exploit trusted components and services to evade detection. For instance, the ClearFake campaign has been known to infect thousands of websites using fake reCAPTCHA and Cloudflare Turnstile verifications to spread information stealers like Lumma Stealer and Vidar Stealer. Similarly, the CastleLoader malware has utilized fake GitHub repositories and ClickFix phishing to infect devices with various information stealers and remote access trojans.
Mitigation Strategies
To defend against such sophisticated attacks, organizations should implement the following measures:
1. User Education: Train employees to recognize social engineering tactics, such as fake CAPTCHAs and deceptive prompts, reducing the likelihood of successful attacks.
2. Restrict Script Execution: Implement policies to control the execution of scripts, especially those that can be exploited for malicious purposes, like SyncAppvPublishingServer.vbs.
3. Monitor Network Traffic: Regularly monitor network traffic for unusual patterns, such as connections to unfamiliar domains or the use of trusted services in unexpected ways.
4. Keep Systems Updated: Ensure that all systems are up-to-date with the latest security patches to mitigate vulnerabilities that could be exploited by attackers.
5. Implement Multi-Factor Authentication (MFA): Use MFA to add an additional layer of security, making it more difficult for attackers to gain unauthorized access.
6. Deploy Endpoint Detection and Response (EDR) Solutions: Utilize EDR solutions to detect and respond to suspicious activities on endpoints promptly.
Conclusion
The integration of fake CAPTCHAs, trusted Microsoft scripts, and legitimate web services in this ClickFix campaign highlights the increasing sophistication of cyber threats. By exploiting trusted components and services, attackers can effectively evade detection and compromise enterprise systems. Organizations must remain vigilant, continuously educate their employees, and implement robust security measures to defend against these evolving threats.