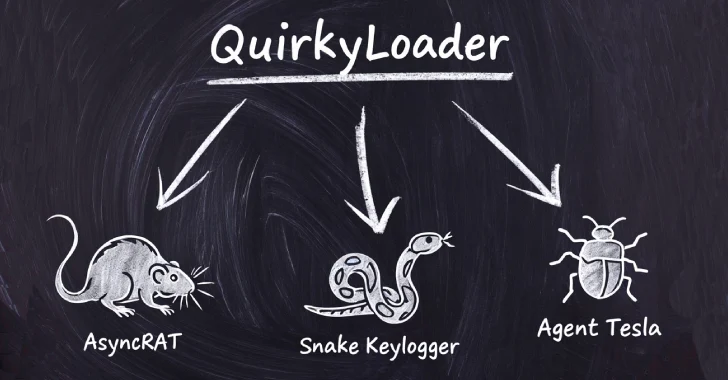
Cybersecurity experts have identified a new malware loader, QuirkyLoader, actively used since November 2024 to disseminate various malicious payloads through email spam campaigns. This loader has been instrumental in spreading malware families such as Agent Tesla, AsyncRAT, Formbook, Masslogger, Remcos RAT, Rhadamanthys Stealer, and Snake Keylogger.
IBM X-Force researchers have detailed that attackers are leveraging both legitimate email service providers and self-hosted servers to dispatch spam emails. These emails contain malicious archives comprising a dynamic link library (DLL), an encrypted payload, and a legitimate executable. The attackers employ DLL side-loading, a technique where executing the legitimate file also loads the malicious DLL. This DLL then decrypts and injects the final payload into targeted processes using process hollowing, specifically targeting processes like AddInProcess32.exe, InstallUtil.exe, or aspnet_wp.exe.
The QuirkyLoader has been observed in limited campaigns over recent months, notably in July 2025, targeting regions such as Taiwan and Mexico. In Taiwan, the campaign specifically targeted employees of Nusoft Taiwan, a network and internet security research company based in New Taipei City, aiming to infect them with Snake Keylogger. This malware is capable of stealing sensitive information from popular web browsers, capturing keystrokes, and accessing clipboard content. The campaign in Mexico appeared more random, delivering Remcos RAT and AsyncRAT through the infection chains.
The threat actors consistently develop the DLL loader module using .NET languages and employ ahead-of-time (AOT) compilation. This method compiles the code into native machine code before execution, making the resulting binary resemble those written in C or C++.
Emerging Phishing Techniques
In addition to QuirkyLoader, cybercriminals are adopting innovative phishing tactics, such as QR code phishing (quishing). These methods involve splitting malicious QR codes into two parts or embedding them within legitimate ones in email messages. Phishing kits like Gabagool and Tycoon are facilitating these tactics to evade detection. Malicious QR codes are particularly effective because they are not readable by humans, often bypass traditional security measures like email filters and link scanners, and can lead users to switch to mobile devices, moving them outside the company’s security perimeter.
Furthermore, the PoisonSeed threat actor has developed a phishing kit designed to acquire credentials and two-factor authentication (2FA) codes from individuals and organizations. This kit impersonates login services from prominent CRM and bulk email companies like Google, SendGrid, and Mailchimp, targeting individuals’ credentials. PoisonSeed employs spear-phishing emails embedding malicious links that redirect victims to their phishing kit. A notable aspect of this kit is the use of precision-validated phishing, where the attacker validates an email address in real-time while presenting a fake Cloudflare Turnstile challenge to the user. Once these checks are passed, a login form impersonating the legitimate online platform appears, allowing the threat actors to capture submitted credentials and relay them to the service.