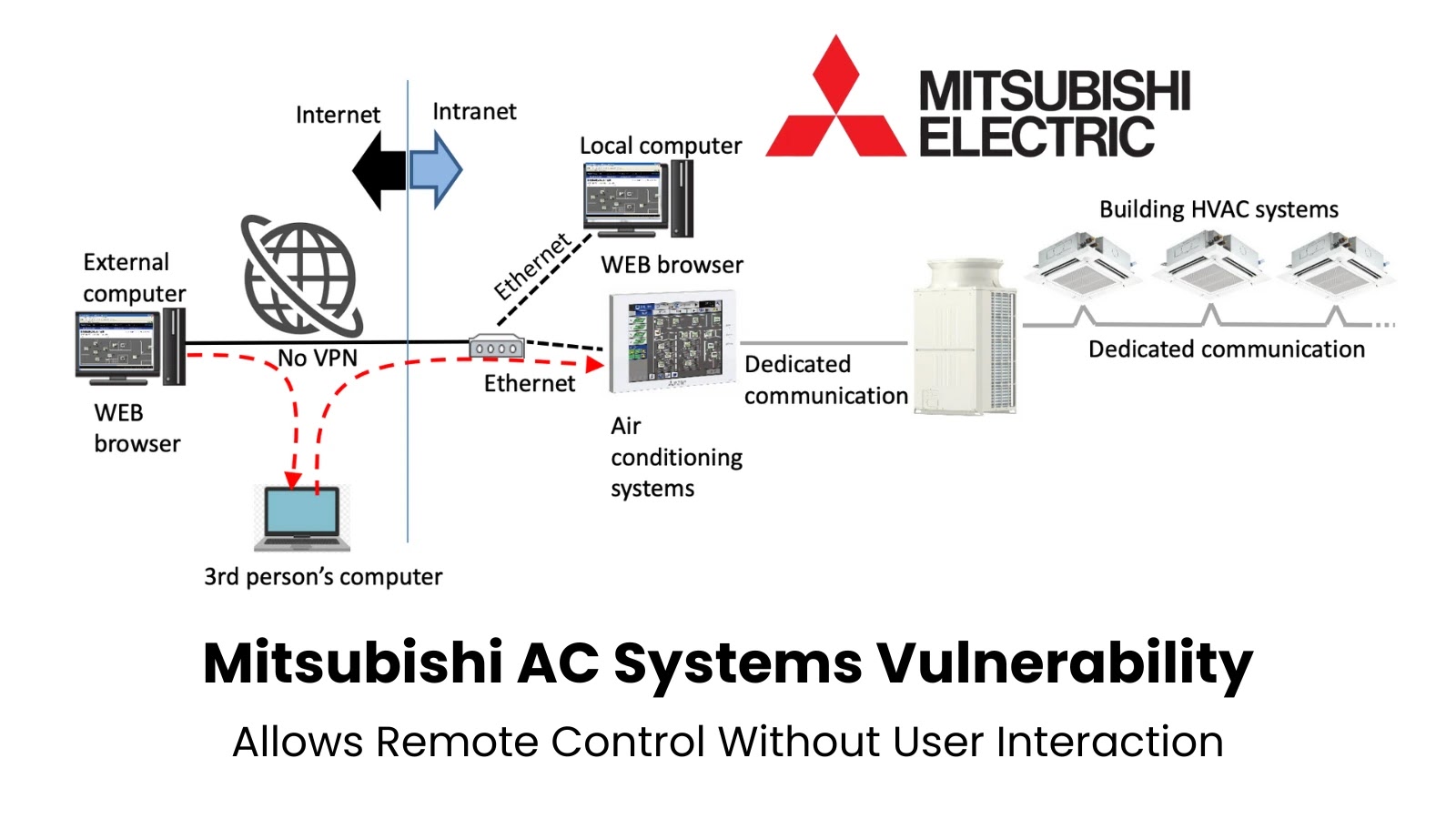
Mitsubishi Electric has recently disclosed a significant security vulnerability affecting 27 models of its air conditioning systems. This flaw, identified as CVE-2025-3699, allows remote attackers to gain unauthorized control over HVAC systems without any user interaction. The vulnerability has been assigned a CVSS v3.1 base score of 9.8, indicating its critical severity.
Nature of the Vulnerability
The issue arises from a Missing Authentication for Critical Function weakness, which permits attackers to bypass authentication mechanisms entirely. By exploiting this flaw, malicious actors can:
– Illegally control air conditioning systems.
– Access sensitive information.
– Tamper with firmware using disclosed data.
Notably, the attack can be executed remotely over network connections without requiring any user interaction, making it particularly dangerous.
Affected Products
The vulnerability impacts a wide range of Mitsubishi Electric air conditioning systems, including:
– G-50 Series: Versions 3.37 and prior.
– GB-50 Series: Versions 3.37 and prior.
– AE-200 and AE-50 Series: Versions 8.01 and prior.
– EW-50 Series: Versions 8.01 and prior.
– Other Models: Including G-150AD, AG-150A, GB-24A, EB-50GU, TE-200A, TE-50A, TW-50A, and CMS-RMD-J, with various versions affected.
The extensive list of affected products underscores the potential impact on commercial buildings, industrial facilities, and other environments where these systems are deployed for climate control and building automation.
Discovery and Reporting
Security researcher Mihály Csonka discovered and reported the vulnerability to Mitsubishi Electric. This collaboration highlights the importance of coordinated efforts between the security community and manufacturers to identify and address critical infrastructure vulnerabilities.
Risk Evaluation
Successful exploitation of this vulnerability could allow an attacker to control the air conditioning system remotely. Given the critical nature of HVAC systems in maintaining environmental conditions, unauthorized control could lead to operational disruptions, potential equipment damage, and compromised safety.
Technical Details
The vulnerability is characterized by a lack of authentication for critical functions within the affected systems. This flaw allows attackers to:
– Bypass authentication mechanisms.
– Illegally control air conditioning systems.
– Access and disclose sensitive information.
– Tamper with firmware using disclosed data.
The attack requires no user interaction and can be executed remotely over network connections, increasing the risk of exploitation.
Mitigation Measures
Mitsubishi Electric is currently preparing improved versions of the following products to mitigate this vulnerability:
– AE-200J, AE-200A, AE-200E, AE-50J, AE-50A, AE-50E, EW-50J, EW-50A, EW-50E, TE-200A, TE-50A, and TW-50A.
To minimize the risk of exploitation, Mitsubishi Electric recommends the following mitigation measures:
– Restrict Access: Limit access to air conditioning systems from untrusted networks and hosts.
– Physical Security: Restrict physical access to air conditioning systems, computers that can access them, and the networks connected to them.
– Use Antivirus Software: Install and update antivirus software on computers that connect to air conditioning systems.
– Update Systems: Ensure operating systems and web browsers on connected computers are updated to the latest versions.
Additionally, Mitsubishi Electric emphasizes that their air conditioning systems are designed for use within secure intranet environments or networks protected by VPN infrastructure. Proper network segmentation and access controls are crucial in mitigating the risk associated with this vulnerability.
Conclusion
The disclosure of CVE-2025-3699 highlights the critical importance of securing industrial control systems against remote exploitation. Organizations utilizing Mitsubishi Electric air conditioning systems should promptly assess their network configurations, apply recommended mitigation measures, and stay informed about firmware updates to protect against potential attacks.