Critical WSUS Vulnerability Under Active Exploitation: Immediate Action Required
In recent weeks, cybersecurity experts have observed a significant uptick in malicious activities targeting Microsoft’s Windows Server Update Services (WSUS). This surge is directly linked to the exploitation of a critical vulnerability, identified as CVE-2025-59287, which allows unauthenticated attackers to execute arbitrary code with SYSTEM privileges on affected servers. The flaw, stemming from unsafe deserialization of untrusted data within WSUS, poses a severe risk to enterprise networks worldwide.
Understanding CVE-2025-59287
CVE-2025-59287 is a remote code execution vulnerability that affects all supported versions of Windows Server from 2012 through 2025. The issue arises from the WSUS server’s handling of encrypted AuthorizationCookie objects. Specifically, the GetCookie() endpoint processes these objects without adequate validation, leading to potential exploitation. Microsoft has assigned this vulnerability a CVSS v3.1 score of 9.8, categorizing it as critical due to its ease of exploitation without the need for authentication.
Timeline of Events
– October 14, 2025: Microsoft initially disclosed the vulnerability during its October Patch Tuesday, providing a partial fix.
– October 23, 2025: An out-of-band emergency patch was released after it was determined that the initial fix was insufficient.
– October 24, 2025: Exploitation attempts were detected in the wild, with attackers leveraging publicly available proof-of-concept (PoC) exploits to target vulnerable WSUS servers.
– October 29, 2025: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-59287 to its Known Exploited Vulnerabilities (KEV) Catalog, urging organizations to apply patches by November 14, 2025.
Current Threat Landscape
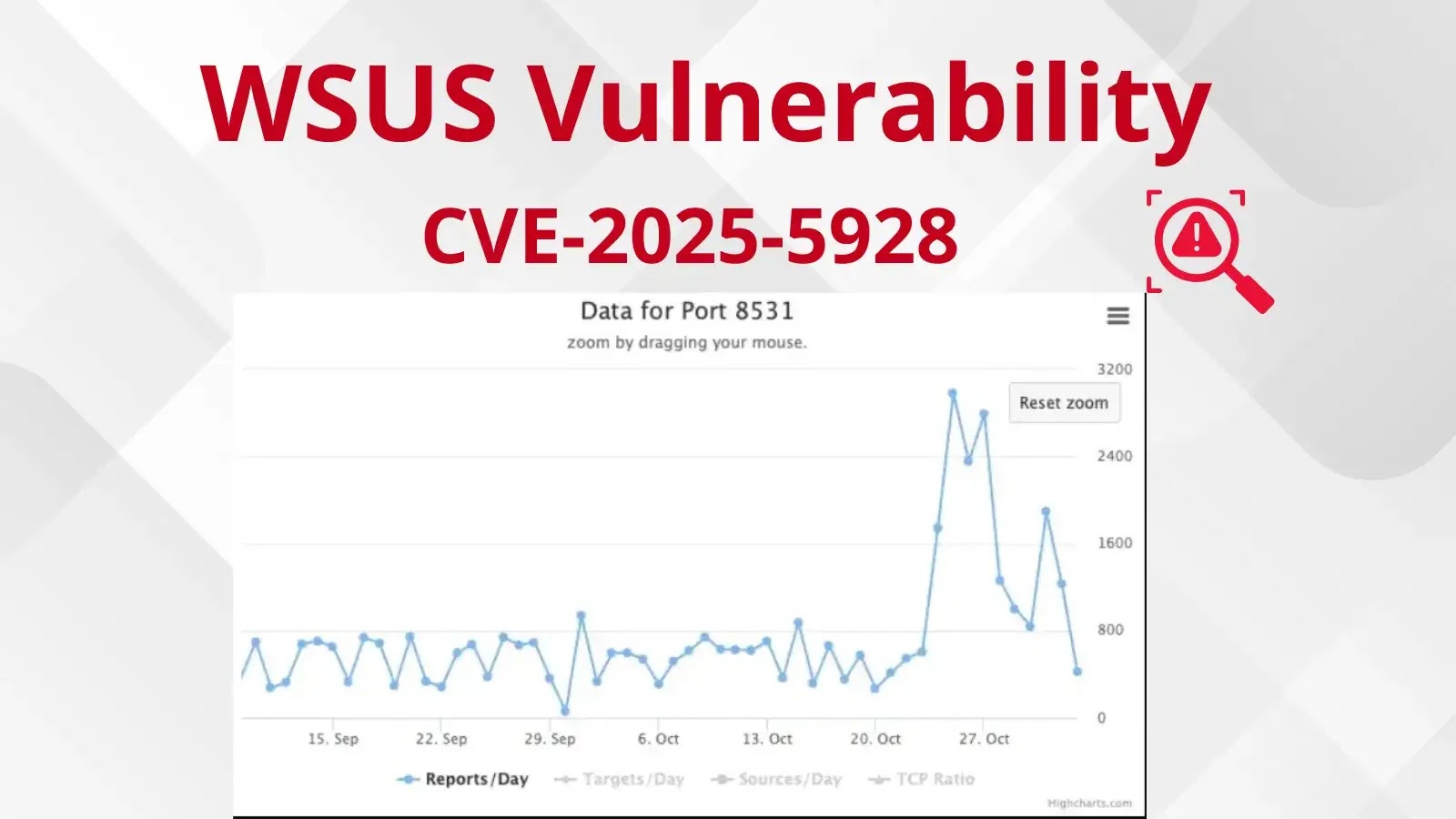
Security monitoring services, including data from Shadowserver, have reported a dramatic increase in scans targeting TCP ports 8530 and 8531, which are associated with WSUS. While some of this activity is attributed to legitimate security research, a significant portion originates from unknown sources, indicating potential exploitation attempts. The scanning activity correlates directly with CVE-2025-59287, suggesting that attackers are actively seeking vulnerable WSUS servers to compromise.
Exploitation Techniques
Attackers are employing a two-stage approach:
1. Reconnaissance: Scanning for WSUS servers with open ports 8530 (unencrypted) and 8531 (TLS-encrypted) to identify vulnerable systems.
2. Exploitation: Once a vulnerable server is identified, attackers can exploit the deserialization flaw to execute arbitrary scripts, potentially gaining full control over the server and, by extension, the enterprise network.
The availability of technical details and PoC exploits has lowered the barrier to entry, enabling even moderately skilled threat actors to develop and deploy exploitation code.
Potential Impact
The successful exploitation of CVE-2025-59287 can have severe consequences, including:
– Unauthorized Access: Attackers can gain SYSTEM-level privileges, allowing them to execute any command or install malicious software.
– Data Exfiltration: Sensitive organizational data can be accessed and exfiltrated, leading to potential data breaches.
– Lateral Movement: Compromised WSUS servers can serve as a foothold for attackers to move laterally within the network, targeting other critical systems.
– Supply Chain Attacks: By controlling WSUS, attackers can distribute malicious updates to all connected client machines, effectively compromising the entire network.
Mitigation Strategies
Given the critical nature of this vulnerability, immediate action is required:
1. Apply Patches: Ensure that all WSUS servers are updated with the latest security patches released by Microsoft on October 23, 2025.
2. Restrict Access: Limit WSUS server access by configuring firewalls to restrict inbound traffic on ports 8530 and 8531 to only trusted internal networks.
3. Monitor Logs: Regularly review server logs for unusual activity, such as unexpected update approvals or anomalous traffic patterns.
4. Conduct Forensic Analysis: If exploitation is suspected, perform a comprehensive forensic investigation to determine the extent of the compromise and implement remediation measures.
5. Network Segmentation: Implement network segmentation to isolate WSUS servers from other critical systems, reducing the potential impact of a compromise.
Conclusion
The active exploitation of CVE-2025-59287 underscores the importance of timely patch management and vigilant network monitoring. Organizations utilizing WSUS must prioritize the application of security updates and implement robust access controls to mitigate the risk posed by this vulnerability. Failure to do so could result in significant operational disruptions and data breaches.