Cybersecurity experts have recently identified and addressed a significant security flaw in the figma-developer-mcp Model Context Protocol (MCP) server, a tool widely utilized for integrating artificial intelligence (AI) capabilities into Figma projects. This vulnerability, cataloged as CVE-2025-53967 with a Common Vulnerability Scoring System (CVSS) score of 7.5, is a command injection issue arising from inadequate validation of user inputs. This oversight permits attackers to execute arbitrary system commands on the host server, potentially leading to unauthorized remote code execution.
Understanding the Vulnerability
The core of this security flaw lies in the MCP server’s method of constructing and executing shell commands. By incorporating unvalidated user inputs directly into command-line strings, the server becomes susceptible to shell metacharacter injection. This means that special characters such as ‘|’, ‘>’, and ‘&&’ can be exploited by malicious actors to manipulate the server’s behavior. A GitHub advisory elaborates on this, stating that the server’s reliance on unvalidated user input within command-line strings opens the door to potential remote code execution under the server process’s privileges.
Potential Exploitation Scenarios
The Framelink Figma MCP server is designed to facilitate various operations within Figma by leveraging AI-powered coding agents like Cursor. However, this integration also introduces risks. An attacker could deceive the MCP client into performing unintended actions through indirect prompt injections. For instance, by crafting a malicious URL or header value, an attacker can inject arbitrary shell commands, leading to remote code execution on the host machine. This scenario is particularly concerning in environments where the MCP client and server communicate over networks that may be accessible to potential attackers, such as public Wi-Fi networks or compromised corporate devices.
Discovery and Reporting
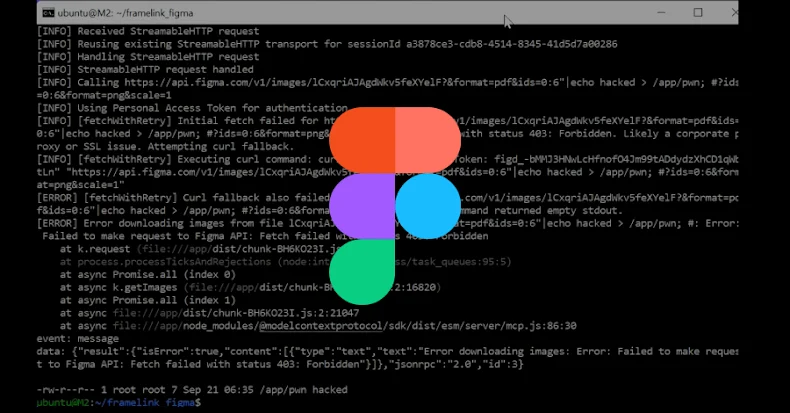
The vulnerability was discovered and reported by cybersecurity firm Imperva in July 2025. Security researcher Yohann Sillam from Imperva highlighted that the flaw originates during the construction of a command-line instruction used to send traffic to the Figma API endpoint. Specifically, the issue resides in the “src/utils/fetch-with-retry.ts” file. Here, the server initially attempts to retrieve content using the standard fetch API. If this attempt fails, it defaults to executing a curl command via child_process.exec, inadvertently introducing the command injection vulnerability.
Technical Breakdown of the Exploit
The exploitation process involves several steps:
1. Initialization Request: The MCP client sends an Initialize request to the MCP endpoint to obtain an mcp-session-id, which is essential for subsequent communications with the MCP server.
2. JSONRPC Request: The client then sends a JSONRPC request to the MCP server using the method tools/call to invoke tools like get_figma_data or download_figma_images.
The vulnerability is triggered when the server constructs a curl command by directly interpolating URL and header values into a shell command string. This approach allows a malicious actor to craft a specially designed URL or header value that injects arbitrary shell commands, potentially leading to remote code execution on the host machine.
Proof-of-Concept Attack Scenarios
In a proof-of-concept attack, a remote adversary on the same network—such as a public Wi-Fi or a compromised corporate device—can exploit this flaw by sending a series of requests to the vulnerable MCP server. Alternatively, an attacker could lure a victim into visiting a specially crafted website as part of a DNS rebinding attack. This technique involves manipulating the domain name system to bind a victim’s browser to a malicious server, thereby facilitating unauthorized actions.
Mitigation and Recommendations
The vulnerability has been addressed in version 0.6.3 of figma-developer-mcp, released on September 29, 2025. Users are strongly encouraged to update to this latest version to mitigate the risk. As a precautionary measure, developers should avoid using child_process.exec with untrusted input. Instead, switching to child_process.execFile is advisable, as it eliminates the risk of shell interpretation and enhances security.
Broader Implications and Industry Response
The emergence of this vulnerability underscores the critical need for security considerations to evolve alongside the rapid adoption of AI-driven development tools. Imperva emphasized that even tools intended for local execution can become significant entry points for attackers if not properly secured. This incident serves as a stark reminder of the importance of rigorous input validation and the potential consequences of overlooking such fundamental security practices.
Related Security Concerns
In a related development, cybersecurity firm FireTail disclosed that Google has opted not to address a new ASCII smuggling attack in its Gemini AI chatbot. This vulnerability could be exploited to craft inputs that bypass security filters, leading to undesirable responses. Such incidents highlight the broader challenges in securing AI-powered platforms and the necessity for continuous vigilance and proactive security measures.
Conclusion
The discovery and subsequent patching of the CVE-2025-53967 vulnerability in the Figma MCP server highlight the ever-present need for robust security practices in the development and deployment of AI-integrated tools. Developers and organizations must remain vigilant, ensuring that security measures keep pace with technological advancements to protect against potential exploits and safeguard sensitive data.