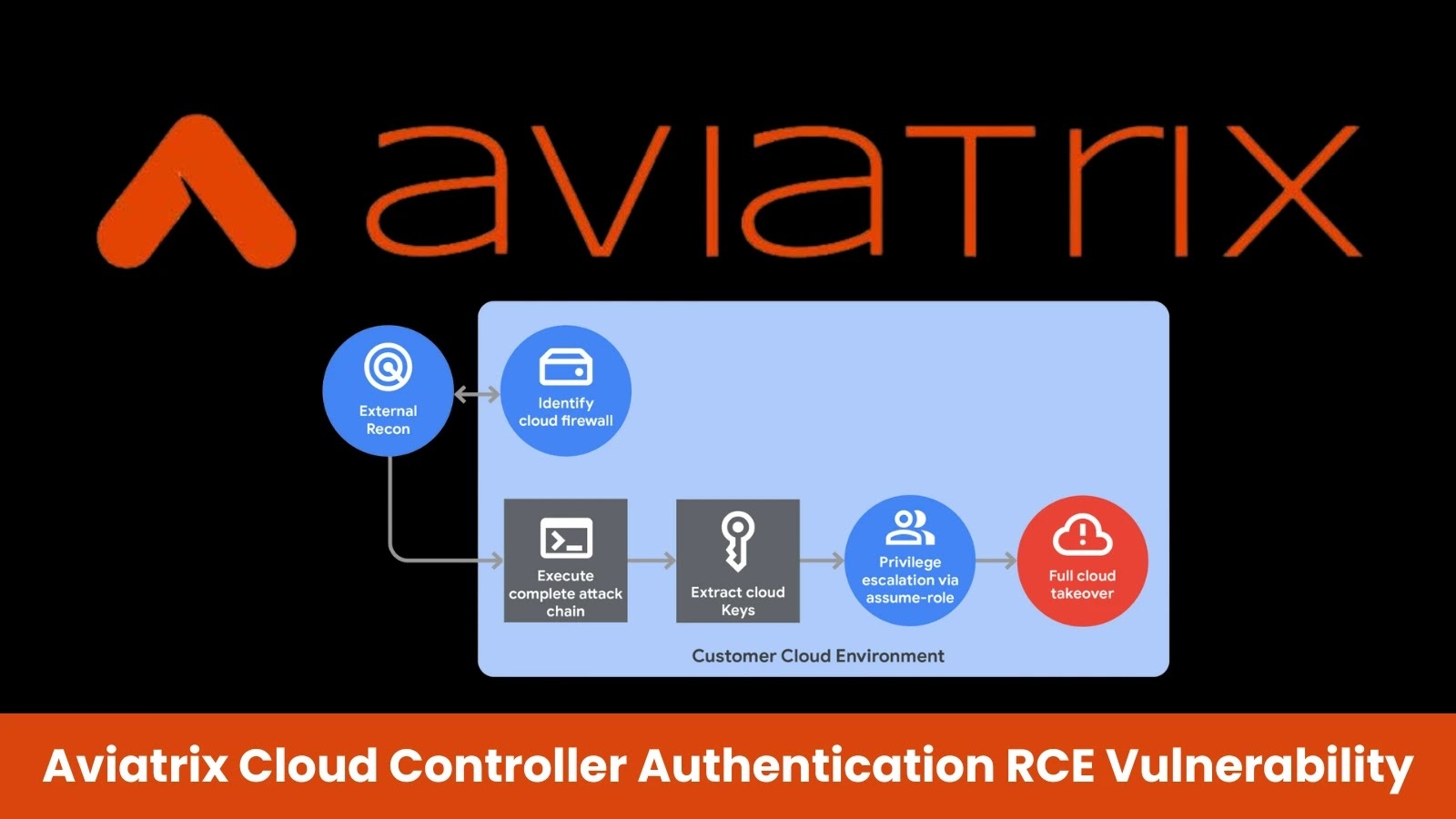
Recent discoveries have unveiled two critical vulnerabilities in the Aviatrix Controller, a pivotal component in cloud networking that facilitates connectivity across various vendors and regions. These vulnerabilities, identified as CVE-2025-2171 and CVE-2025-2172, enable attackers to bypass authentication mechanisms and execute remote code with root privileges, thereby jeopardizing entire cloud infrastructures.
Overview of the Vulnerabilities
The Aviatrix Controller serves as a Software-Defined Networking (SDN) utility, providing centralized management for cloud networking solutions. The identified vulnerabilities are:
– CVE-2025-2171: This flaw pertains to an administrator authentication bypass, allowing unauthorized access to the controller’s administrative functions.
– CVE-2025-2172: This issue involves authenticated command injection, enabling attackers to execute arbitrary commands with elevated privileges.
These vulnerabilities were present in Aviatrix Controller versions 7.2.5012 and earlier.
Detailed Analysis of the Exploits
During a comprehensive security assessment, researchers from Mandiant uncovered that the authentication bypass (CVE-2025-2171) could be exploited through a deficient password reset mechanism. The system generated six-digit password reset tokens within a range of 111,111 to 999,999, resulting in only 888,888 unique combinations. Given a 15-minute validity period for each token, attackers could feasibly brute-force the administrator account in approximately 16 hours and 23 minutes of continuous attempts.
Upon gaining initial access, the researchers identified a command injection vulnerability (CVE-2025-2172) within the file upload functionality. The system’s `upload_file()` function permitted attackers to manipulate partial filenames, including the insertion of tab characters, which could be exploited to smuggle command-line arguments.
The vulnerability exploited the `shlex.split()` function used by the system to tokenize command strings. By uploading files with specially crafted names containing tab characters, attackers could inject additional arguments into shell commands. For instance, a filename like `foobar.foo{TAB}–bar{TAB}–baz` would be tokenized as separate command arguments.
Researchers demonstrated the exploit by targeting the Proxy Admin utility’s CA certificate installation feature, which utilized the `cp` command to copy uploaded files. Through meticulous argument injection, they overwrote `/etc/crontab` with malicious content, achieving persistent root access.
Potential Impact on Cloud Environments
The successful exploitation of these vulnerabilities grants attackers centralized control over cloud gateways and APIs, potentially leading to a complete takeover of the cloud environment. This level of access can result in unauthorized data exfiltration, deployment of malicious software, and disruption of cloud services.
Mitigation Measures and Recommendations
In response to these critical vulnerabilities, Aviatrix has released security patches for versions 8.0.0, 7.2.5090, and 7.1.4208, addressing the issues present in Controller versions 7.2.5012 and earlier.
Organizations utilizing Aviatrix Controller are strongly advised to:
1. Update Immediately: Apply the latest security patches to mitigate the identified vulnerabilities.
2. Review Access Controls: Assess and strengthen authentication mechanisms to prevent unauthorized access.
3. Monitor Systems: Implement continuous monitoring to detect any unusual activities indicative of exploitation attempts.
4. Conduct Security Audits: Regularly perform security assessments to identify and remediate potential vulnerabilities within the cloud infrastructure.
By proactively addressing these vulnerabilities, organizations can safeguard their cloud environments against potential threats and ensure the integrity and security of their data and services.