Critical React and Next.js Vulnerability Exposes Applications to Remote Code Execution
A critical security vulnerability, identified as CVE-2025-55182, has been discovered in React Server Components (RSC) and Next.js frameworks, posing a significant risk of remote code execution (RCE) to web applications. This flaw, carrying a maximum CVSS score of 10.0, affects React versions 19.0.0 through 19.2.0 and Next.js versions 15.x and 16.x utilizing the App Router. Even applications that do not explicitly implement server functions are vulnerable if they support RSC.
Vulnerability Details
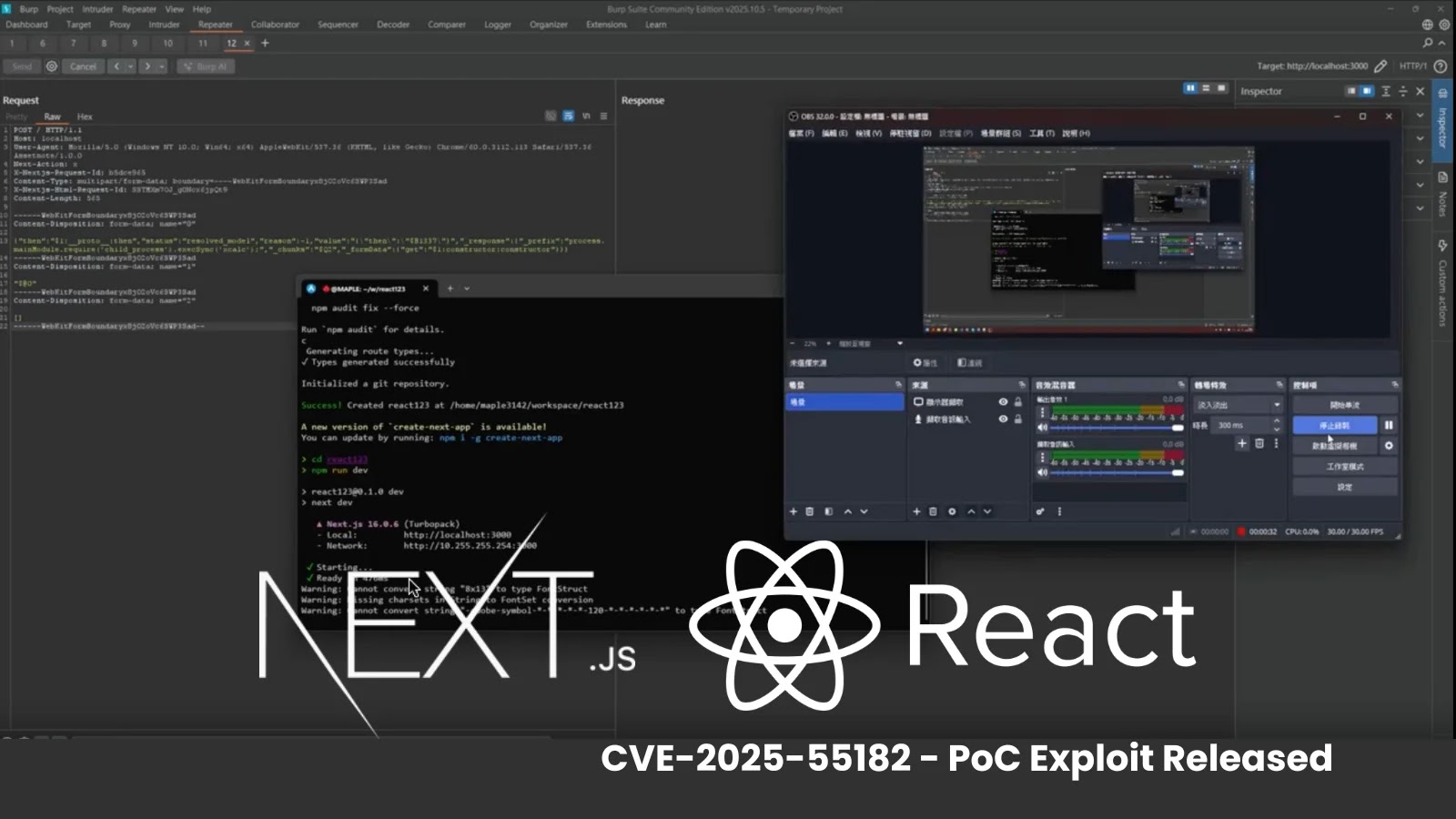
The root cause of this vulnerability lies in insecure deserialization within the RSC Flight protocol. Maliciously crafted payloads can exploit this flaw to manipulate object prototypes and hijack server-side execution. Security researcher @maple3142 demonstrated the exploit by sending a multipart HTTP request that injects a Node.js payload, resulting in the execution of arbitrary code on the target server without authentication. In a proof-of-concept (PoC) demonstration, the exploit triggered the opening of a calculator application on a Linux server, illustrating the potential impact of this vulnerability.
Discovery and Disclosure
The vulnerability was discovered by Lachlan Davidson and responsibly disclosed to Meta and Vercel on November 29, 2025. Following the disclosure, the issue was made public on December 3, prompting swift action from the development community. A new scanner tool was also introduced to identify vulnerable endpoints on networks affected by CVE-2025-55182.
Exploitation and Impact
Within hours of the public disclosure, Amazon’s threat intelligence reported exploitation attempts by groups such as Earth Lamia, indicating active targeting of this vulnerability. Wiz Research estimates that approximately 39% of cloud environments host vulnerable instances, highlighting the widespread nature of the risk. Palo Alto Networks’ Unit 42 confirmed that the attack requires only a crafted POST request to RSC endpoints, achieving near-100% reliability in tests. The simplicity of the exploit amplifies the risk, especially in production environments where default configurations may be vulnerable.
Mitigation and Recommendations
React has released patches in versions 19.0.1, 19.1.2, and 19.2.1 of the react-server-dom packages to address this vulnerability. Next.js has also issued hardened releases across supported branches. Developers are strongly urged to upgrade React, Next.js, and all related RSC-enabled dependencies immediately. Hosting provider mitigations may reduce risk but are not a replacement for patching. Until systems are fully updated, any exposed React Server Component deployment should be treated as high-risk for compromise.
Conclusion
This incident underscores the critical importance of promptly addressing security vulnerabilities in web development frameworks. The ease of exploitation and the potential for significant impact make it imperative for developers and organizations to take immediate action to secure their applications against CVE-2025-55182.