Critical React and Next.js Vulnerability Exposes Servers to Remote Code Execution
A critical security vulnerability, identified as CVE-2025-55182, has been discovered in React Server Components (RSC) and the Next.js framework, potentially allowing unauthenticated remote attackers to execute arbitrary code on affected servers. This flaw, carrying the highest severity rating with a CVSS score of 10.0, poses a significant threat to web applications utilizing these technologies.
Understanding the Vulnerability
The root cause of CVE-2025-55182 lies in insecure deserialization within the React Server Components’ Flight protocol. This protocol facilitates communication between the client and server, and the vulnerability arises from improper handling of serialized data. By crafting malicious payloads, attackers can exploit this flaw to execute arbitrary code on the server without requiring authentication.
Affected Versions
The vulnerability impacts the following versions:
– React: Versions 19.0.0 through 19.2.0.
– Next.js: Versions 15.x and 16.x that utilize the App Router.
Notably, applications that support React Server Components are vulnerable, even if they do not explicitly implement server functions.
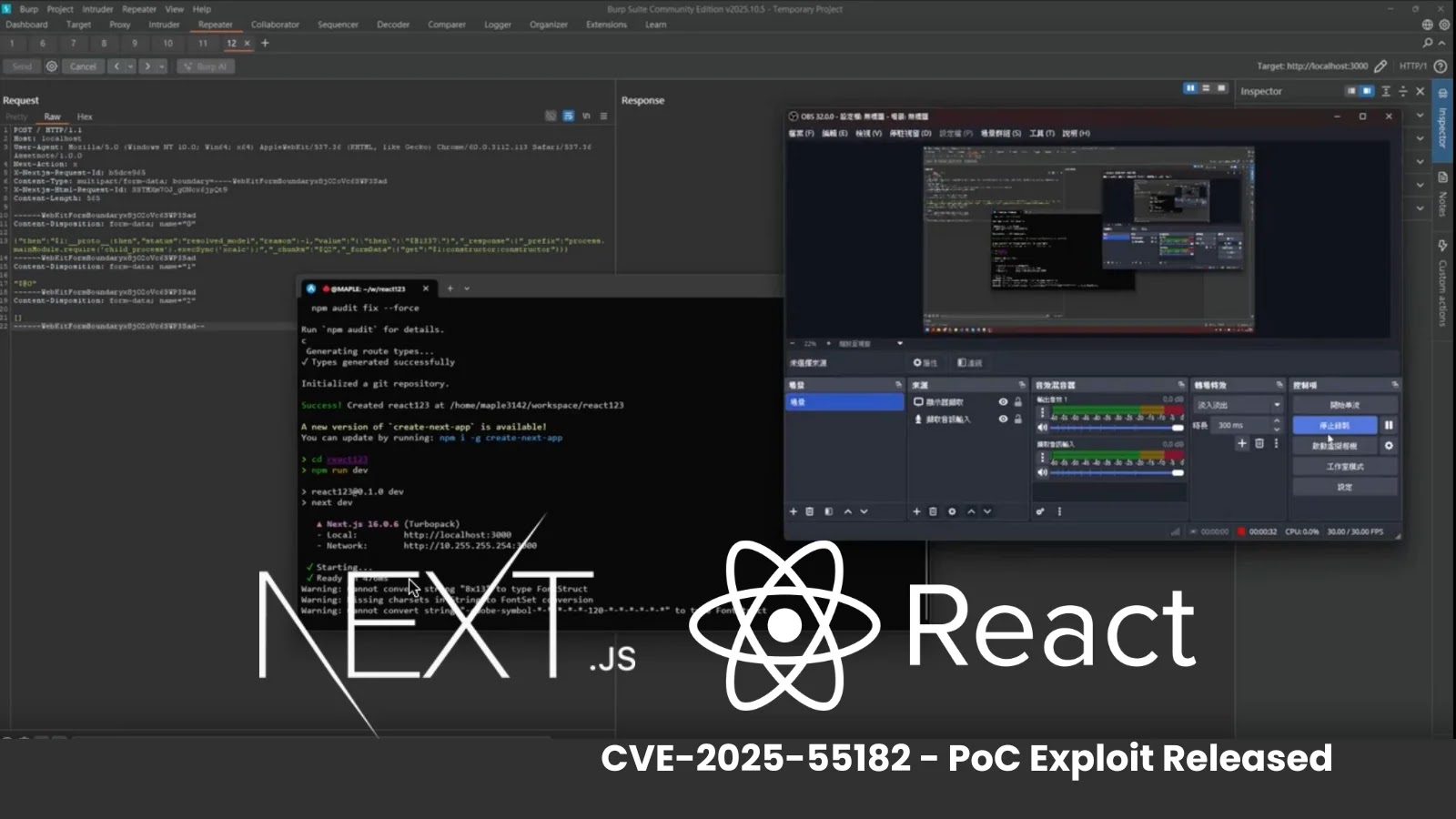
Proof-of-Concept Exploit
Security researcher @maple3142 publicly demonstrated a proof-of-concept (PoC) exploit for this vulnerability. The demonstration involved sending a specially crafted multipart HTTP request containing a Node.js payload. This payload, when processed by a vulnerable server, executed a child process that launched a calculator application on a Linux system, illustrating the potential for remote code execution without authentication.
The exploit leverages the React Flight protocol to bypass serialization safeguards. Techniques such as using Blob references labeled $B1337 were employed to manipulate the deserialization process, effectively hijacking server-side execution.
Discovery and Disclosure
The vulnerability was discovered by security researcher Lachlan Davidson and responsibly disclosed to Meta (the maintainers of React) and Vercel (the creators of Next.js) on November 29, 2025. Following the disclosure, the issue was made public on December 3, 2025, prompting swift action from the development communities to address the flaw.
Exploitation in the Wild
Shortly after the public disclosure, Amazon’s threat intelligence team reported exploitation attempts by threat actors, including groups like Earth Lamia, which are believed to have ties to China. These attempts underscore the urgency for developers and organizations to address this vulnerability promptly.
Scope of Impact
Wiz Research conducted a scan of over 968,000 servers and estimated that approximately 39% of cloud environments host instances vulnerable to CVE-2025-55182. This statistic highlights the widespread nature of the issue and the potential for significant impact if not remediated.
Mitigation and Remediation
To protect against potential exploitation, developers and organizations are strongly advised to take the following actions:
1. Upgrade React: Update to version 19.2.1 or later, where the vulnerability has been patched.
2. Upgrade Next.js: Apply the latest updates provided by the Next.js team, which include fixes for this issue.
3. Audit Deployments: Review all deployments to identify instances of React Server Components and ensure they are updated accordingly.
4. Monitor for Anomalies: Implement monitoring to detect unusual activities that may indicate exploitation attempts.
Conclusion
The discovery of CVE-2025-55182 serves as a stark reminder of the critical importance of secure deserialization practices in web development. The rapid public disclosure and subsequent exploitation attempts highlight the need for prompt action to secure affected systems. Developers and organizations must prioritize updating their React and Next.js deployments to mitigate the risks associated with this vulnerability.