A significant security vulnerability has been identified in One Identity’s OneLogin Identity and Access Management (IAM) solution, potentially exposing sensitive OpenID Connect (OIDC) application client secrets. This flaw, designated as CVE-2025-59363, carries a Common Vulnerability Scoring System (CVSS) score of 7.7 out of 10, indicating a high severity level. The issue arises from improper resource transfer between security domains, allowing unauthorized access to confidential data and functions.
Technical Details of the Vulnerability
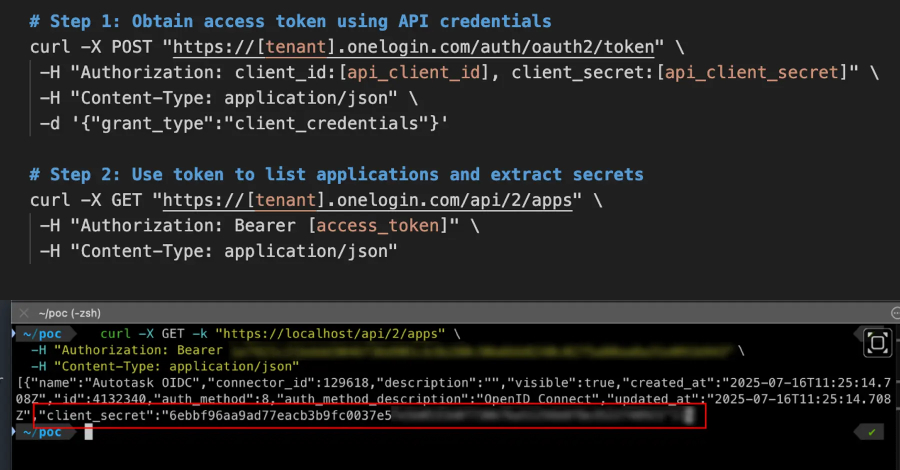
The core of this vulnerability lies in the misconfiguration of the application listing endpoint, specifically `/api/2/apps`. This endpoint was inadvertently set to return more information than necessary, including `client_secret` values alongside application metadata. As a result, attackers possessing valid OneLogin API credentials could exploit this misconfiguration to enumerate and retrieve client secrets for all OIDC applications within an organization’s OneLogin tenant.
Exploitation Process
An attacker could exploit this vulnerability through the following steps:
1. Authentication: Utilize valid OneLogin API credentials (client ID and secret) to authenticate.
2. Access Token Acquisition: Request an access token.
3. Application Enumeration: Call the `/api/2/apps` endpoint to list all applications.
4. Data Extraction: Parse the response to retrieve `client_secret` values for all OIDC applications.
5. Application Impersonation: Use the extracted client secrets to impersonate applications and access integrated services.
Potential Impact
Successfully exploiting this flaw would enable an attacker with valid OneLogin API credentials to retrieve client secrets for all OIDC applications configured within a OneLogin tenant. With these secrets, the attacker could impersonate applications, gaining unauthorized access to other integrated services and facilitating lateral movement within the organization’s network.
Contributing Factors
Several factors exacerbate the risk associated with this vulnerability:
– Broad API Key Access: OneLogin’s role-based access control (RBAC) grants API keys extensive access across various endpoints. Consequently, compromised credentials could be used to access sensitive endpoints throughout the platform.
– Absence of IP Allowlisting: The lack of IP address allowlisting means that attackers can exploit this vulnerability from any location globally, increasing the potential attack surface.
Remediation and Response
Upon responsible disclosure of the vulnerability on July 18, 2025, OneLogin addressed the issue in version 2025.3.0, released in September 2025. The update ensures that OIDC `client_secret` values are no longer visible through the affected endpoint. To date, there is no evidence suggesting that this vulnerability has been exploited in the wild.
Broader Implications
This incident underscores the critical role of identity providers in enterprise security architectures. Vulnerabilities within these systems can have cascading effects across entire technology stacks, emphasizing the necessity for rigorous API security measures.
Recommendations for Organizations
Organizations utilizing OneLogin should take the following steps to mitigate potential risks:
1. Immediate Update: Upgrade to OneLogin version 2025.3.0 or later to ensure the vulnerability is patched.
2. Credential Management: Rotate all API credentials to invalidate any potentially compromised keys.
3. Access Controls: Implement IP allowlisting to restrict API access to trusted sources.
4. Monitoring and Logging: Enhance monitoring of API usage and maintain comprehensive logs to detect any unauthorized access attempts.
5. Security Training: Educate development and security teams on secure API practices to prevent similar vulnerabilities in the future.
Conclusion
The discovery and remediation of CVE-2025-59363 highlight the importance of continuous vigilance and proactive security measures in identity and access management solutions. Organizations must prioritize the security of their IAM systems to protect against potential breaches and maintain the integrity of their digital environments.