Critical Notepad++ Vulnerability Allows Attackers to Hijack Updates and Install Malware
Notepad++, a widely used text editor among developers and IT professionals, has recently addressed a significant security vulnerability in its update mechanism. This flaw could have allowed attackers to intercept network traffic and deliver malicious executables disguised as legitimate updates.
Discovery of the Vulnerability
Security researchers identified unusual traffic patterns associated with WinGUp, the built-in updater for Notepad++. Investigations revealed that update requests were, in some instances, being redirected to malicious servers. Instead of downloading authentic Notepad++ installers, the updater retrieved compromised binaries, effectively creating a covert channel for malware distribution.
Technical Details
An internal review uncovered a flaw in how WinGUp validated the integrity and authenticity of downloaded update files. Under specific conditions, if an attacker could intercept or manipulate the network traffic between the Notepad++ updater and the official update servers, they could exploit this weakness to replace the legitimate installer with a rogue binary. Consequently, the updater could be deceived into downloading and executing malware, all while appearing to perform a routine software update. This type of attack aligns with classic man-in-the-middle or traffic-hijacking techniques often seen in supply-chain and update-channel compromises.
Security Enhancements in the Latest Release
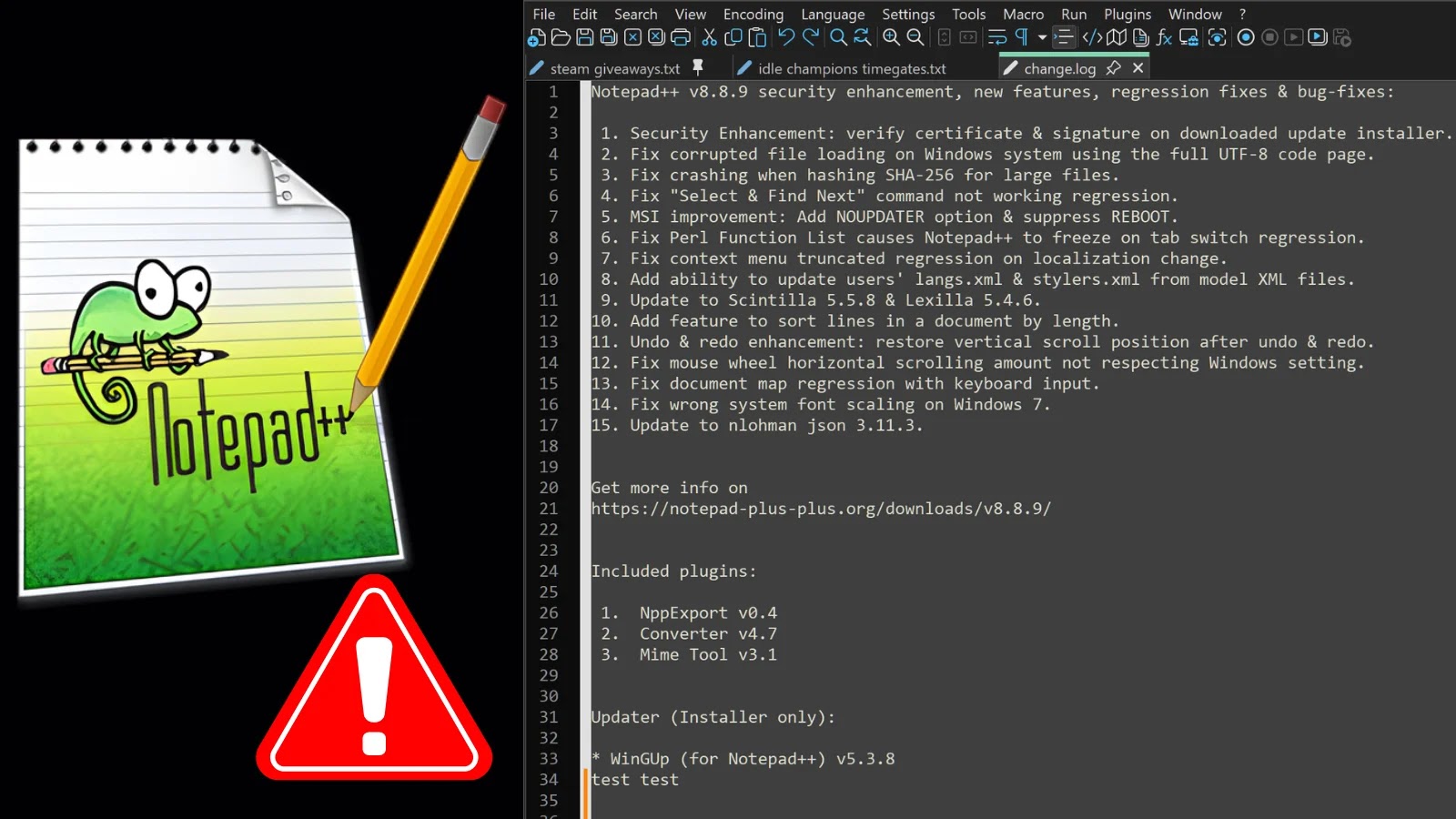
To mitigate this issue, the latest Notepad++ release introduces stricter verification during the update process. Both Notepad++ and WinGUp have been enhanced to verify the digital signature and certificate of downloaded installers before proceeding. If the signature or certificate check fails, the update process is immediately aborted, preventing the execution of untrusted code.
Starting with version 8.8.7, all Notepad++ binaries, including the installer, are digitally signed using a legitimate certificate issued by GlobalSign. This change eliminates the need for users to install a custom Notepad++ root certificate. The project now recommends that any previously installed Notepad++ root certificates be removed to reduce unnecessary trust anchors.
Recommendations for Users
Users are strongly advised to upgrade to the latest release and obtain installers only from the official Notepad++ website. The new version 8.8.9 packages these security improvements alongside several bug fixes and additional enhancements. By updating to the latest version, users can ensure they are protected against potential exploits targeting this vulnerability.
Broader Implications
This incident underscores the importance of securing software update mechanisms. Attackers often target these channels to distribute malware, as they provide a trusted pathway into users’ systems. Ensuring the integrity and authenticity of updates is crucial in maintaining the security of software applications.
In conclusion, the prompt response by the Notepad++ development team in addressing this vulnerability highlights the ongoing need for vigilance in software security. Users are encouraged to stay informed about security updates and to apply them promptly to protect their systems from potential threats.