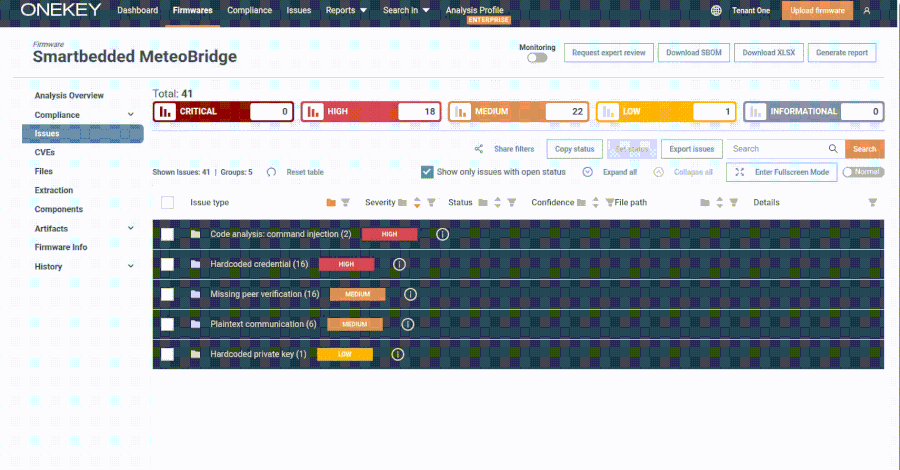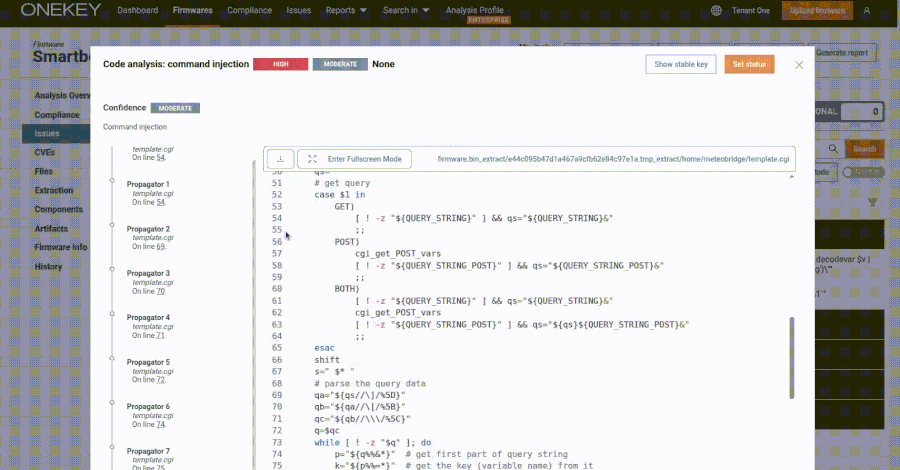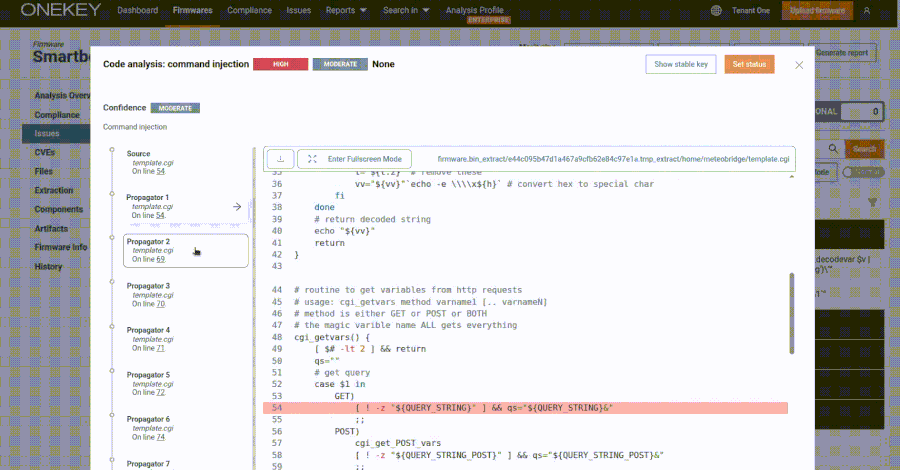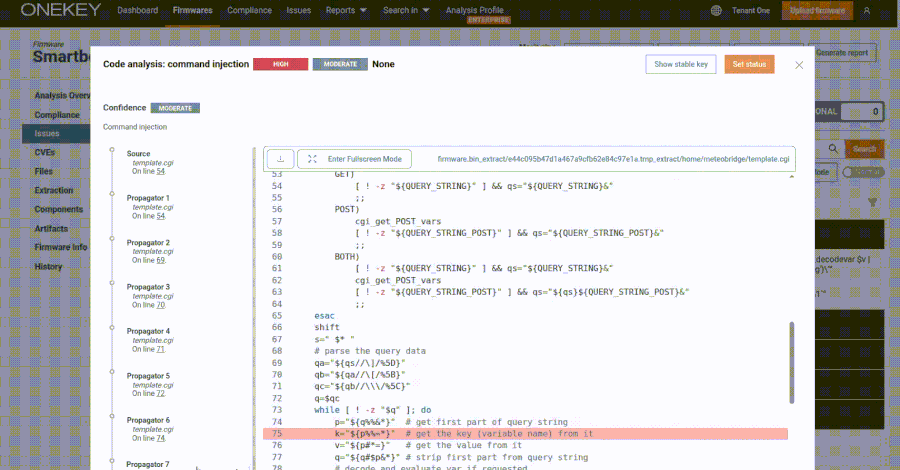
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently added a significant security vulnerability affecting Smartbedded’s Meteobridge devices to its Known Exploited Vulnerabilities (KEV) catalog, indicating active exploitation in the wild. This vulnerability, identified as CVE-2025-4008 with a CVSS score of 8.7, involves a command injection flaw within the Meteobridge web interface, potentially allowing unauthenticated remote attackers to execute arbitrary commands with root privileges on compromised devices.
Understanding the Vulnerability
Meteobridge devices are utilized by weather enthusiasts and professionals to collect and manage weather station data. The web interface of these devices enables administrators to oversee data collection and system control through a web application composed of CGI shell scripts and C programming. The vulnerability resides in the template.cgi script, accessible via /cgi-bin/template.cgi, which improperly handles user input due to insecure use of eval calls. This flaw allows attackers to craft specific requests that can execute arbitrary code on the device.
Security researcher Quentin Kaiser from ONEKEY, who discovered and reported the issue in late February 2025, demonstrated the exploitability of this vulnerability. By sending a specially crafted GET request, an attacker can execute commands on the device without authentication. For example, using the following curl command:
“`bash
curl -i -u meteobridge:meteobridge \
‘https://192.168.88.138/cgi-bin/template.cgi?$(id>/tmp/a)=whatever’
“`
This command injects and executes the ‘id’ command, redirecting its output to a file named ‘a’ in the ‘/tmp’ directory. The lack of authentication requirements for accessing the CGI script exacerbates the risk, as it is hosted in a public directory. Consequently, attackers can exploit this vulnerability remotely, even through malicious web pages, by embedding image tags with the source set to the vulnerable URL.
Implications of the Exploit
The exploitation of CVE-2025-4008 poses significant risks, including unauthorized access to sensitive weather data, potential manipulation of device settings, and the possibility of using compromised devices as entry points for broader network attacks. Given the elevated privileges obtained through this exploit, attackers could execute commands that may disrupt device functionality or exfiltrate data.
Mitigation Measures
In response to the discovery, Smartbedded released Meteobridge version 6.2 on May 13, 2025, addressing the vulnerability. Users are strongly advised to update their devices to this latest version to mitigate the risk of exploitation. The update can be obtained through the official Meteobridge website or by following the device’s update procedures.
CISA’s Advisory and Broader Context
CISA’s inclusion of CVE-2025-4008 in its KEV catalog underscores the severity of the vulnerability and the necessity for immediate action. Federal Civilian Executive Branch (FCEB) agencies are mandated to apply the necessary updates by October 23, 2025, to ensure optimal protection against potential threats.
In addition to CVE-2025-4008, CISA has added several other vulnerabilities to the KEV catalog, highlighting the ongoing challenges in cybersecurity:
– CVE-2025-21043: An out-of-bounds write vulnerability in Samsung mobile devices’ ‘libimagecodec.quram.so’ library, potentially allowing remote code execution.
– CVE-2017-1000353: A deserialization of untrusted data vulnerability in Jenkins, enabling unauthenticated remote code execution.
– CVE-2015-7755: An improper authentication vulnerability in Juniper ScreenOS, allowing unauthorized remote administrative access.
– CVE-2014-6278 (Shellshock): An OS command injection vulnerability in GNU Bash, permitting remote attackers to execute arbitrary commands via crafted environment variables.
Recommendations for Users
To protect against potential exploits, users of Meteobridge devices should:
1. Update Devices Promptly: Ensure that Meteobridge devices are updated to version 6.2 or later to patch the vulnerability.
2. Restrict Access: Limit access to the Meteobridge web interface to trusted networks and users.
3. Monitor Network Traffic: Regularly review network logs for unusual activity that may indicate exploitation attempts.
4. Implement Strong Authentication: If possible, configure authentication mechanisms to restrict access to the web interface.
5. Stay Informed: Keep abreast of security advisories from CISA and other reputable sources to remain aware of emerging threats and vulnerabilities.
Conclusion
The active exploitation of CVE-2025-4008 in Meteobridge devices highlights the critical importance of timely software updates and vigilant security practices. By addressing vulnerabilities promptly and adhering to recommended security measures, users can significantly reduce the risk of unauthorized access and potential damage to their systems.