In a recent disclosure, Google has revealed that the Chinese state-sponsored cyber threat group known as APT41 has been utilizing a sophisticated malware named TOUGHPROGRESS to exploit Google Calendar for command-and-control (C2) operations. This activity, detected in late October 2024, involved the malware being hosted on a compromised government website and subsequently targeting multiple other governmental entities.
APT41, also recognized by aliases such as Axiom, Blackfly, Brass Typhoon (formerly Barium), Bronze Atlas, Earth Baku, HOODOO, Red Kelpie, TA415, Wicked Panda, and Winnti, is notorious for its extensive cyber-espionage campaigns. Their targets span various sectors, including government agencies, global shipping and logistics, media and entertainment, technology, and automotive industries.
The attack sequence initiated with spear-phishing emails containing links to a ZIP archive hosted on the compromised government website. This ZIP file comprised a directory and a Windows shortcut (LNK) file masquerading as a PDF document. The directory appeared to contain seven images of arthropods, labeled from 1.jpg to 7.jpg.
Upon execution of the LNK file, a decoy PDF was displayed to the recipient, indicating that the species depicted in the images required declaration for export. Notably, the files 6.jpg and 7.jpg were counterfeit images.
The infection process unfolded in a multi-stage manner:
1. PLUSDROP: This DLL decrypted and executed the subsequent stage in memory.
2. PLUSINJECT: It launched and performed process hollowing on a legitimate svchost.exe process to inject the final payload.
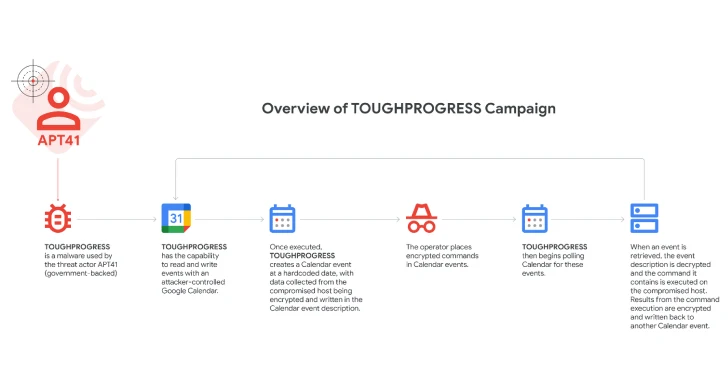
3. TOUGHPROGRESS: The primary malware that leveraged Google Calendar for C2 operations.
TOUGHPROGRESS was engineered to interact with an attacker-controlled Google Calendar, creating zero-minute events on a hard-coded date (May 30, 2023) to store harvested data within the event descriptions. The attackers embedded encrypted commands in Calendar events dated July 30 and 31, 2023. The malware would poll these events, decrypt the commands, execute them on the compromised Windows host, and write the results back to another Calendar event, from which the attackers could retrieve the data.
Google has taken decisive actions to neutralize this campaign by removing the malicious Google Calendar and terminating the associated Workspace projects. Affected organizations have been duly notified. The exact scale of this campaign remains undetermined.
This incident underscores a broader trend of threat actors misusing legitimate cloud services for malicious purposes. By leveraging trusted platforms like Google Calendar, attackers can blend their activities with normal network traffic, thereby evading detection. Such tactics highlight the evolving sophistication of cyber threats and the necessity for organizations to implement robust security measures.
APT41’s history of exploiting legitimate tools and services is well-documented. In previous campaigns, the group has utilized open-source red teaming tools like Google Command and Control (GC2) to target media and job sites. They have also employed advanced malware such as MoonBounce, a UEFI firmware-based rootkit, to maintain persistent access to compromised systems.
The group’s ability to rapidly adapt and integrate new techniques into their operations poses a significant challenge to cybersecurity defenses worldwide. Their activities emphasize the importance of continuous monitoring, threat intelligence sharing, and the development of advanced detection mechanisms to counteract such sophisticated adversaries.
Organizations are advised to remain vigilant against spear-phishing attempts and to scrutinize unexpected emails containing links or attachments. Implementing multi-layered security protocols, conducting regular security audits, and educating employees about the latest cyber threats are crucial steps in mitigating the risks posed by groups like APT41.
In conclusion, the exploitation of Google Calendar by APT41 for C2 operations represents a significant evolution in cyber-espionage tactics. It highlights the need for a proactive and comprehensive approach to cybersecurity, emphasizing the detection and prevention of such sophisticated attacks.