Unveiling DKnife: China’s Advanced Router-Based Cyber Espionage Framework
In the ever-evolving landscape of cyber threats, a sophisticated adversary-in-the-middle (AitM) framework named DKnife has emerged, operated by China-linked threat actors since at least 2019. This Linux-based toolkit is engineered to infiltrate routers and edge devices, enabling deep packet inspection, traffic manipulation, and malware delivery. Its primary targets appear to be Chinese-speaking users, as evidenced by credential-harvesting phishing pages for Chinese email services and modules designed to exfiltrate data from popular Chinese applications like WeChat.
The Architecture of DKnife
DKnife’s modular design comprises seven distinct components, each serving a specific function:
1. dkknife.bin: Acts as the core, responsible for deep packet inspection, user activity reporting, binary download hijacking, and DNS hijacking.
2. postapi.bin: Functions as a data relay, receiving traffic from DKnife and forwarding it to remote command-and-control (C2) servers.
3. sslmm.bin: A modified reverse proxy module derived from HAProxy, it performs TLS termination, email decryption, and URL rerouting.
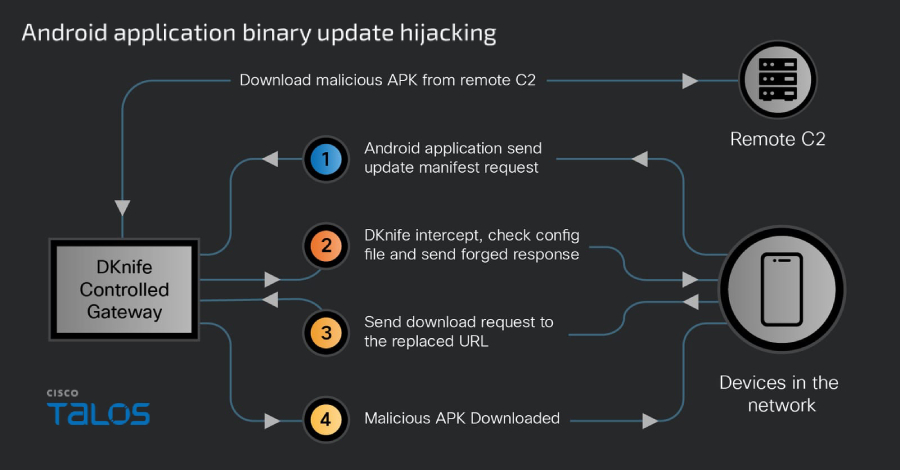
4. mmdown.bin: An updater module that connects to hard-coded C2 servers to download malicious APKs used in attacks.
5. yitiji.bin: Creates a bridged TAP interface on the router to host and route attacker-injected LAN traffic.
6. remote.bin: Establishes a peer-to-peer VPN client module, creating a communication channel to remote C2 servers.
7. dkupdate.bin: Serves as an updater and watchdog, ensuring the continuous operation of the various components.
Operational Tactics and Techniques
DKnife’s capabilities are extensive and alarming. By compromising routers and edge devices, it can intercept and manipulate network traffic, allowing attackers to:
– Hijack Binary Downloads: Intercept legitimate software downloads and replace them with malicious versions, leading to widespread malware distribution.
– DNS Hijacking: Redirect users to malicious websites by altering DNS responses, facilitating phishing attacks and further malware dissemination.
– Credential Harvesting: Decrypt and inspect email communications to steal login credentials, particularly targeting major Chinese email providers.
– Malware Delivery: Deploy and manage backdoors like ShadowPad and DarkNimbus by hijacking binary downloads and Android application updates.
Connections to Other Threat Actors
The infrastructure and operational patterns of DKnife suggest links to other China-aligned advanced persistent threat (APT) groups. Notably, an IP address associated with DKnife was found hosting WizardNet, a Windows implant deployed by TheWizards via an AitM framework known as Spellbinder. This overlap indicates potential collaboration or shared resources among these groups, enhancing their capabilities and reach.
Implications for Cybersecurity
The emergence of DKnife underscores the growing sophistication of cyber espionage tools targeting network infrastructure. By compromising routers and edge devices, attackers can gain a foothold in networks, intercept sensitive communications, and deploy malware with alarming efficiency. This approach not only broadens the attack surface but also complicates detection and mitigation efforts.
Mitigation Strategies
To defend against threats like DKnife, organizations should implement comprehensive security measures, including:
– Regular Firmware Updates: Ensure that routers and edge devices are updated with the latest firmware to patch known vulnerabilities.
– Network Segmentation: Divide networks into segments to limit the spread of malware and unauthorized access.
– Intrusion Detection Systems (IDS): Deploy IDS to monitor network traffic for signs of malicious activity.
– Encrypted Communications: Utilize encrypted protocols for all communications to prevent interception and manipulation.
– User Education: Train users to recognize phishing attempts and the importance of secure practices.
Conclusion
DKnife represents a significant advancement in cyber espionage tactics, highlighting the need for heightened vigilance and robust security measures. As threat actors continue to evolve, so must our defenses to protect critical infrastructure and sensitive information from sophisticated attacks.