Navigating the Complexities of Trusted Open Source: Insights from Chainguard’s Latest Report
In the rapidly evolving landscape of open-source software, understanding how organizations utilize and manage these resources is crucial. Chainguard, a leading authority in open-source security, has released The State of Trusted Open Source, a comprehensive quarterly analysis shedding light on current trends, risks, and operational challenges within the open-source ecosystem.
Key Findings from the Report:
1. AI’s Influence on the Open Source Stack:
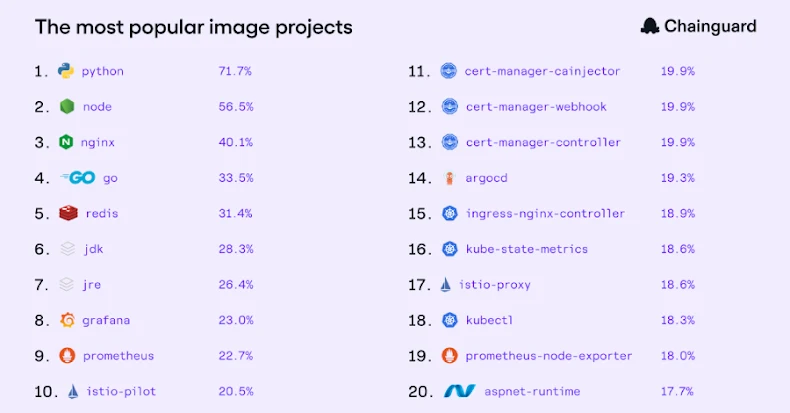
Python has emerged as the predominant open-source image among Chainguard’s global clientele, underscoring its pivotal role in the modern AI infrastructure. Its versatility makes it indispensable for tasks ranging from model development to data pipeline management and production inference services.
2. Beyond the Popular Projects:
While many teams standardize on a familiar set of images, real-world infrastructure relies on a diverse array of projects. Notably, over half of production activities occur outside the top 20 most popular projects, referred to as longtail images in the report. This highlights the extensive and varied nature of open-source utilization in production environments.
3. Risk Distribution Across Projects:
A striking 98% of vulnerabilities identified and addressed in Chainguard images were found in projects beyond the top 20. This indicates that significant security challenges often reside in less prominent parts of the software stack, where implementing patches can be more complex and resource-intensive.
4. Compliance as a Driving Force:
Regulatory requirements, such as Software Bill of Materials (SBOM) mandates and frameworks like PCI DSS, SOC 2, and the EU’s Cyber Resilience Act, are increasingly influencing software decisions. For instance, 44% of Chainguard customers utilize FIPS-compliant images in production, reflecting the substantial impact of compliance on software deployment strategies.
5. Emphasis on Rapid Remediation:
The speed of addressing vulnerabilities is critical to maintaining trust. Chainguard demonstrated this by resolving Critical Common Vulnerabilities and Exposures (CVEs) in under 20 hours on average, showcasing their commitment to swift and effective security responses.
Methodology Overview:
The report’s insights are based on an analysis of over 1,800 unique container image projects, encompassing 10,100 vulnerability instances and 154 unique CVEs. The data spans from September 1, 2025, to November 30, 2025, providing a robust foundation for the findings presented.
Detailed Analysis:
1. Production Usage Patterns:
The report reveals that foundational languages, runtimes, and infrastructure components dominate the production container landscape. Python leads with 71.7% of customers utilizing it, followed by Node (56.5%), nginx (40.1%), Go (33.5%), and Redis (31.4%). This trend underscores the critical role these technologies play in building and maintaining modern software infrastructures.
2. Regional Variations in Open Source Adoption:
While the core stack remains consistent globally, regional differences emerge in the adoption of longtail images. In North America, there’s a broad and consistent set of default production building blocks, including Python, Node, nginx, Go, and Redis, along with strong penetration of Kubernetes ecosystem components. Outside North America, the same core stack appears, but the portfolio spreads differently, with noticeable presence of .NET runtimes and PostgreSQL.
3. The Significance of Longtail Images:
Despite the prominence of top images, the longtail—comprising 1,436 images—accounts for 61.42% of the average customer’s container portfolio. This indicates that half of all production workloads rely on these less prominent images, highlighting their essential role in infrastructure. Maintaining security and operational efficiency across this diverse range is crucial for trusted open-source utilization.
4. Compliance as a Catalyst for Action:
Compliance requirements significantly influence software deployment decisions. The report notes that 44% of customers run at least one FIPS-compliant image in production, reflecting the impact of regulatory standards on software choices. This trend underscores the necessity for organizations to align their software practices with evolving compliance mandates.
5. Addressing Vulnerabilities Across the Stack:
The distribution of vulnerabilities is heavily skewed towards longtail images, with 98% of CVEs remediated by Chainguard occurring outside the top 20 projects. This highlights the importance of comprehensive security measures that extend beyond the most popular projects to encompass the entire software stack.
6. The Importance of Remediation Speed:
Timely resolution of vulnerabilities is paramount. Chainguard’s achievement of resolving Critical CVEs in under 20 hours on average demonstrates the value of rapid response in maintaining system integrity and trust.
Conclusion:
The findings from Chainguard’s report emphasize the complexity and breadth of the open-source landscape. Organizations must recognize the significance of both popular and longtail projects in their production environments. By prioritizing comprehensive security practices, aligning with compliance requirements, and ensuring swift vulnerability remediation, businesses can effectively navigate the challenges of trusted open-source software utilization.