Enhancing SOC Efficiency: Addressing Delayed Threat Detection
In today’s digital landscape, the speed at which Security Operations Centers (SOCs) detect and respond to cyber threats is paramount. However, many SOCs are identifying attacks only after significant damage has occurred. The average data breach now costs organizations approximately $4.4 million, with expenses escalating the longer attackers remain undetected within networks. Delayed detection, often measured in days or weeks, transforms preventable incidents into costly crises.
Challenges Leading to Delayed Detection
Several factors contribute to the lag in threat detection:
1. Outdated or Incomplete Threat Intelligence: Public reports often arrive too late, after attackers have shifted to new infrastructures. Many commercial feeds provide indicators without meaningful context, necessitating time-consuming manual verification by analysts.
2. Alert Overload: SOCs can face up to 11,000 alerts daily, with only 19% deemed actionable. This inundation leads to alert fatigue, increased false positives, analyst burnout, and missed threats.
3. Evasion Techniques: Modern malware and phishing campaigns employ sophisticated evasion methods, allowing them to bypass traditional defenses and leaving SOCs reactive rather than proactive.
4. Resource Drain: Overworked teams and inefficient workflows escalate operational costs while increasing the risk of breaches.
The Importance of Real-Time Threat Intelligence
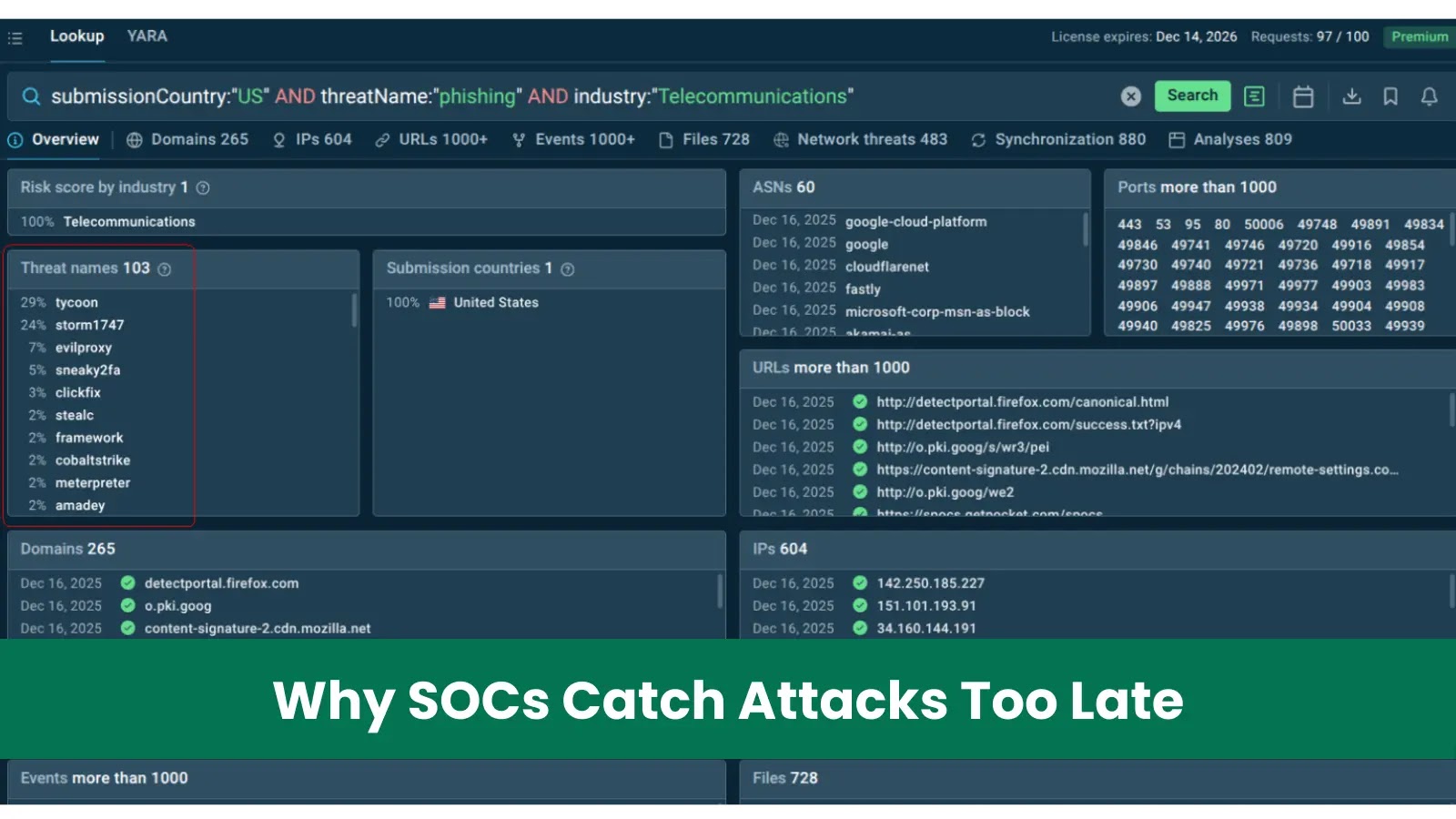
To address these challenges, adopting real-time threat intelligence feeds that deliver verified, contextual indicators as emerging threats are identified is crucial. ANY.RUN’s Threat Intelligence Feeds, for instance, integrate current, verified indicators directly into security stacks like SIEMs, XDR, EDR, and SOAR. This integration offers several benefits:
1. Early Detection of Emerging Attacks: Fresh threat intelligence feeds provide up-to-the-minute Indicators of Compromise (IOCs), including malicious IPs, domains, and URLs sourced from active attacks and sandbox investigations. This enables SOCs to detect threats before they escalate.
2. Reduction in False Positives and Noise: High-quality feeds filter out false positives before reaching analysts. By enriching IOCs with sandbox-verified contextual data, these feeds help SOC teams focus on real risks, reducing wasted labor and associated costs.
3. Faster Triage and Decision-Making: With access to top-tier intelligence, SOC analysts can instantly validate IOCs and understand their context, dramatically shortening Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), thereby reducing exposure and operational impact.
4. Proactive Defense: Real-time intelligence allows SOCs to anticipate and prepare for emerging threats, shifting from a reactive to a proactive security posture.
Implementing Effective Threat Intelligence
To effectively implement real-time threat intelligence, organizations should:
– Integrate Intelligence Feeds: Incorporate real-time threat intelligence feeds into existing security infrastructures to ensure timely and relevant data is available for analysis.
– Automate Alert Triage: Utilize automation tools to handle initial alert triage, allowing analysts to focus on more complex investigations.
– Continuous Training: Provide ongoing training for SOC analysts to stay updated on the latest threat landscapes and detection techniques.
– Collaborate with Peers: Engage in information sharing with other organizations and industry groups to enhance collective defense mechanisms.
Conclusion
In an era where cyber threats are increasingly sophisticated and pervasive, SOCs must evolve to detect and respond to attacks more swiftly. By addressing the root causes of delayed detection and integrating real-time, contextual threat intelligence into their operations, SOCs can enhance their efficiency, reduce financial losses, and better protect their organizations from emerging cyber threats.