BodySnatcher Vulnerability: Unauthenticated Attackers Can Impersonate Any ServiceNow User
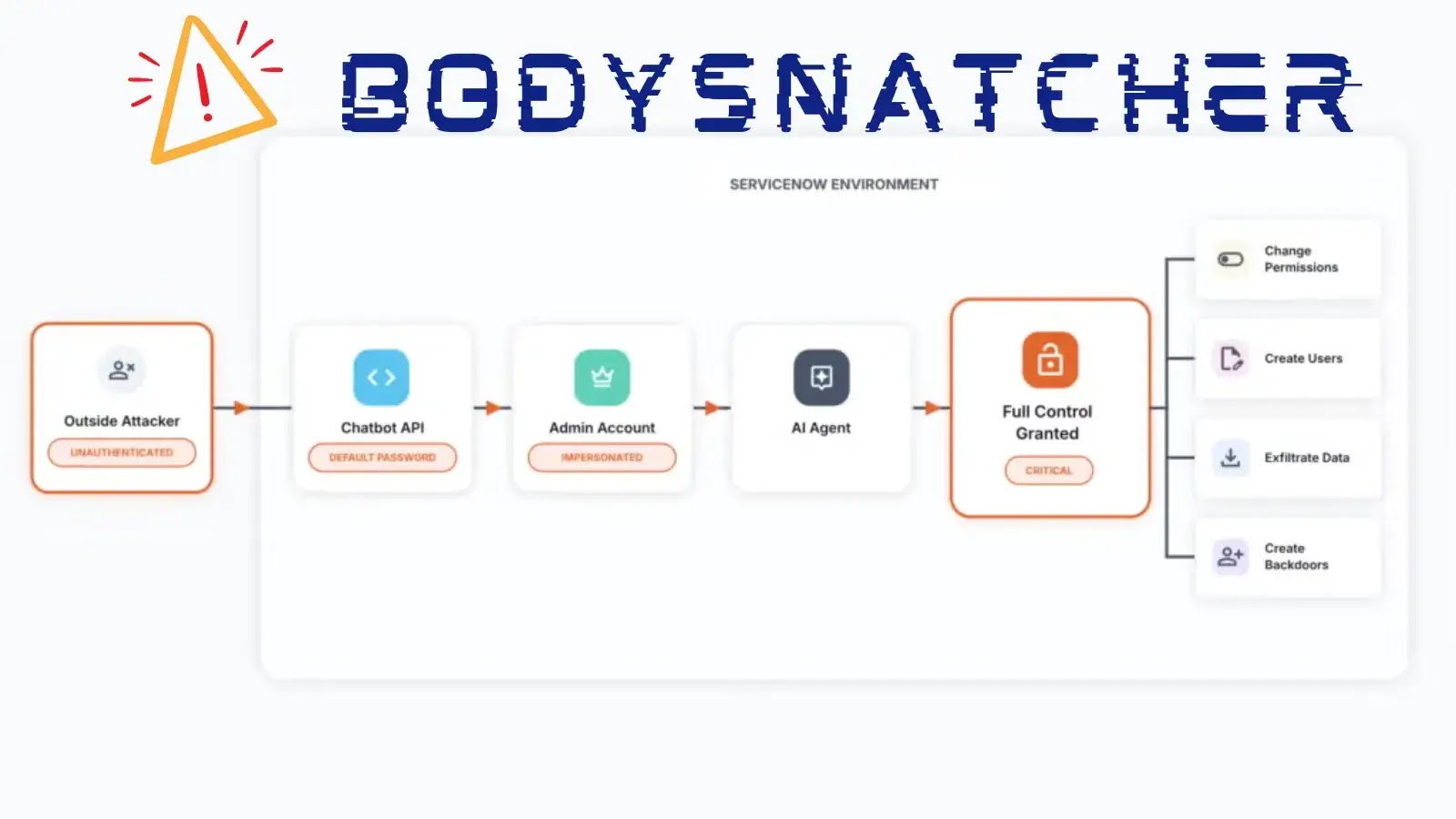
A critical security flaw, designated as CVE-2025-12420 and dubbed BodySnatcher, has been identified in ServiceNow’s Virtual Agent API and Now Assist AI Agents application. This vulnerability enables unauthenticated attackers to impersonate any user, including administrators, and execute privileged AI agents remotely.
Discovery and Disclosure
Security researcher Aaron Costello from AppOmni uncovered this flaw, which combines a hardcoded platform-wide secret with insecure account-linking logic. This combination allows attackers to bypass multi-factor authentication (MFA), single sign-on (SSO), and other access controls. The vulnerability was reported to ServiceNow on October 23, 2025, prompting immediate remediation efforts.
Technical Details
The vulnerability exploits two primary design flaws:
1. Universal Authentication Token: AI agent channel providers were shipped with identical authentication tokens across all customer instances, creating a universal authentication bypass.
2. Insecure Auto-Linking Mechanism: The system trusted any requester supplying the shared token along with a valid email address, automatically associating external entities with ServiceNow accounts without requiring MFA.
By chaining these weaknesses through the Virtual Agent API, attackers can impersonate privileged users and execute AI agents. In proof-of-concept demonstrations, researchers successfully created administrative accounts, assigned elevated privileges, reset passwords, and achieved full platform access without authenticating.
Affected Versions and Patches
The vulnerability affects the following applications and versions:
– Now Assist AI Agents (sn_aia): Versions 5.0.24 – 5.1.17 and 5.2.0 – 5.2.18.
– Virtual Agent API (sn_va_as_service): Versions ≤ 3.15.1 and 4.0.0 – 4.0.3.
ServiceNow addressed the issue by October 30, 2025, deploying patches that rotated provider credentials and removed the powerful Record Management AI agent from customer environments. The company issued customer notifications and published a knowledge base article, KB2587317, crediting Costello and AppOmni with the discovery.
Recommendations for Organizations
Organizations using ServiceNow’s AI-powered automation features should take the following actions:
1. Update Affected Applications: Ensure that Now Assist AI Agents and Virtual Agent API are updated to the fixed versions:
– Now Assist AI Agents: 5.1.18 or later, or 5.2.19 or later.
– Virtual Agent API: 3.15.2 or later, or 4.0.4 or later.
2. Implement Multi-Factor Authentication: Enforce MFA for account-linking processes to add an additional layer of security.
3. Establish Review Workflows: Set up automated review workflows for AI agent deployments to ensure that only authorized agents are active.
4. Audit Dormant AI Agents: Regularly audit and deactivate unused AI agents to minimize potential attack surfaces.
ServiceNow administrators can leverage the AI Control Tower application to identify unused agents and enforce approval processes before production deployment.
Conclusion
The BodySnatcher vulnerability underscores the importance of robust security measures in AI-powered platforms. Organizations must promptly apply patches, enforce strong authentication mechanisms, and continuously monitor their systems to protect against such critical vulnerabilities.