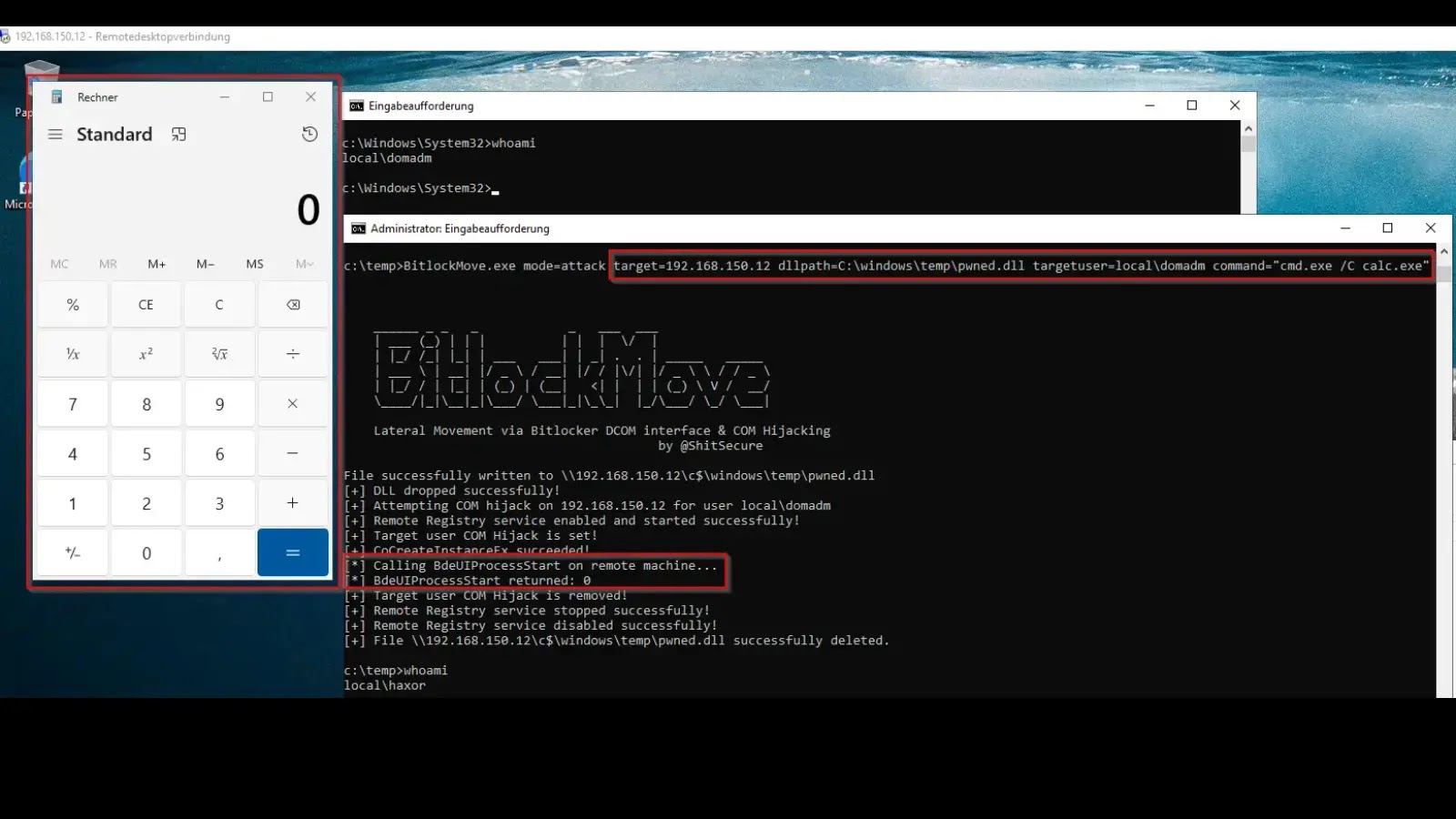
A recent proof-of-concept (PoC) tool named BitlockMove has unveiled a sophisticated lateral movement technique that exploits BitLocker’s Distributed Component Object Model (DCOM) interfaces in conjunction with Component Object Model (COM) hijacking. Developed by security researcher Fabian Mosch from r-tec Cyber Security, this tool enables attackers to execute code on remote systems within the session of an already logged-on user, effectively bypassing the need to steal credentials or impersonate accounts.
Understanding BitlockMove
BitlockMove capitalizes on specific COM classes configured as INTERACTIVE USER, allowing processes to spawn within the current user’s session. If these processes are vulnerable to COM hijacking, an attacker can remotely modify the registry, deliver a malicious Dynamic Link Library (DLL) via Server Message Block (SMB), and trigger its execution through DCOM. This method is particularly stealthy, as the malicious code operates directly within the target user’s context, generating fewer indicators of compromise compared to traditional methods like credential theft from the Local Security Authority Subsystem Service (LSASS).
The PoC specifically targets the `BDEUILauncher Class` (CLSID `ab93b6f1-be76-4185-a488-a9001b105b94`), capable of launching several processes. One such process, `BaaUpdate.exe`, is susceptible to COM hijacking when initiated with specific parameters. The tool hijacks a related BitLocker CLSID (`A7A63E5C-3877-4840-8727-C1EA9D7A4D50`) from the remote system. Given that BitLocker is predominantly enabled on Windows client operating systems, this lateral movement technique is primarily effective against workstations rather than servers.
Operational Modes of BitlockMove
Written in C#, BitlockMove operates in two distinct modes: enumeration and attack.
– Enumeration Mode: This mode allows an attacker to identify active user sessions on a target host, enabling the selection of high-privilege users, such as domain administrators, for subsequent attacks.
– Attack Mode: In this mode, the attacker specifies the target host, the username of the active session, a path to deploy the malicious DLL, and the command to be executed. The tool then performs the remote COM hijack, triggers the payload, and cleans up by removing the hijack from the registry and deleting the DLL.
Detection and Mitigation Strategies
Defenders can detect this technique by monitoring for specific behaviors. Key indicators include the remote COM hijacking of the targeted BitLocker-related CLSID, followed by the `BaaUpdate.exe` process loading a newly deployed DLL from the hijack location. Suspicious subprocesses spawning from `BaaUpdate.exe` or `BdeUISrv.exe` are also strong signs of compromise. Security teams can develop threat hunting queries to detect the presence of the `BdeUISrv.exe` process, as its legitimate use is rare.
The PoC utilizes a hardcoded DLL, making signature-based detection straightforward; however, attackers can easily create custom DLLs to evade such defenses.
Implications for Cybersecurity
The emergence of BitlockMove underscores the evolving sophistication of lateral movement techniques employed by attackers. By leveraging legitimate Windows components like BitLocker’s DCOM interfaces, adversaries can achieve stealthy code execution without the need for credential theft or account impersonation. This approach not only complicates detection but also highlights the necessity for continuous monitoring and advanced threat detection mechanisms within organizational networks.
Recommendations for Organizations
To mitigate the risks associated with such advanced lateral movement techniques, organizations should consider the following measures:
1. Enhanced Monitoring: Implement comprehensive monitoring solutions to detect unusual behaviors associated with COM and DCOM activities, particularly those involving BitLocker-related processes.
2. Regular Audits: Conduct regular audits of system configurations and registry settings to identify and remediate unauthorized modifications that could indicate COM hijacking attempts.
3. User Education: Educate users about the risks of executing unknown or unsolicited files and the importance of reporting suspicious activities to the security team.
4. Patch Management: Ensure that all systems are up-to-date with the latest security patches to minimize vulnerabilities that could be exploited for lateral movement.
5. Access Controls: Implement strict access controls and least privilege principles to limit the potential impact of compromised accounts.
By adopting these proactive measures, organizations can enhance their resilience against sophisticated lateral movement techniques like those demonstrated by BitlockMove.