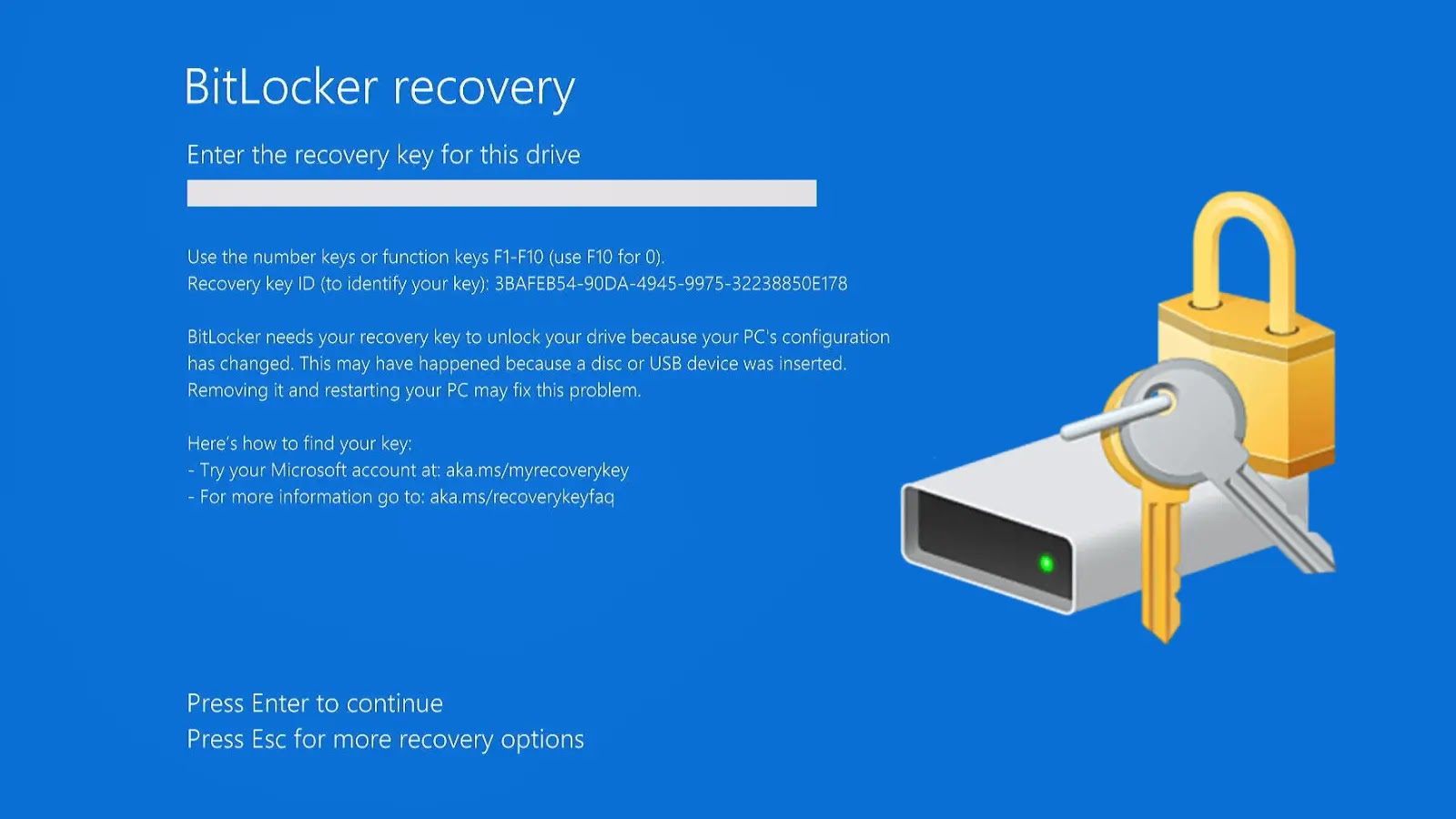
In the digital age, data security is paramount. However, sometimes the very tools designed to protect our information can inadvertently lead to its loss. A recent incident involving Microsoft’s BitLocker encryption feature serves as a stark reminder of this paradox.
The Unintended Encryption Dilemma
A Reddit user recently recounted a harrowing experience after reinstalling Windows 11. In an attempt to resolve performance issues, they performed a clean installation of the operating system. Post-installation, they discovered that two of their backup drives, containing 3TB of invaluable data, were encrypted by BitLocker without their initiation. This unexpected encryption rendered the data inaccessible, as the user did not possess the necessary recovery keys.
Understanding BitLocker’s Automatic Activation
BitLocker is Microsoft’s full-disk encryption tool, designed to safeguard data from unauthorized access. In Windows 11 Pro and Enterprise editions, particularly from version 24H2 onwards, BitLocker can automatically enable device encryption if the system meets specific hardware and policy criteria, such as TPM 2.0 support and Secure Boot. This automatic activation aims to enhance security seamlessly but can catch users off guard, especially during system reinstalls.
The Risks of Silent Encryption
The Reddit user’s experience underscores the potential dangers of automatic encryption:
– Data Inaccessibility: Without prior knowledge or recovery keys, users can find themselves locked out of their own data.
– Compromised Recovery Attempts: In desperation, users might resort to unverified recovery tools, increasing the risk of malware infections.
– Potential Data Loss: Without valid recovery keys, decrypting the data becomes nearly impossible, leading to potential data loss.
Technical Insights and Hardware Considerations
Certain hardware configurations can inadvertently trigger BitLocker’s automatic activation. For instance, systems equipped with AMD Ryzen processors and compatible motherboards may enable BitLocker if BIOS settings like fTPM are active. This automatic activation can occur even if the user has not explicitly enabled BitLocker, leading to unexpected encryption of drives.
Preventive Measures and Best Practices
To mitigate the risks associated with automatic BitLocker encryption, consider the following steps:
1. Disable Automatic Encryption During Installation: Utilize registry tweaks or tools like Rufus during Windows 11 installation to prevent automatic encryption prompts.
2. Backup Recovery Keys: Always store BitLocker recovery keys securely, either in your Microsoft account or on external media.
3. Monitor Group Policy Settings: Regularly review and adjust Group Policy settings to manage encryption defaults and prevent unintended activations.
4. Stay Informed: Keep abreast of updates and changes in Windows 11’s encryption policies to make informed decisions about your data security.
Conclusion
While BitLocker serves as a robust tool for data protection, its automatic activation can lead to unintended consequences. Users must remain vigilant, proactively managing their system settings and backup strategies to ensure that security measures do not inadvertently compromise their data.