This detailed report provides an analysis of the cyber incidents recorded on January 10, 2026. The dataset covers 133 distinct entries, revealing a diverse landscape […]
Author: The Daily Tech Feed Team
WhatsApp Worm Spreads Astaroth Banking Trojan in Brazil, Exploits Trusted Contacts for Rapid Malware Distribution
WhatsApp Worm Propagates Astaroth Banking Trojan Across Brazil Cybersecurity experts have recently uncovered a sophisticated campaign leveraging WhatsApp to disseminate the Astaroth banking trojan, primarily […]
Iranian Hackers Exploit Vulnerabilities, Target Israel, U.S. Agencies, and More in Week’s Cybersecurity News
Cybersecurity Weekly Recap: RustFS Vulnerability, Iranian Cyber Operations, and Emerging Threats In the ever-evolving landscape of cybersecurity, the past week has unveiled a series of […]
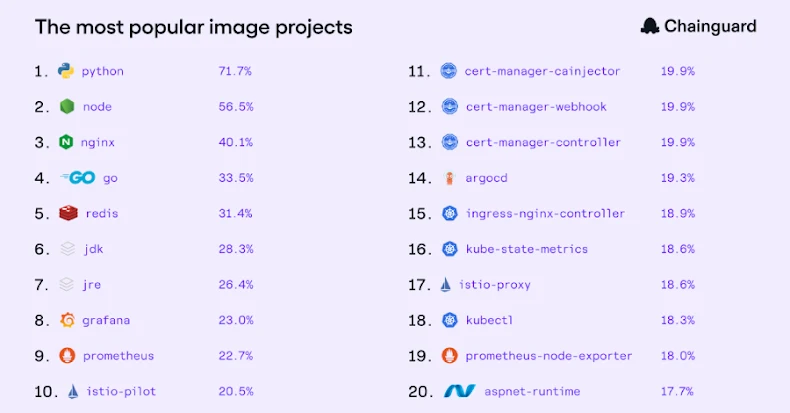
Chainguard Report Highlights Security Challenges in Diverse Open-Source Software Usage
Navigating the Complexities of Trusted Open Source: Insights from Chainguard’s Latest Report In the rapidly evolving landscape of open-source software, understanding how organizations utilize and […]
Malicious npm Packages Deploy NodeCordRAT to Target Cryptocurrency Enthusiasts
Unveiling NodeCordRAT: Malicious npm Packages Targeting Cryptocurrency Enthusiasts In a recent cybersecurity revelation, researchers have identified three malicious npm packages designed to deploy a previously […]
OpenAI Launches ChatGPT Health for Secure, Personalized Health Conversations
OpenAI Introduces ChatGPT Health: A Secure Platform for Personalized Health Conversations On January 8, 2026, OpenAI unveiled ChatGPT Health, a specialized platform designed to facilitate […]
FBI Warns of North Korean Spear-Phishing Attacks Using Malicious QR Codes Targeting US Entities
FBI Alerts on North Korean Hackers’ Use of Malicious QR Codes in Spear-Phishing Attacks The U.S. Federal Bureau of Investigation (FBI) has issued a warning […]
Critical Vulnerabilities Found in Coolify Allow Full Server Compromise; Users Urged to Update and Review Security Measures
Critical Vulnerabilities in Coolify Expose Self-Hosted Servers to Full Compromise Cybersecurity experts have recently identified multiple critical vulnerabilities in Coolify, an open-source platform designed for […]
Cisco Urges Critical Updates for ISE and Snort 3 to Fix Security Flaws
Cisco Releases Critical Security Updates for ISE and Snort 3 to Address Vulnerabilities Cisco has recently issued critical security updates to address vulnerabilities in its […]
CISA Urges Action on Critical Microsoft Office, HPE OneView Vulnerabilities Amid Active Exploitation
CISA Alerts on Active Exploitation of Microsoft Office and HPE OneView Vulnerabilities The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently identified and added […]
![[January-11-2026] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)