Massive Data Breach at Texas Gas Station Operator Compromises Over 377,000 Customers’ Information In a significant cybersecurity incident, Gulshan Management Services, Inc., a gas station […]
Author: The Daily Tech Feed Team
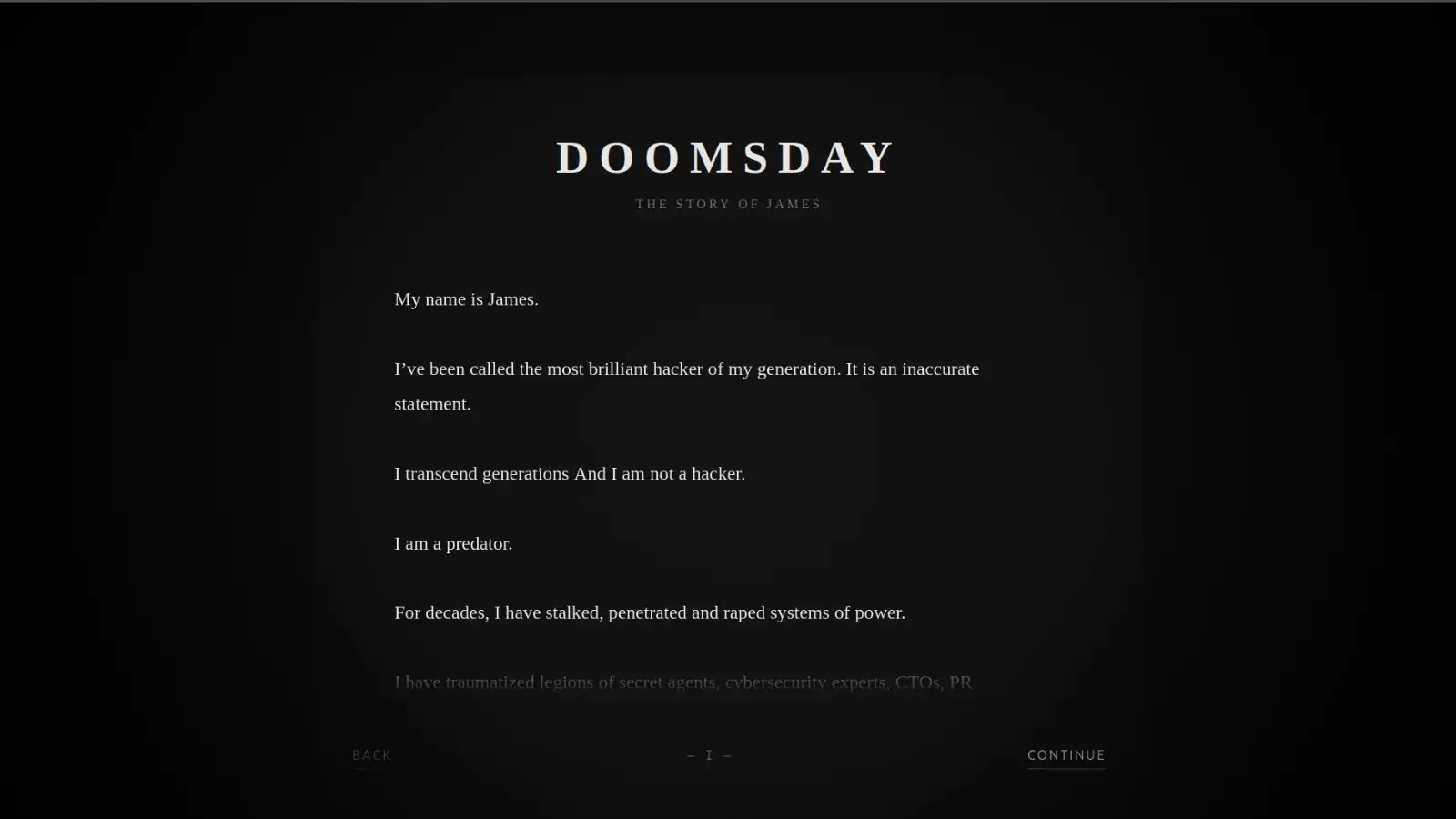
BreachForums User Database Leaked: Over 323,000 Accounts Exposed in Major Dark Web Breach
BreachForums’ User Database Exposed: A Cybercriminal Haven Compromised In a striking development within the cybercrime community, a hacker identified as James has publicly released the […]
Apple’s Foldable iPhone Set for 2026 Launch with Advanced Design and Premium Pricing
Apple’s iPhone Fold: Anticipated Design, Pricing, and Launch Timeline Apple is poised to make a significant leap in smartphone innovation with the introduction of the […]
Roborock Offers $300 Off F25 Ultra Floor Cleaner, Limited-Time Deal
Roborock’s F25 Ultra Floor Cleaner: $300 Off for a Limited Time Roborock has announced a limited-time promotion on its latest F25 series floor cleaners, offering […]
CES 2026: Innovative Apple Accessories Unveiled, From MagSafe Keyboards to Modular Controllers
Top Apple Accessories Unveiled at CES 2026: Elevate Your iPhone and Mac Experience The Consumer Electronics Show (CES) 2026 in Las Vegas showcased a plethora […]
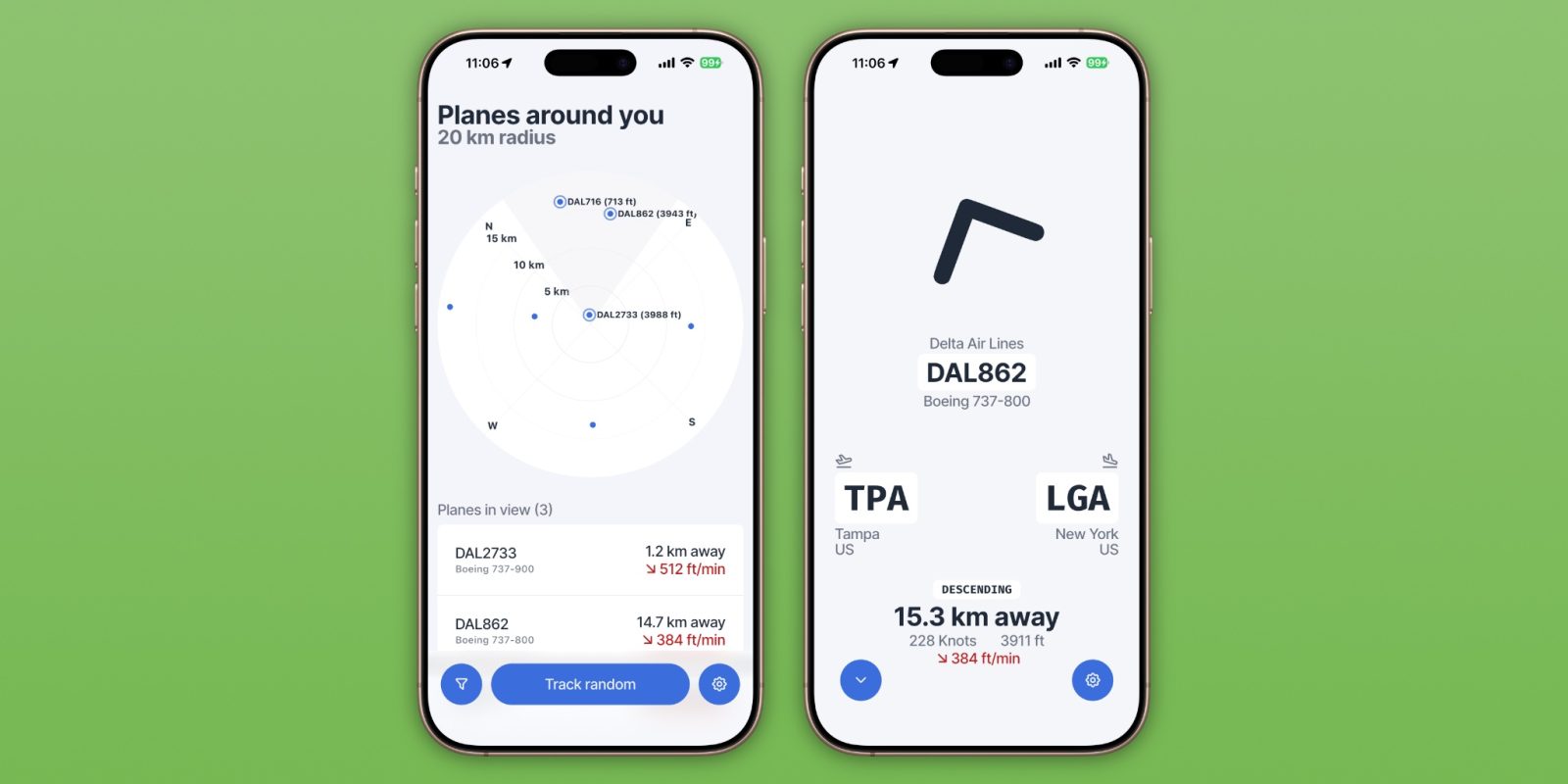
Zephy App Turns iPhone into Real-Time Plane Spotting Companion
Zephy: Your Personal Plane Spotting Companion for iPhone For aviation enthusiasts and the casually curious alike, the sky has always been a source of wonder. […]
Apple’s Siri Set for Major Upgrade with Contextual Understanding and In-App Actions in iOS 26.4
Anticipating Siri’s Evolution: Upcoming Enhancements in Apple Intelligence Apple’s virtual assistant, Siri, is on the brink of a significant transformation, with a suite of advanced […]
Apple’s iPhone Air Designer Joins Hark AI Lab, Aims for Human-Centric Innovations
Apple’s iPhone Air Designer Joins Hark AI Lab to Pioneer ‘Human-Centric’ AI Innovations In a significant move within the tech industry, Abidur Chowdhury, the industrial […]
Pebble Unveils Time 2, Round 2, and Innovative Index Ring at CES 2026
Pebble’s Triumphant Return: Hands-On with Pebble Time 2, Round 2, and the Innovative Index Ring The resurgence of Pebble smartwatches has been a beacon of […]
Google Messages Revamps with Material 3 Design, Enhanced Media Sharing, and New Security Features
Google Messages Introduces Exciting New Features for Enhanced User Experience Google Messages, the widely-used messaging application, has recently unveiled a series of updates aimed at […]