Apple’s March 4 ‘Special Apple Experience’: Anticipated Product Announcements and Insights Apple has officially announced a special Apple Experience scheduled for March 4, 2026, set […]
Author: The Daily Tech Feed Team
Apple to Launch Budget-Friendly MacBook with A18 Pro Chip and Vibrant Colors in 2026
Apple’s Upcoming Affordable MacBook: What to Expect Apple is set to unveil a new, budget-friendly MacBook on March 4, 2026, during its Special Apple Experience […]
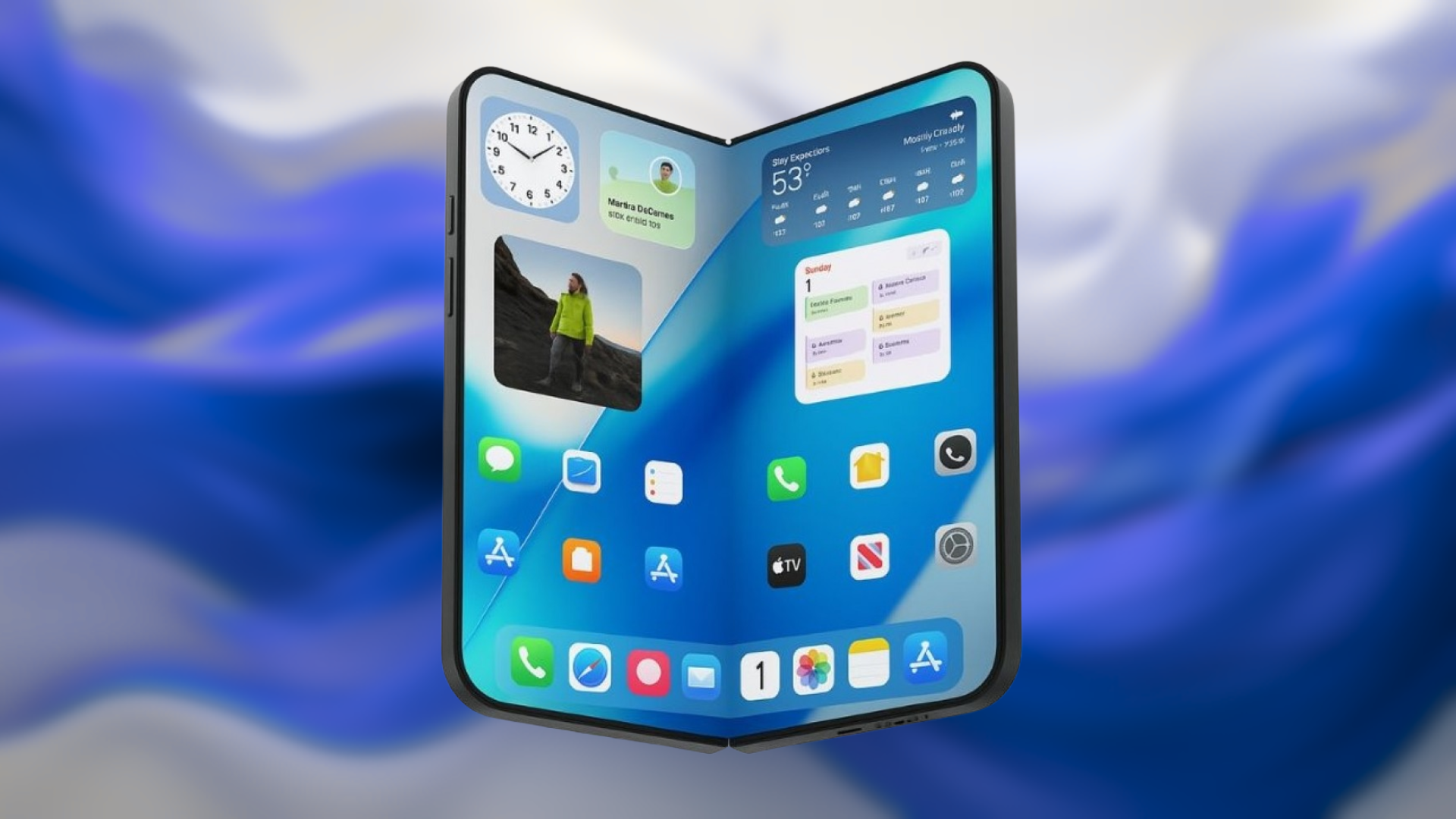
Apple to Enter Foldable Phone Market in 2026 with High-End iPhone Featuring Innovative Design and Advanced Specs
Apple’s Foldable iPhone: A Comprehensive Overview of Leaks, Specs, and Pricing Apple is poised to make a significant entry into the foldable smartphone market with […]
Apple Plans to Launch Eight New iPhones by 2027, Including First Foldable Model and Major Redesigns
Apple’s Ambitious Roadmap: Eight New iPhones Set to Launch by 2027 Apple is gearing up for an eventful period in its iPhone lineup, with plans […]
WhatsApp Tests ‘Spoiler’ Feature for Enhanced Message Privacy with Concealed Text Option
WhatsApp Introduces ‘Spoiler’ Formatting to Enhance Messaging Privacy WhatsApp is developing a new feature aimed at enhancing user privacy and control over message content. This […]
EC-Council Launches Comprehensive AI Certification Suite to Enhance U.S. Workforce and Security
EC-Council Unveils Comprehensive AI Certification Suite to Bolster U.S. Workforce and Security In response to the escalating integration of artificial intelligence (AI) across industries, EC-Council, […]
CISA Warns of Critical Roundcube Flaws Amid Active Exploitation; Urges Immediate Patching
CISA Flags Critical Roundcube Vulnerabilities Amid Active Exploitation The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently added two significant security vulnerabilities affecting Roundcube […]
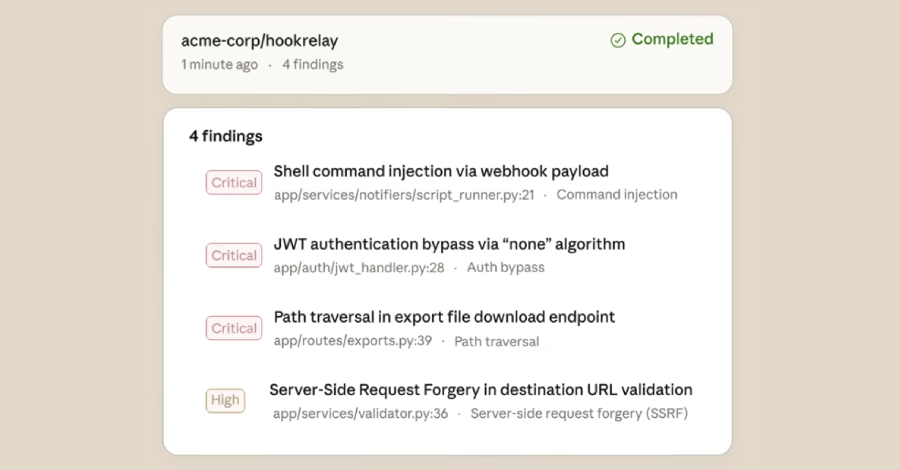
Anthropic Launches Claude Code Security: AI Tool for Code Vulnerability Detection and Patching
Anthropic Unveils Claude Code Security: AI-Driven Vulnerability Detection and Patching In a significant advancement for software security, Anthropic has introduced Claude Code Security, an AI-powered […]
Wikipedia Blacklists Archive.today Citing DDoS, Content Manipulation Allegations
Wikipedia Severs Ties with Archive.today Amid DDoS Allegations In a decisive move, Wikipedia’s editorial community has elected to sever all connections with Archive.today, a web […]
Sam Altman Urges Shift to Sustainable Energy Amid AI’s Environmental Impact Concerns
Sam Altman Addresses AI’s Energy Consumption Concerns At a recent event hosted by The Indian Express, OpenAI CEO Sam Altman tackled growing concerns about the […]