Cybersecurity experts have identified a new campaign involving the Astaroth banking trojan, which now leverages GitHub repositories to sustain its operations even after infrastructure takedowns. This strategic shift enhances the malware’s resilience against traditional command-and-control (C2) server disruptions.
Innovative Use of GitHub for Resilience
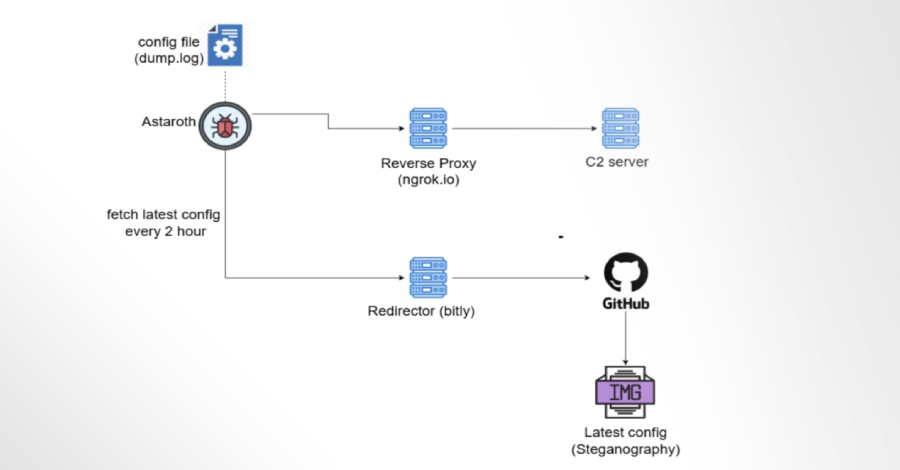
Traditionally, malware relies on dedicated C2 servers to receive instructions and updates. However, these servers are vulnerable to law enforcement actions and security interventions. To counteract this, Astaroth’s operators have adopted GitHub—a widely trusted platform—to host their malware configurations. By embedding malicious configurations within GitHub repositories, the trojan can retrieve fresh instructions, ensuring uninterrupted functionality even if primary C2 servers are disabled.
Geographical Focus and Historical Context
The current campaign predominantly targets Brazil, aligning with Astaroth’s historical focus on Latin American countries such as Mexico, Uruguay, Argentina, Paraguay, Chile, Bolivia, Peru, Ecuador, Colombia, Venezuela, and Panama. Previous campaigns in July and October 2024, identified by Google and Trend Micro as PINEAPPLE and Water Makara respectively, also utilized phishing emails to disseminate the malware.
Detailed Attack Chain
The infection process begins with phishing emails that mimic DocuSign communications, enticing recipients to download a ZIP file containing a Windows shortcut (.lnk) file. When executed, this shortcut initiates a sequence of events:
1. Obfuscated JavaScript Execution: The LNK file runs obfuscated JavaScript code designed to evade detection.
2. Secondary JavaScript Retrieval: This script fetches additional JavaScript from an external server.
3. Payload Download: The newly acquired script downloads multiple files from randomly selected hard-coded servers.
4. AutoIt Script Execution: Among the downloaded files is an AutoIt script, which is executed to facilitate further actions.
5. Shellcode Deployment: The AutoIt script loads and runs shellcode, a small piece of code used as a payload.
6. DLL Injection: The shellcode loads a Delphi-based DLL that decrypts and injects the Astaroth malware into a newly created RegSvc.exe process.
Functionality and Targeted Entities
Astaroth is designed to monitor user activity, specifically targeting visits to banking and cryptocurrency websites. It employs keylogging techniques to capture credentials, transmitting the stolen information to attackers via the Ngrok reverse proxy. The malware checks the active browser window every second to detect access to specific financial sites, including:
– caixa.gov.br
– safra.com.br
– itau.com.br
– bancooriginal.com.br
– santandernet.com.br
– btgpactual.com
– etherscan.io
– binance.com
– bitcointrade.com.br
– metamask.io
– foxbit.com.br
– localbitcoins.com
Evasion and Persistence Mechanisms
To avoid detection and analysis, Astaroth incorporates several sophisticated techniques:
– Anti-Analysis Features: The malware terminates itself if it detects the presence of emulators, debuggers, or analysis tools such as QEMU Guest Agent, HookExplorer, IDA Pro, ImmunityDebugger, PE Tools, WinDbg, and Wireshark.
– Persistence Strategies: Astaroth ensures its longevity on infected systems by placing an LNK file in the Windows Startup folder. This setup allows the malware to launch automatically upon system reboot.
– Geofencing and Locale Checks: The initial URL accessed by the JavaScript within the LNK file is geofenced, and the malware verifies that the system locale is not set to English or the United States, thereby targeting specific regions more effectively.
Steganography and GitHub Utilization
Astaroth’s operators employ steganography—a technique of hiding information within other non-suspicious data—to conceal configuration details within images hosted on GitHub. This method allows the malware to discreetly update its configurations when primary C2 servers are inaccessible, effectively using GitHub as a resilient backup infrastructure.
Collaborative Efforts and Temporary Disruption
McAfee Labs collaborated with GitHub to remove the malicious repositories, temporarily disrupting Astaroth’s operations. However, the adaptability demonstrated by the malware underscores the ongoing challenges in combating such threats.
Implications and Recommendations
The innovative use of legitimate platforms like GitHub for malicious purposes highlights the evolving tactics of cybercriminals. Organizations and individuals are advised to:
– Enhance Email Security: Implement advanced email filtering solutions to detect and block phishing attempts.
– Educate Users: Conduct regular training sessions to raise awareness about phishing tactics and safe online practices.
– Monitor Network Traffic: Utilize network monitoring tools to detect unusual activities that may indicate malware infections.
– Implement Multi-Factor Authentication (MFA): Strengthen access controls by requiring multiple forms of verification.
– Keep Systems Updated: Regularly update software and security patches to mitigate vulnerabilities.
By adopting these measures, entities can bolster their defenses against sophisticated malware campaigns like those involving the Astaroth banking trojan.