Enhancing Business Security with Live Threat Intelligence from 15,000 SOCs
In today’s rapidly evolving digital landscape, cybersecurity leaders grapple with a challenging equation: acquiring intelligence that is both comprehensive enough to safeguard their organizations and timely enough to counter emerging threats, all while ensuring their teams are not overwhelmed by false positives. Striking this balance is crucial, as the effectiveness of a Security Operations Center (SOC) hinges on its ability to process vast amounts of data efficiently without succumbing to information overload.
The Intelligence Paradox: Balancing Data Volume and Relevance
Chief Information Security Officers (CISOs) are acutely aware of the delicate balance required in threat intelligence management. Utilizing too few threat feeds can leave an organization vulnerable, missing critical indicators that could preempt potential breaches. Conversely, an overabundance of feeds can inundate SOC analysts with alerts, leading to fatigue and the risk of overlooking genuine threats. This operational challenge translates into significant business risks, including delayed response times, missed detection of sophisticated attacks, and inefficient allocation of resources.
The ideal solution lies in obtaining data that is both comprehensive and curated, real-time and actionable, detailed yet digestible. Achieving this equilibrium enables organizations to enhance their security posture without overburdening their teams.
Integrating Contextual Intelligence for Enhanced Resilience
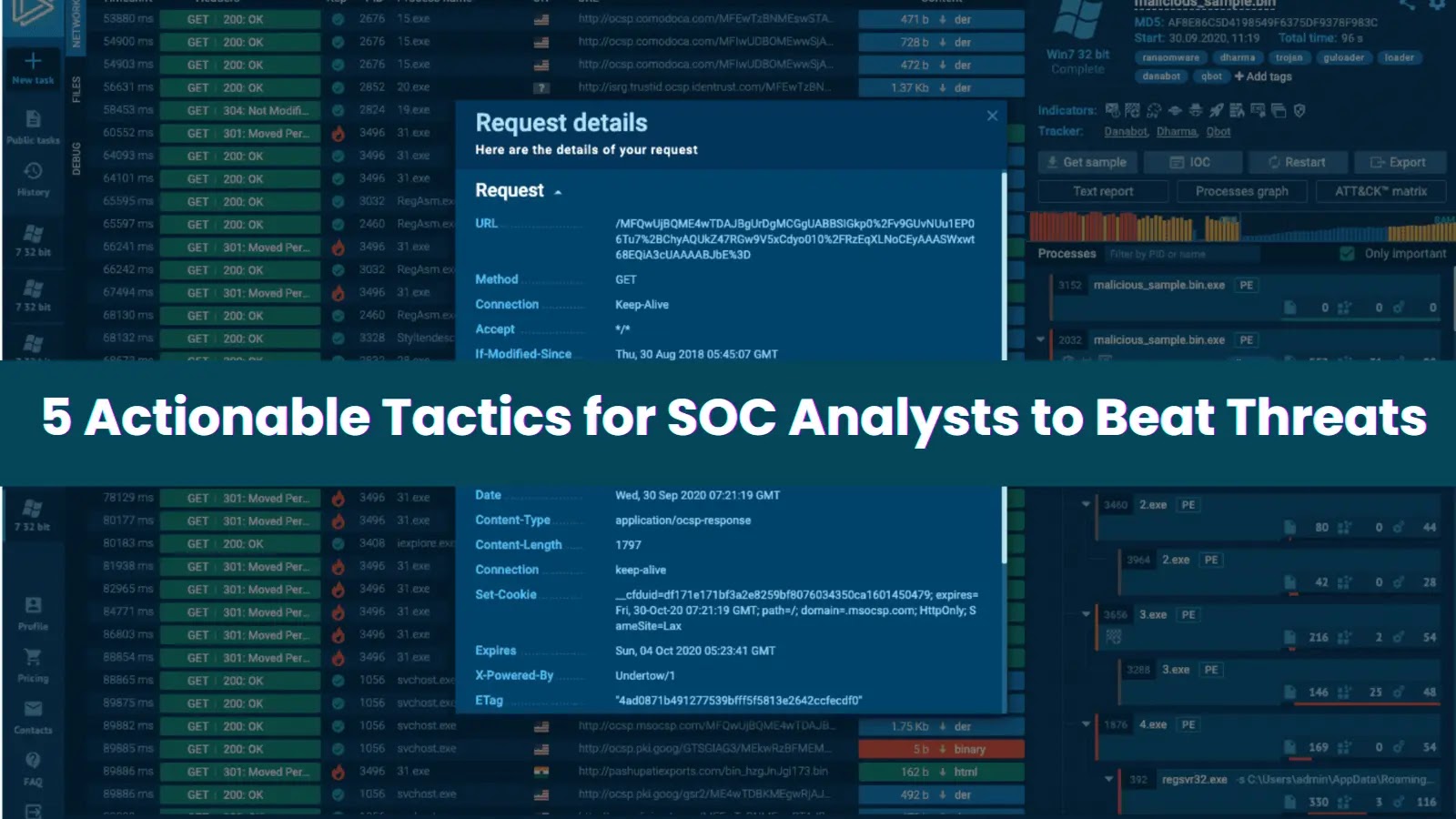
ANY.RUN’s Threat Intelligence Feeds are designed to address this challenge by transforming raw data into actionable insights. By leveraging data from over 15,000 SOCs and researchers utilizing ANY.RUN’s interactive malware sandbox, these feeds provide live intelligence on real-time attacks. Each record is supported by behavioral analysis and real-world evidence, offering a nuanced understanding of threats.
This integration of context and timeliness is vital for decision-makers. It ensures that analysts can prioritize genuine threats, act proactively, and protect organizational assets effectively. The feeds seamlessly integrate with existing security tools such as Security Information and Event Management (SIEM) systems, Endpoint Detection and Response (EDR) solutions, and firewalls, enriching alerts with context and facilitating automated response workflows. This proactive approach shifts the organization’s security posture from reactive to preventive, enabling the blocking of threats before they infiltrate the network.
For Managed Security Service Providers (MSSPs) overseeing security across multiple clients, these feeds are invaluable. They allow for scalable protection without a proportional increase in headcount, applying insights gained from one client’s threat landscape to safeguard others instantaneously.
The Business Impact of Contextual Threat Intelligence
Contextual intelligence transforms raw data into actionable information. When a SIEM flags a suspicious IP address, generic feeds may simply label it as malicious. In contrast, ANY.RUN’s feeds provide detailed information on how the IP is malicious, its association with specific malware families, the attack techniques employed, and relevant Indicators of Compromise (IOCs) to monitor within the environment.
For security teams, this depth of information translates to:
– Faster Triage: Analysts can quickly assess the severity and scope of threats.
– Accurate Prioritization: Distinguishing between critical incidents and low-risk events becomes more straightforward.
– Effective Response: Clear guidance on appropriate containment measures enhances response efficacy.
– Reduced Burnout: Analysts can focus on genuine threats, reducing time spent on false positives.
For business leaders, contextual intelligence offers:
– Reduced Risk Exposure: Timely identification and mitigation of threats minimize potential damage.
– Operational Efficiency: Streamlined processes lead to cost savings and optimized resource allocation.
– Enhanced Compliance: Proactive threat management supports adherence to regulatory requirements.
– Informed Decision-Making: Access to detailed threat insights aids strategic planning and risk management.
Leveraging Collective Defense for Proactive Security
The concept of collective defense is central to modern cybersecurity strategies. By tapping into the shared experiences and data of over 15,000 SOCs, organizations can benefit from a wealth of knowledge and insights. This collaborative approach enables the identification of emerging threats, understanding of evolving attack vectors, and development of effective countermeasures.
ANY.RUN’s Threat Intelligence Feeds exemplify this collective defense model by aggregating and analyzing data from a vast network of security professionals. This shared intelligence empowers organizations to stay ahead of adversaries, adapt to new threats swiftly, and enhance their overall security resilience.
Implementing Live Threat Intelligence: A Strategic Imperative
Integrating live threat intelligence into an organization’s security framework is not merely a technical enhancement but a strategic imperative. It involves:
1. Assessment of Current Capabilities: Evaluating existing security tools and processes to identify gaps and areas for improvement.
2. Selection of Appropriate Feeds: Choosing threat intelligence feeds that align with the organization’s specific needs and risk profile.
3. Integration with Existing Systems: Ensuring seamless incorporation of feeds into current security infrastructure to maximize effectiveness.
4. Continuous Monitoring and Adaptation: Regularly reviewing and updating threat intelligence strategies to address the dynamic nature of cyber threats.
By adopting a strategic approach to live threat intelligence, organizations can enhance their ability to detect, respond to, and mitigate cyber threats, thereby safeguarding their assets and maintaining business continuity.
Conclusion
In the face of an increasingly complex threat landscape, the integration of live, contextual threat intelligence from a vast network of SOCs offers a viable solution to the intelligence paradox. By balancing comprehensive data with actionable insights, organizations can enhance their security posture, improve operational efficiency, and reduce risk exposure. Embracing this approach is essential for businesses aiming to navigate the challenges of modern cybersecurity effectively.