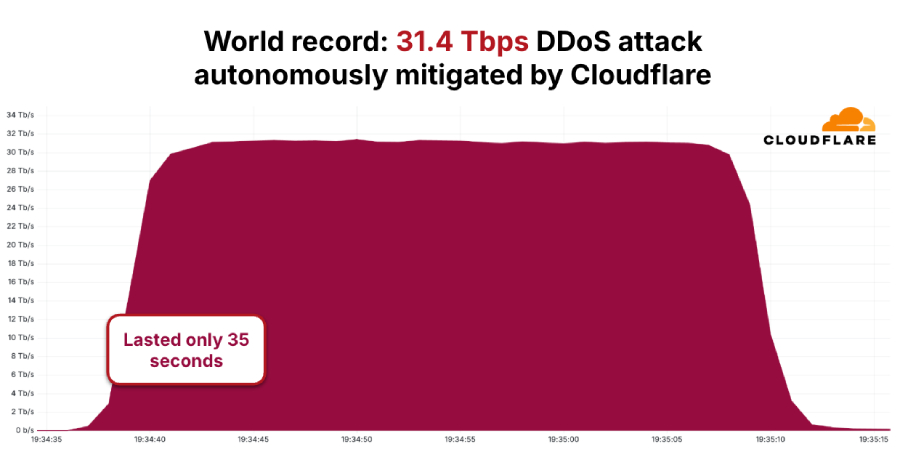
AISURU/Kimwolf Botnet Unleashes Unprecedented 31.4 Tbps DDoS Attack
In November 2025, the AISURU/Kimwolf botnet executed a record-breaking distributed denial-of-service (DDoS) attack, peaking at 31.4 terabits per second (Tbps) and lasting 35 seconds. Cloudflare, a leading web infrastructure and security company, detected and mitigated this hyper-volumetric HTTP DDoS attack, marking a significant escalation in cyber threats.
The AISURU/Kimwolf botnet has been linked to a series of high-profile DDoS campaigns, including one codenamed The Night Before Christmas, which began on December 19, 2025. During this campaign, the botnet launched attacks averaging 3 billion packets per second (Bpps), 4 Tbps, and 54 million requests per second (Mrps), with peaks reaching 9 Bpps, 24 Tbps, and 205 Mrps.
The year 2025 witnessed a 121% surge in DDoS attacks, with Cloudflare automatically mitigating an average of 5,376 attacks per hour. The total number of DDoS attacks more than doubled to 47.1 million. Notably, network-layer DDoS attacks accounted for 78% of all DDoS incidents in the fourth quarter of 2025. Hyper-volumetric attacks increased by 40% compared to the previous quarter, with the size of these attacks growing over 700% compared to late 2024.
The AISURU/Kimwolf botnet has compromised over 2 million Android devices, primarily off-brand Android TVs, by infiltrating residential proxy networks like IPIDEA. In response, Google disrupted the proxy network and initiated legal action to dismantle domains used to control these devices and proxy traffic through them. Cloudflare collaborated with Google to suspend access to numerous accounts and domains misusing its infrastructure.
IPIDEA enrolled devices using at least 600 trojanized Android apps embedding various proxy software development kits (SDKs) and over 3,000 trojanized Windows binaries posing as legitimate software. The Beijing-based company also advertised VPN and proxy apps that covertly turned users’ Android devices into proxy exit nodes without their knowledge. These operations were connected to a centralized infrastructure under IPIDEA’s control.
In the fourth quarter of 2025, telecommunications, service providers, and carriers emerged as the most attacked sectors, followed by information technology, gambling, gaming, and computer software industries. The most attacked countries included China, Hong Kong, Germany, Brazil, the U.S., the U.K., Vietnam, Azerbaijan, India, and Singapore. Bangladesh surpassed Indonesia as the largest source of DDoS attacks, with other top sources being Ecuador, Indonesia, Argentina, Hong Kong, Ukraine, Vietnam, Taiwan, Singapore, and Peru.
The AISURU/Kimwolf botnet’s unprecedented 31.4 Tbps DDoS attack underscores the escalating scale and sophistication of cyber threats. The collaboration between tech giants like Google and Cloudflare highlights the necessity for coordinated efforts to combat these evolving challenges.