Unprecedented 29.7 Tbps DDoS Attack by Aisuru Botnet Sets New Record
In a significant escalation of cyber threats, the Aisuru botnet has launched a Distributed Denial-of-Service (DDoS) attack peaking at 29.7 terabits per second (Tbps), setting a new benchmark in the scale of such assaults. This incident underscores the increasing vulnerability of global internet infrastructure to massive cyber onslaughts.
The Attack’s Magnitude and Methodology
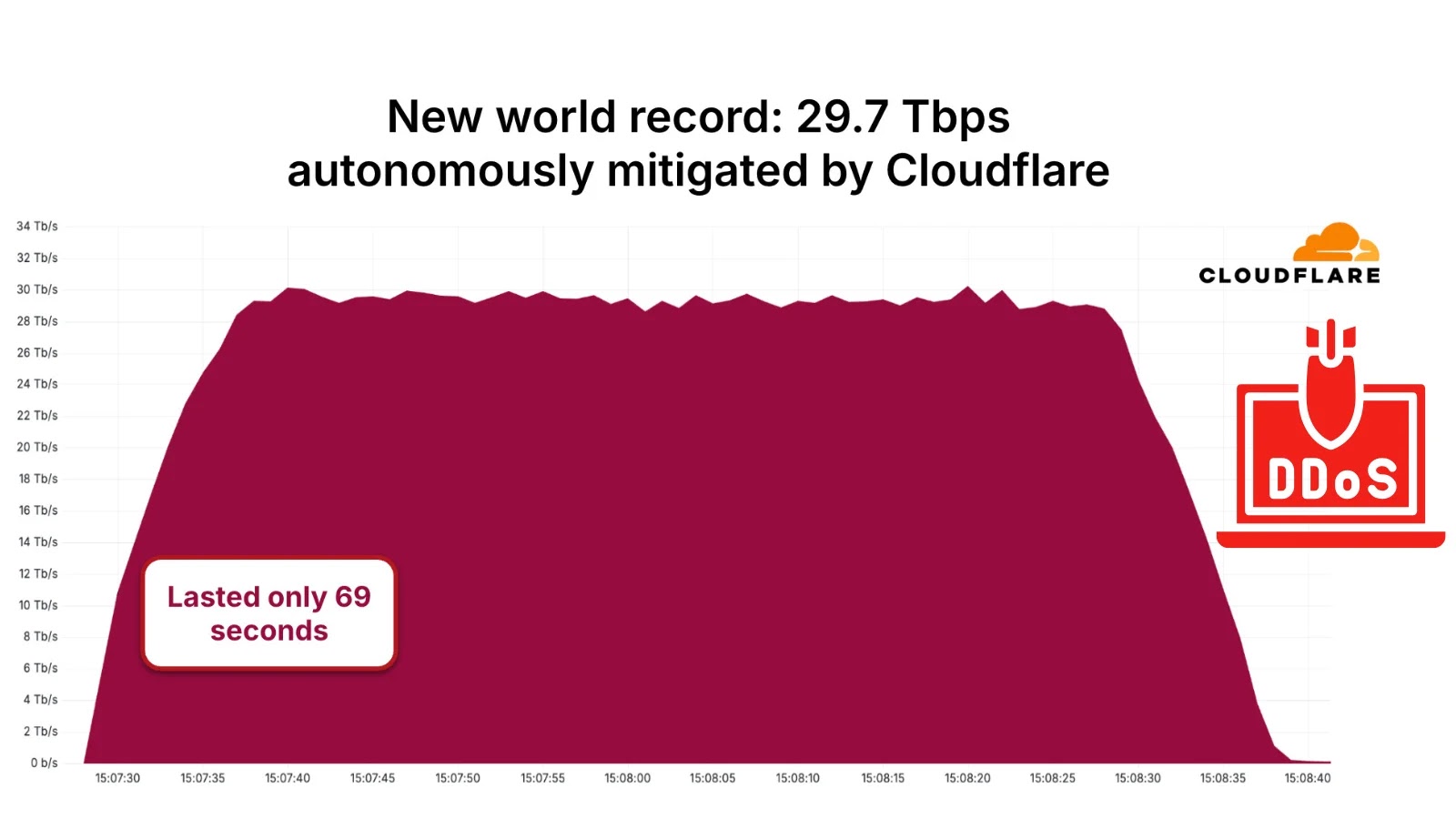
The attack, which occurred in the third quarter of 2025, surpassed the previous record of a 22 Tbps DDoS attack mitigated by Cloudflare earlier that year. The Aisuru botnet’s assault not only reached a peak of 29.7 Tbps but also generated approximately 14.1 billion packets per second, highlighting the sheer volume and intensity of the attack.
Employing a UDP carpet bombing technique, the botnet targeted around 15,000 destination ports per second. This method involved randomizing packet attributes to evade traditional filtering mechanisms and legacy scrubbing centers, making detection and mitigation more challenging.
Cloudflare’s Response and Mitigation Efforts
Despite the unprecedented scale of the attack, Cloudflare’s autonomous mitigation infrastructure swiftly detected and filtered the malicious traffic within seconds. This rapid response ensured that the targeted services remained operational, preventing any noticeable impact on end-users.
Cloudflare’s latest DDoS threat report indicates that the Aisuru botnet comprises an estimated 1 to 4 million compromised devices globally, making it the most significant DDoS botnet in the current cyber threat landscape. Since the beginning of 2025, Cloudflare has mitigated 2,867 attacks attributed to Aisuru, including 1,304 hyper-volumetric events in the third quarter alone—a 54% increase from the previous quarter.
The Evolving Threat Landscape
The rise of the Aisuru botnet signifies a shift in the DDoS threat environment. Portions of this botnet are reportedly available for hire, allowing potential attackers to rent substantial capacity capable of overwhelming backbone links or incapacitating national internet service providers for relatively low costs.
In the third quarter of 2025, Cloudflare blocked 8.3 million DDoS attacks, marking a 15% increase from the previous quarter and a 40% rise year-over-year. This brings the year-to-date total to 36.2 million attacks, already surpassing the full-year volume of 2024 by 170%, with a quarter still remaining.
Network-layer DDoS attacks accounted for approximately 71% of all incidents in the quarter, experiencing an 87% quarter-over-quarter increase and a 95% year-over-year surge. Conversely, HTTP-layer attacks declined by 41% quarter-over-quarter and 17% year-over-year, indicating a strategic pivot by attackers towards raw transport and bandwidth exhaustion methods.
Notably, incidents exceeding 100 million packets per second rose by 189% quarter-over-quarter, and those surpassing 1 Tbps grew by 227%. However, the majority of these attacks concluded within 10 minutes, rendering manual responses or on-demand mitigation contracts less effective.
Broader Implications and Industry Impact
The ramifications of the Aisuru botnet’s activities extend beyond direct targets. Reports indicate that the substantial botnet traffic has caused significant disruptions across U.S. internet service providers, even when they were not the intended victims.
Cloudflare’s data reveals that Aisuru and similar actors frequently target telecommunications providers, gaming platforms, hosting companies, and financial services firms. In the third quarter, the most attacked industries included information technology and services, telecommunications, and gambling and casinos.
Additionally, DDoS traffic against generative AI providers spiked by up to 347% month-over-month in September. Attacks on the mining, minerals, and metals, and automotive sectors also surged, coinciding with trade tensions between the European Union and China over rare earths and electric vehicle tariffs.
Geographically, Indonesia remained the top global source of DDoS traffic, with a 31,900% increase in HTTP DDoS requests since 2021. In the third quarter of 2025, the Maldives, France, and Belgium also experienced significant increases in DDoS activity, reflecting the global and dynamic nature of these cyber threats.
Conclusion
The record-breaking 29.7 Tbps DDoS attack orchestrated by the Aisuru botnet marks a pivotal moment in cybersecurity, highlighting the escalating scale and sophistication of cyber threats. This incident serves as a stark reminder of the critical need for robust, adaptive, and proactive defense mechanisms to safeguard global internet infrastructure against increasingly potent and complex attacks.