Unveiling AI-Powered Zero Trust: Detecting Stealthy Cyber Threats Without Traditional Indicators
In the ever-evolving landscape of cybersecurity, traditional defense mechanisms are increasingly being outmaneuvered by sophisticated attack strategies. Modern cyber threats often bypass conventional detection methods by exploiting existing tools and processes within an organization’s environment, leaving minimal traces and evading standard security alerts.
The Emergence of Fileless Attacks
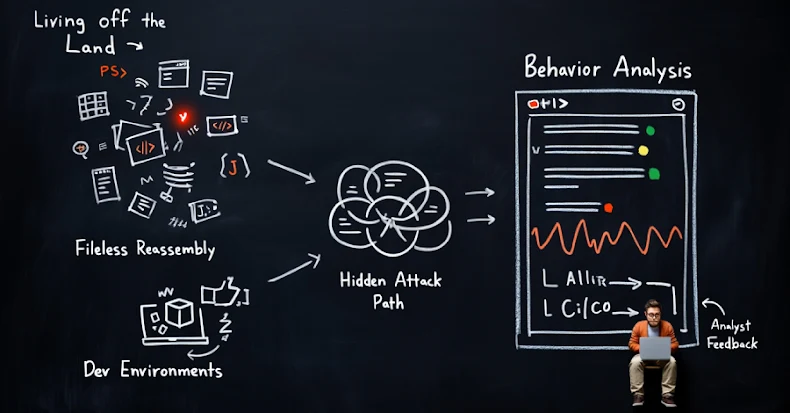
Historically, malware detection has relied heavily on identifying malicious files or known indicators of compromise. However, attackers are now leveraging living off the land techniques, utilizing legitimate system tools such as PowerShell, Windows Management Instrumentation (WMI), and remote desktop protocols to execute malicious activities. These methods do not introduce new files into the system, making them particularly challenging for traditional file-based detection systems to identify.
Understanding Living off the Land Attacks
Living off the land attacks involve the misuse of trusted system utilities to carry out malicious operations. By exploiting tools already present within the environment, attackers can perform unauthorized actions without triggering conventional security mechanisms. For instance, PowerShell scripts can be used to download and execute malicious code directly in memory, bypassing file-based detection entirely.
The Challenge of Fileless Last Mile Reassembly Attacks
Another sophisticated tactic employed by cyber adversaries is the use of obfuscated HTML and JavaScript to execute malicious logic without delivering a clear payload to the endpoint. These last mile reassembly attacks involve assembling the malicious code at the final stage, often within the browser or application, making it difficult for legacy security tools to detect and mitigate the threat.
Securing Developer Environments
Developer environments, including Continuous Integration/Continuous Deployment (CI/CD) pipelines and third-party repositories, are particularly vulnerable to these advanced attack methods. The rapid pace of development and reliance on encrypted traffic can allow malicious code and risky dependencies to infiltrate systems unnoticed. Limited inspection and visibility in these environments further exacerbate the risk, as traditional security measures may not effectively monitor or control the flow of potentially harmful code.
The Role of AI-Powered Zero Trust Security
To address these evolving threats, organizations are increasingly turning to AI-powered Zero Trust security models. Zero Trust operates on the principle of never trust, always verify, ensuring that every access request is thoroughly authenticated and authorized, regardless of its origin. By integrating artificial intelligence and machine learning, Zero Trust architectures can analyze behavior patterns, detect anomalies, and identify potential threats that do not exhibit traditional indicators.
Cloud-Native Inspection and Behavior Analysis
Implementing cloud-native inspection and behavior analysis allows security teams to monitor and analyze activities in real-time. This approach enables the detection of subtle deviations from normal behavior, which may indicate the presence of a fileless attack. By focusing on the behavior of applications and users rather than solely on file-based indicators, organizations can uncover hidden attack paths before they reach users or production systems.
Practical Insights for Security Teams
For Security Operations Center (SOC) teams, IT leaders, and security architects, understanding and implementing AI-powered Zero Trust security is crucial. By moving beyond reliance on file-based signals and adopting a behavior-centric approach, organizations can enhance their ability to detect and respond to modern cyber threats. This proactive stance not only improves security posture but also supports business continuity by minimizing the impact of potential breaches.
Conclusion
As cyber threats continue to evolve, traditional security measures are proving insufficient against sophisticated, fileless attacks. Embracing AI-powered Zero Trust security models offers a robust solution by focusing on behavior analysis and continuous verification. By understanding and implementing these advanced security strategies, organizations can effectively detect and mitigate threats that operate without traditional files or indicators, ensuring a more secure and resilient digital environment.