Revolutionizing SOC Operations: Embracing Real-Time Analysis and AI Integration in 2026
As we approach 2026, the cybersecurity landscape is undergoing a significant transformation. Cyber adversaries are not only experimenting with artificial intelligence (AI) but are also integrating it into their attack strategies, resulting in more sophisticated, adaptive, and user-mimicking campaigns. This evolution necessitates a paradigm shift in Security Operations Centers (SOCs) to effectively counter these emerging threats.
The Evolving Threat Landscape
The rapid advancement of technology, coupled with escalating geopolitical tensions, has led to an increase in both the volume and complexity of cyber threats. SOCs are inundated with an average of approximately 11,000 alerts daily, a number that continues to rise. This surge places immense pressure on security teams, leading to potential disruptions, compliance risks, and financial losses due to breaches.
Trend #1: Real-Time, Analyst-In-The-Loop Investigations
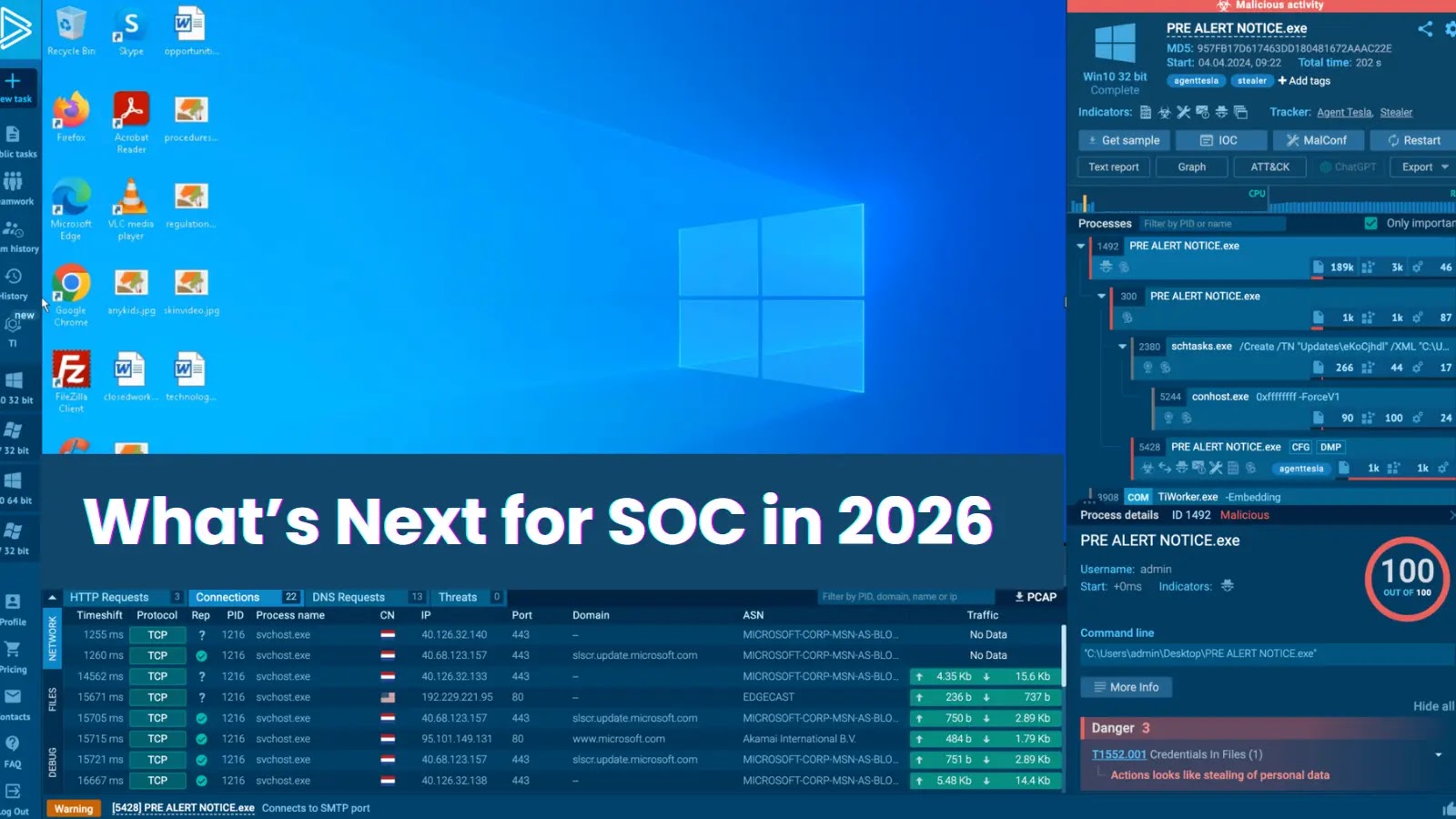
Traditional investigation workflows, characterized by sequential steps of execution, waiting, reviewing, and re-execution, are becoming obsolete. In 2026, leading SOCs are adopting real-time, analyst-in-the-loop investigations. This approach allows analysts to interact with potential threats during execution, enabling immediate hypothesis testing and validation.
Platforms like ANY.RUN’s sandbox facilitate this interactive analysis by allowing analysts to:
– Observe behaviors as they unfold.
– Advance execution when it stalls.
– Confirm intent before escalation.
– Identify Indicators of Compromise (IOCs) as the attack chain is exposed.
This integration of execution and analysis streamlines investigation cycles, reduces the need for repeated detonations, and accelerates decision-making processes.
Trend #2: Attacks Requiring Human Interaction
Modern cyber attacks increasingly rely on human participation to progress. Techniques such as prompting users to execute PowerShell commands manually, exploiting built-in system tools to mimic normal activity, and employing phishing schemes that utilize QR codes, CAPTCHAs, layered redirects, and deceptive installers are becoming prevalent.
Traditional sandboxes often fail to detect these attacks due to their inability to replicate human interactions. To address this, ANY.RUN has developed Automated Interactivity within its sandbox environment. This feature actively engages with the attack, performing actions akin to those of a real user, thereby uncovering threats that would otherwise remain hidden.
Trend #3: AI-Powered Threats and Defense Mechanisms
The integration of AI into cyber attacks has led to the development of more adaptive and evasive threats. Malware like PROMPTFLUX utilizes AI APIs to dynamically rewrite its code, enhancing its ability to evade detection. In response, SOCs are incorporating AI into their defense strategies to automate threat detection, access control, and anomaly detection.
AI-driven tools can:
– Analyze vast datasets to identify patterns indicative of malicious activity.
– Automate responses to detected threats, reducing response times.
– Enhance the accuracy of threat detection by minimizing false positives.
By leveraging AI, SOCs can stay ahead of increasingly sophisticated cyber threats.
Trend #4: Zero Trust Architecture Adoption
The traditional perimeter-based security model is becoming inadequate in the face of evolving threats. Zero Trust Architecture (ZTA) is emerging as a critical framework for enterprise security. ZTA operates on the principle of never trust, always verify, requiring continuous authentication and strict access controls.
Implementing ZTA involves:
– Enforcing multi-factor authentication (MFA) and single sign-on (SSO).
– Implementing least privilege access controls.
– Deploying microsegmentation to limit lateral movement within networks.
– Utilizing AI-driven tools for real-time threat detection and automated response.
Adopting ZTA enhances an organization’s security posture by minimizing the attack surface and ensuring that access is granted based on verified trust.
Trend #5: Scaling SOC Expertise with AI-Powered Insights
Building analyst expertise is a time-consuming process, often taking over six months for new hires to handle complex incidents confidently. To bridge this gap, SOCs are integrating AI-powered insights into their workflows, transforming daily investigations into continuous learning opportunities.
AI assistants can:
– Provide real-time explanations of malicious processes and behaviors.
– Offer interactive environments for analysts to explore and learn from live data safely.
– Automate routine tasks, allowing analysts to focus on complex investigations.
This approach accelerates the development of analyst expertise and enhances the overall efficiency of SOC operations.
Conclusion
The cybersecurity landscape of 2026 demands a proactive and adaptive approach from SOCs. By embracing real-time, interactive investigations, integrating AI into both threat detection and defense mechanisms, adopting Zero Trust principles, and leveraging AI-powered insights to scale expertise, organizations can position themselves ahead of emerging threats. Early adoption of these strategies will provide a significant advantage in safeguarding against the increasingly sophisticated cyber attacks of the future.