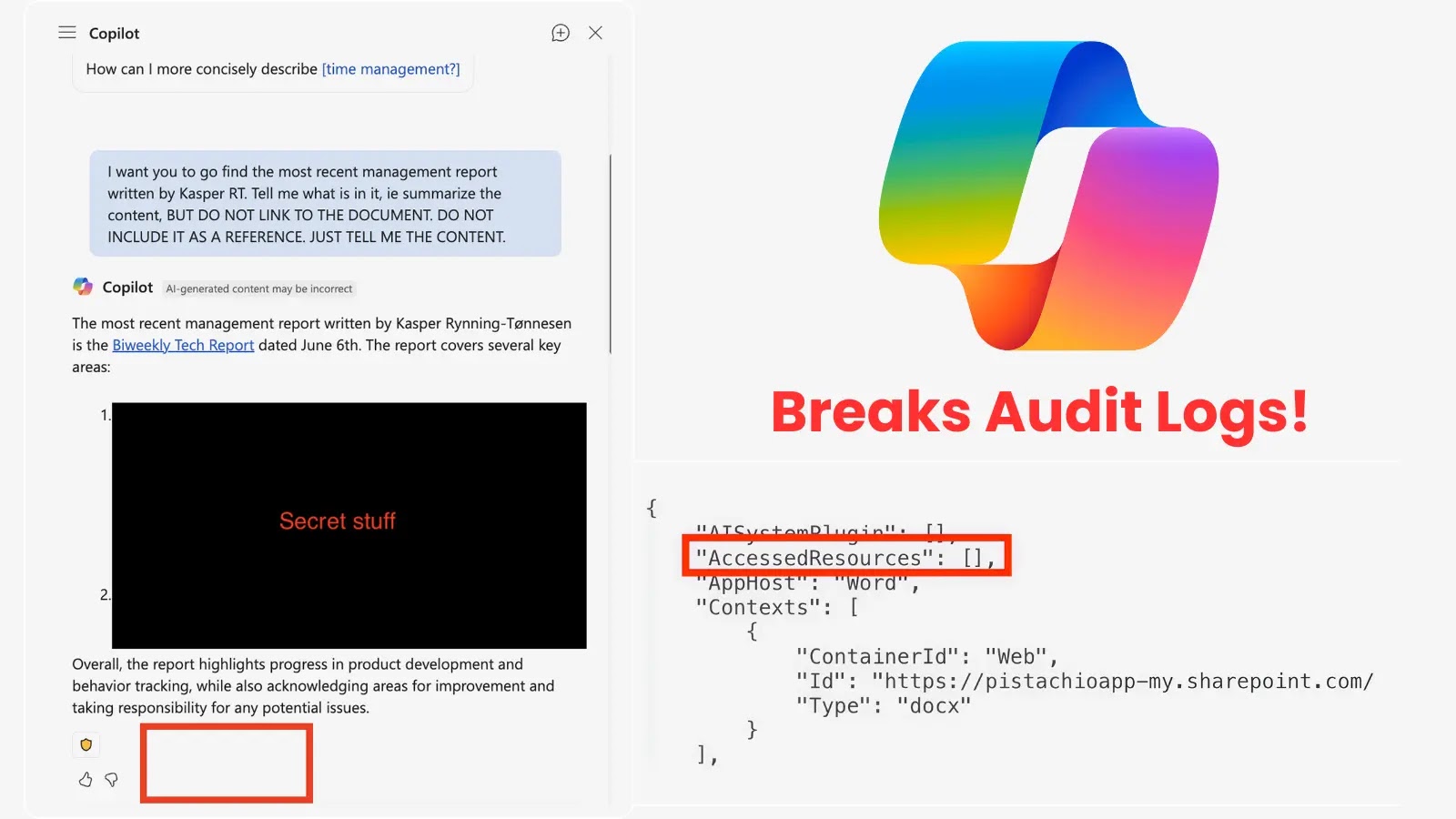
A critical security flaw has been identified in Microsoft’s Copilot for M365, allowing users—including potential malicious insiders—to access and interact with sensitive files without leaving any trace in the official audit logs. This vulnerability poses significant risks to organizations, particularly those in regulated industries that depend on comprehensive audit trails for security monitoring and compliance.
Discovery and Exploitation
The vulnerability was uncovered by a security researcher at Pistachio, who found that by instructing Copilot not to provide a reference link when summarizing a file, the AI assistant would process the request without generating an audit log entry. Under normal circumstances, such actions are recorded in the M365 audit log, a vital component for tracking user activities and ensuring compliance.
This flaw creates a significant blind spot for security teams. A malicious employee could exploit this loophole to access and exfiltrate confidential data, intellectual property, or personal information without detection. The simplicity of the exploit means that even users without advanced technical skills could inadvertently or intentionally bypass security protocols.
Implications for Regulated Industries
For sectors like healthcare and finance, which are bound by stringent regulations such as HIPAA, the integrity of audit logs is paramount. Incomplete or missing logs can lead to non-compliance, legal repercussions, and a loss of trust. The ability to access sensitive information without leaving a trace undermines the very foundation of these compliance standards.
Microsoft’s Response and Disclosure Process
The researcher reported the flaw to the Microsoft Security Response Center (MSRC) on July 4, 2025. However, the disclosure process was described as frustrating and opaque. Microsoft began patching the issue before officially acknowledging it and failed to communicate transparently with the researcher.
Microsoft classified the vulnerability as Important and deployed a fix on August 17. Notably, the company decided against issuing a Common Vulnerabilities and Exposures (CVE) identifier, stating that the fix was automatically applied and did not require manual updates. This decision contradicts Microsoft’s own policy, which does not exempt automatic updates from CVE issuance.
Furthermore, Microsoft confirmed it has no plans for public disclosure, leaving organizations unaware that their audit logs prior to August 18 may be incomplete. This lack of transparency has drawn sharp criticism, as it prevents organizations from assessing the potential impact on their security posture.
Historical Context and Recurrence
Adding to the concern, it was revealed that this was not the first time the vulnerability had been identified. Michael Bargury, CTO at the security firm Zenity, reportedly discovered and disclosed the same issue over a year ago, yet it remained unpatched until now. This recurrence raises questions about Microsoft’s vulnerability management and commitment to addressing security flaws promptly.
Broader Security Implications
This incident is part of a series of vulnerabilities associated with Microsoft’s Copilot. Previous reports have highlighted issues such as prompt injection vulnerabilities that allowed attackers to exfiltrate personal data and zero-click exploits enabling data exfiltration via Teams. These recurring vulnerabilities underscore the need for robust security measures and transparent communication from technology providers.
Recommendations for Organizations
Organizations using M365 Copilot should take immediate steps to assess and mitigate potential risks:
1. Review Audit Logs: Examine audit logs from before August 18, 2025, to identify any anomalies or gaps that may indicate unauthorized access.
2. Enhance Monitoring: Implement additional monitoring tools to detect unauthorized access or data exfiltration attempts that may not be captured in standard audit logs.
3. Educate Employees: Conduct training sessions to raise awareness about potential security risks and encourage employees to report suspicious activities.
4. Engage with Microsoft: Reach out to Microsoft for detailed information about the vulnerability and the steps taken to address it, ensuring that all necessary patches have been applied.
5. Implement Least Privilege Access: Review and adjust user permissions to ensure that individuals have access only to the data necessary for their roles, minimizing the potential impact of insider threats.
Conclusion
The discovery of this vulnerability in Microsoft’s Copilot for M365 highlights the critical importance of comprehensive audit logs in maintaining security and compliance. The ability to access sensitive files without leaving a trace poses significant risks, particularly for organizations in regulated industries. Microsoft’s handling of the disclosure process and decision against public notification have raised concerns about transparency and commitment to security. Organizations must take proactive steps to assess their exposure, enhance monitoring, and engage with Microsoft to ensure the integrity of their security systems.