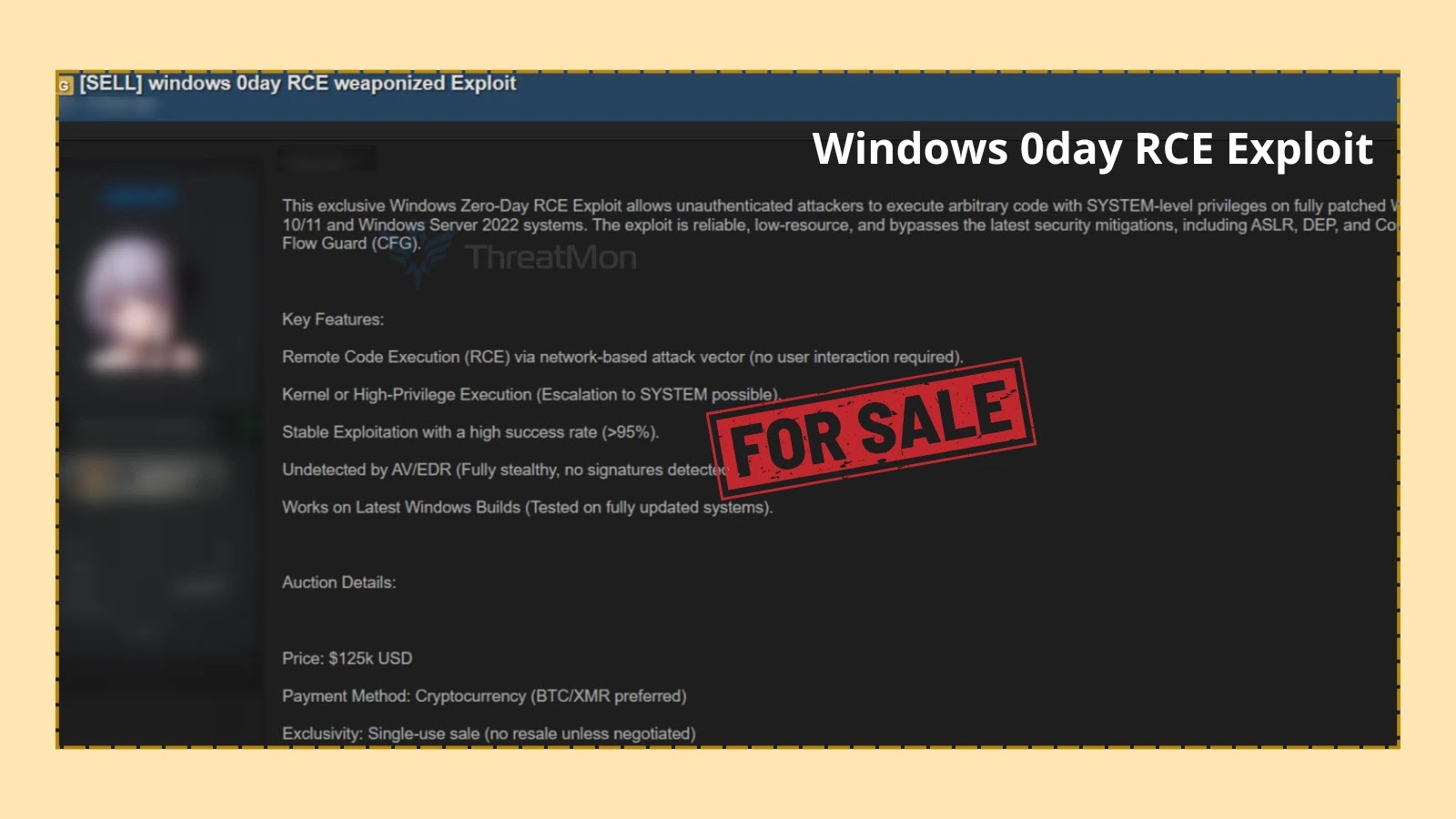
A threat actor has reportedly listed a Windows Zero-Day Remote Code Execution (RCE) exploit for sale on the dark web, claiming it targets fully updated Windows 10, Windows 11, and Windows Server 2022 systems. The exploit is advertised as capable of granting SYSTEM-level privileges without prior authentication or user interaction, effectively bypassing Windows security mechanisms such as Address Space Layout Randomization (ASLR), Data Execution Prevention (DEP), and Control Flow Guard (CFG).
Technical Capabilities and Implications
The seller emphasizes the exploit’s technical prowess, offering kernel-level code execution and privilege escalation directly to SYSTEM—a critical concern for both enterprise and individual systems. The exploit is designed for remote code execution via a network-based attack vector, eliminating the need for any user interaction. This tactic aligns with the most dangerous categories of vulnerabilities, especially those facilitating unauthenticated remote attack surface exploitation.
The exploit’s capacity to elevate privileges—typically from a standard user to SYSTEM, the highest Windows permission level—is particularly alarming. Additionally, direct interaction and manipulation of the Windows kernel bypasses typical user-mode restrictions. The advertisement claims that the exploit is undetected by leading antivirus and endpoint detection and response (EDR) solutions, boasting a stealthy profile with no signatures detected. With a purported success rate exceeding 95%, the exploit’s reliability makes it exceptionally attractive to advanced persistent threat (APT) groups and ransomware operators.
Market Dynamics and Sale Conditions
Auction details reveal an asking price of USD 125,000, with payment preferred via cryptocurrency (BTC/XMR), reflecting the high market demand for robust, undetectable exploit code. The sale conditions emphasize exclusivity, prohibiting resale unless explicitly negotiated, which is typical for premium exploits.
Broader Context of Zero-Day Exploits
This incident is part of a broader trend where threat actors are increasingly monetizing zero-day vulnerabilities. For instance, in May 2024, a threat actor listed an Outlook RCE zero-day exploit for $1.8 million, targeting various versions of Microsoft Office. Similarly, in April 2024, claims surfaced about a Windows zero-day local privilege escalation (LPE) exploit being sold for $80,000. These instances highlight the lucrative nature of zero-day exploits in the cybercriminal underground.
Recommendations for Organizations
Organizations facing heightened threat landscapes should reinforce monitoring of anomalous kernel-level activity, enforce timely patch management, and deploy advanced threat intelligence tools capable of detecting zero-day exploitation attempts. The incident underscores the persistent risks associated with unreported vulnerabilities and the continued evolution of cybercrime marketplaces.
It is recommended to stay informed of emerging threat intelligence feeds, apply available mitigations, and report suspicious activity associated with zero-day vulnerabilities to relevant authorities and vendors.