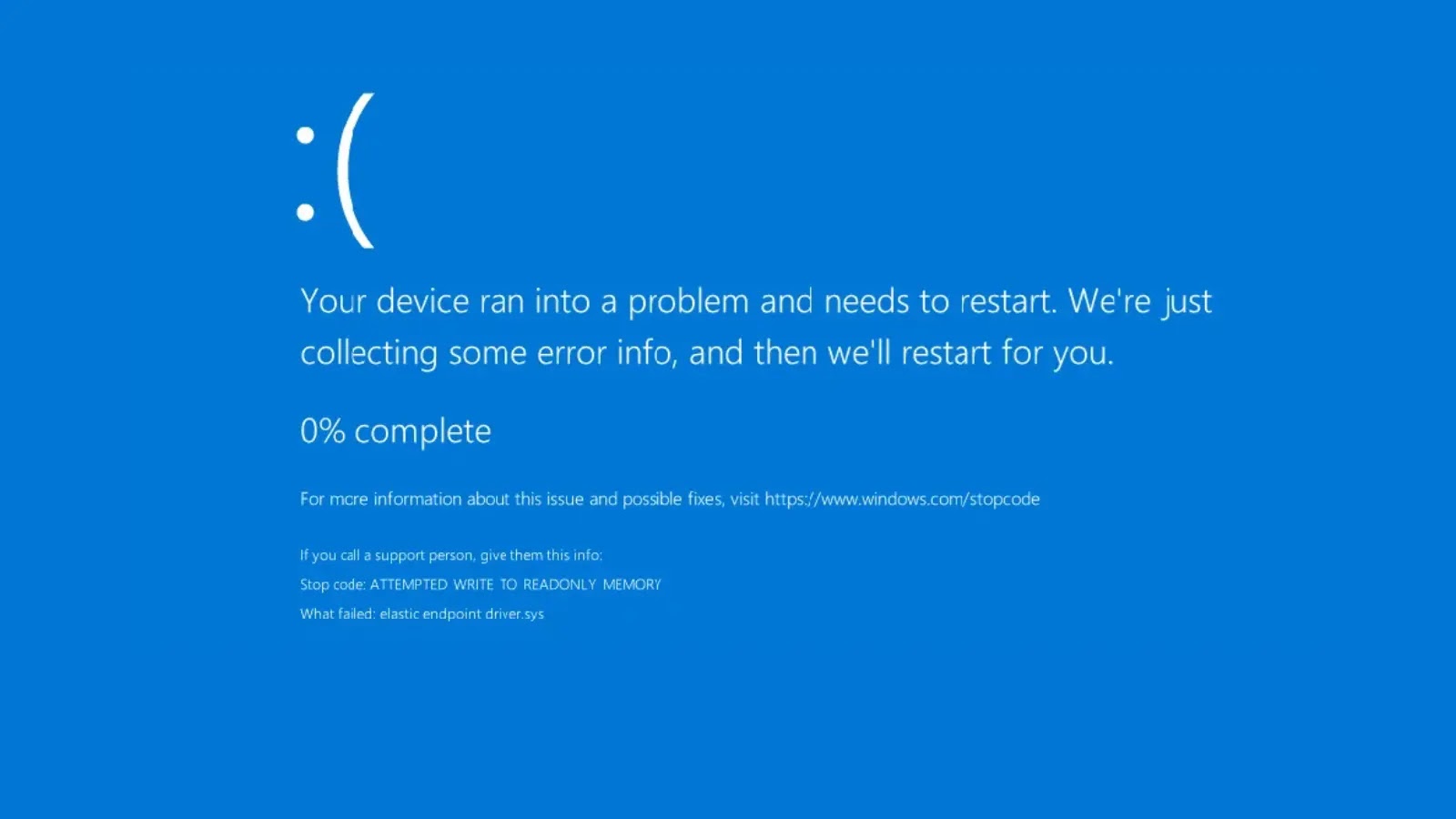
A recently identified zero-day vulnerability within Elastic’s Endpoint Detection and Response (EDR) solution poses significant security threats, enabling attackers to circumvent detection mechanisms, execute malicious code, and induce system crashes, commonly referred to as the Blue Screen of Death (BSOD). This discovery, attributed to research conducted by Ashes Cybersecurity, highlights a critical flaw in a core component of Elastic’s security software, potentially transforming a defensive tool into an instrument of attack against the very systems it is designed to protect.
Vulnerability Details
The vulnerability resides in the elastic-endpoint-driver.sys, a kernel driver that is both signed by Microsoft and developed by Elasticsearch, Inc. This driver is integral to the functionality of Elastic Defend and Elastic Agent security solutions. The flaw is classified as a CWE-476: NULL Pointer Dereference, indicating improper handling of memory operations within the driver’s privileged kernel routines.
Specifically, under certain conditions, a pointer controllable from user-mode is passed into a kernel function without adequate validation. If this pointer is null, has been freed, or is corrupted, the kernel’s attempt to dereference it results in a system-wide crash, manifesting as a BSOD. This vulnerability not only undermines system stability but also opens avenues for attackers to exploit the flaw for malicious purposes.
Exploitation Methodology
The exploitation of this vulnerability follows a structured four-step attack chain:
1. EDR Bypass: Attackers employ a custom loader to circumvent Elastic’s security protections, effectively blinding the EDR system.
2. Remote Code Execution (RCE): With the EDR disabled, attackers can execute malicious code on the system without detection or obstruction.
3. Persistence: Attackers establish persistence by installing a custom kernel driver that interacts with the vulnerable Elastic driver, ensuring continued access and control over the compromised system.
4. Privileged Persistent Denial of Service: Finally, attackers can trigger repeated system crashes, rendering the system unusable and causing significant operational disruptions.
This methodical approach not only compromises system integrity but also demonstrates the potential for the Elastic driver to be manipulated into exhibiting behavior akin to malware.
Implications for Enterprises
The ramifications of this zero-day vulnerability are particularly severe for organizations that rely on Elastic’s security products. Enterprises utilizing Elastic’s Security Information and Event Management (SIEM) and EDR solutions may unknowingly harbor a vulnerability that can be remotely exploited to disable endpoints on a large scale. This scenario presents a substantial risk, as a trusted, signed kernel driver can be transformed into a persistent, privileged weapon against the organization’s own infrastructure.
Disclosure Timeline and Affected Versions
The timeline of the vulnerability’s discovery and disclosure is as follows:
– June 2, 2025: Initial discovery of the vulnerability.
– June 11, 2025: Disclosure attempt made through HackerOne.
– July 29, 2025: Disclosure attempt made through the Zero Day Initiative (ZDI).
– August 16, 2025: Independent disclosure of the vulnerability.
The affected product is elastic-endpoint-driver.sys in version 8.17.6. It is believed that all subsequent versions are also vulnerable, as no patch has been released to address the issue.
Researcher Insights
The researcher from Ashes Cybersecurity, who discovered the vulnerability during user-mode testing operations, emphasized the gravity of the situation. Their organization is a paying customer of Elastic, underscoring the widespread impact of the flaw. The researcher stated, A defender that crashes, blinds, or disables its own system on command is indistinguishable from malware, highlighting the erosion of trust this vulnerability causes not only in Elastic but in the broader security industry. Until a patch is issued, customers remain exposed to this active zero-day threat.
Recommendations for Mitigation
In light of this vulnerability, organizations utilizing Elastic’s EDR solutions should take the following steps to mitigate potential risks:
1. Monitor for Unusual Activity: Implement enhanced monitoring to detect signs of exploitation, such as unexpected system crashes or unauthorized code execution.
2. Restrict Privileged Access: Limit the number of users with administrative privileges to reduce the risk of exploitation.
3. Apply Security Patches Promptly: Stay informed about updates from Elastic and apply security patches as soon as they become available.
4. Conduct Regular Security Audits: Perform thorough security assessments to identify and remediate potential vulnerabilities within the organization’s infrastructure.
By proactively addressing these areas, organizations can enhance their security posture and reduce the likelihood of successful exploitation of this vulnerability.
Conclusion
The discovery of this zero-day vulnerability within Elastic’s EDR solution underscores the critical importance of rigorous security practices and prompt vulnerability management. Organizations must remain vigilant, continuously monitor their systems, and apply necessary updates to safeguard against emerging threats. The collaboration between security researchers and software vendors is essential in identifying and mitigating vulnerabilities to protect the integrity and reliability of security solutions.