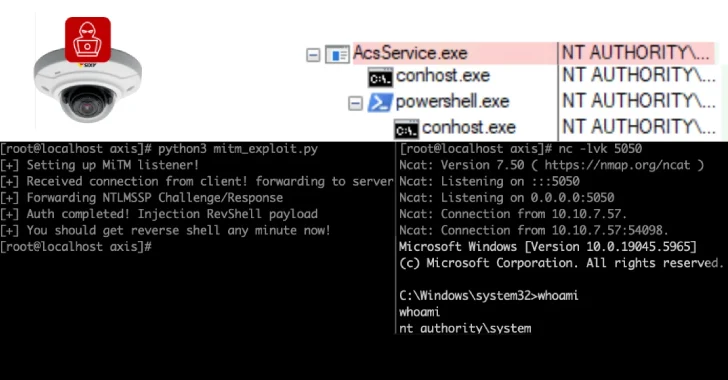
Recent cybersecurity research has uncovered multiple security vulnerabilities in video surveillance products developed by Axis Communications. These flaws, if exploited, could allow unauthorized individuals to take control of affected systems.
Noam Moshe, a researcher at Claroty, highlighted the severity of these issues:
The attack results in pre-authentication remote code execution on Axis Device Manager, a server used to configure and manage fleets of cameras, and the Axis Camera Station, client software used to view camera feeds.
He further noted that attackers could use internet scans of exposed Axis.Remoting services to identify vulnerable servers and clients, enabling precise, targeted attacks.
Identified Vulnerabilities:
The following security flaws have been identified:
1. CVE-2025-30023 (CVSS score: 9.0): A flaw in the communication protocol between client and server could allow an authenticated user to perform a remote code execution attack. This issue has been addressed in Camera Station Pro 6.9, Camera Station 5.58, and Device Manager 5.32.
2. CVE-2025-30024 (CVSS score: 6.8): A vulnerability in the client-server communication protocol could be exploited to execute an adversary-in-the-middle (AitM) attack. This has been fixed in Device Manager 5.32.
3. CVE-2025-30025 (CVSS score: 4.8): A flaw in the communication protocol between the server process and the service control could lead to local privilege escalation. Patches have been released in Camera Station Pro 6.8 and Device Manager 5.32.
4. CVE-2025-30026 (CVSS score: 5.3): A vulnerability in the Axis Camera Station Server could result in authentication bypass. This issue has been resolved in Camera Station Pro 6.9 and Camera Station 5.58.
Potential Impact:
Exploiting these vulnerabilities could allow attackers to position themselves between the Camera Station and its clients, enabling them to alter requests and responses. This could lead to arbitrary actions being executed on both server and client systems. Currently, there is no evidence to suggest that these vulnerabilities have been exploited in real-world scenarios.
Claroty’s research identified over 6,500 servers exposing the proprietary Axis.Remoting protocol and its services on the internet, with nearly 4,000 located in the United States.
Moshe emphasized the risks:
Successful exploits give attackers system-level access on the internal network and the ability to control each of the cameras within a specific deployment. Feeds can be hijacked, watched, and/or shut down. Attackers can exploit these security issues to bypass authentication to the cameras and gain pre-authentication remote code execution on the devices.
Recommendations:
To mitigate these risks, it is crucial for organizations using Axis Communications’ products to:
– Update Software: Ensure that all devices are running the latest versions of Camera Station Pro, Camera Station, and Device Manager, as these updates contain patches for the identified vulnerabilities.
– Restrict Network Exposure: Limit the exposure of Axis.Remoting services to the internet. Implement firewall rules and network segmentation to control access to these services.
– Monitor Systems: Regularly monitor systems for unusual activity that could indicate exploitation attempts.
– Implement Strong Authentication: Use strong, unique passwords for all devices and enable multi-factor authentication where possible.
By taking these steps, organizations can significantly reduce the risk of unauthorized access and potential exploitation of their video surveillance systems.