A recent supply chain attack has compromised ETHcode, a widely used Visual Studio Code (VS Code) extension for Ethereum development, through a malicious GitHub pull request that introduced just two lines of code. This incident underscores the vulnerabilities inherent in software development tools and the potential risks to developers and their projects.
The Attack’s Genesis
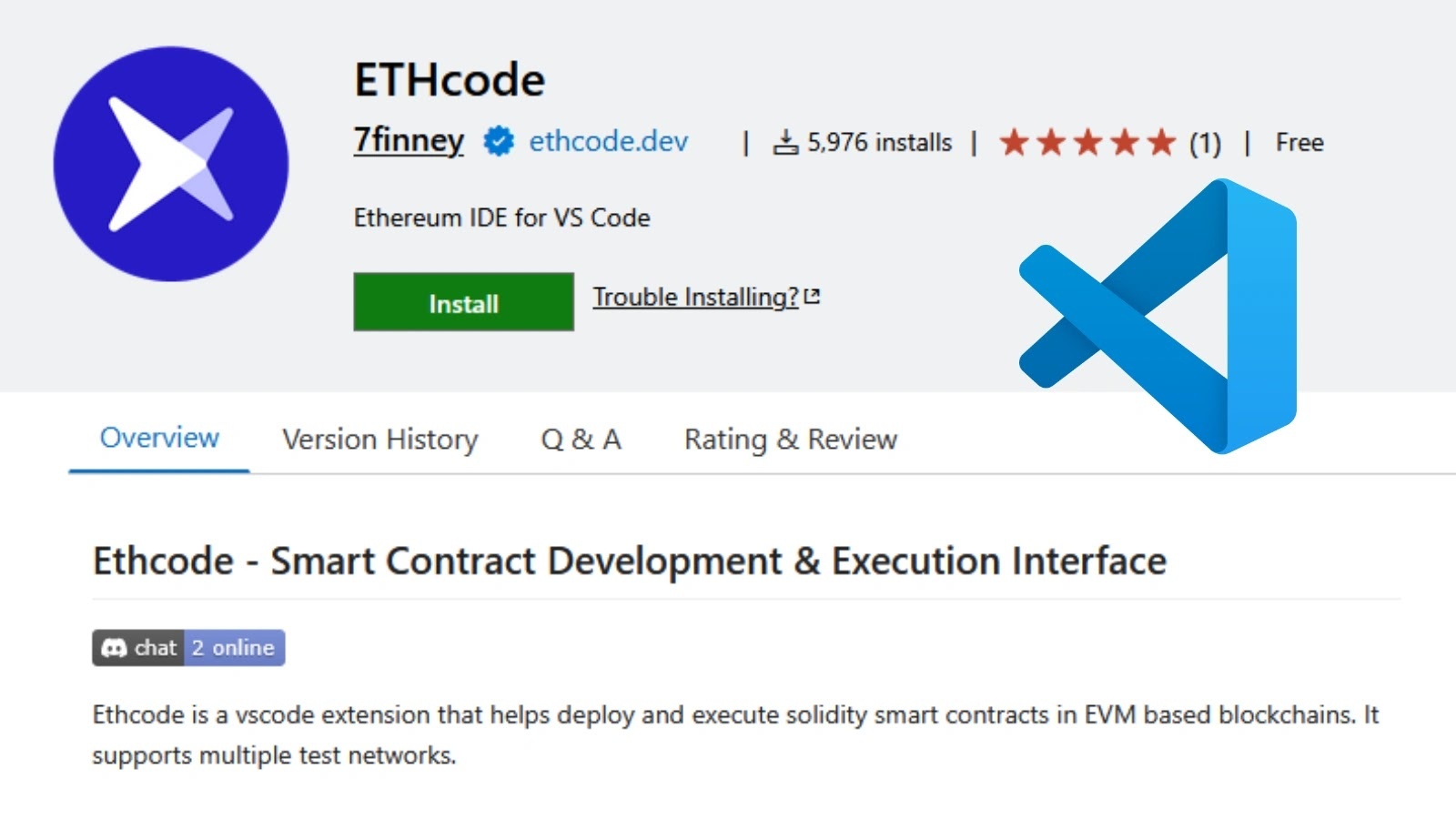
On June 17, 2025, a GitHub user named Airez299 submitted a pull request to the ETHcode project with the message: Modernize codebase with viem integration and testing framework. ETHcode, developed by the 7finney organization, is a legitimate VS Code extension with nearly 6,000 installations, enabling Ethereum developers to test, debug, and deploy smart contracts across Ethereum Virtual Machine (EVM)-based blockchains.
The pull request appeared beneficial, claiming to add new features and modernize the codebase. Given that the ETHcode project had been dormant since September 6, 2024, the submission was particularly convincing. Both human reviewers from the 7finney organization and GitHub’s Copilot AI reviewed the code and approved the changes after requesting minor modifications.
Technical Breakdown of the Malicious Code
Within 43 commits and approximately 4,000 lines of changed code, two critical lines compromised the extension:
1. Introduction of a new dependency named keythereum-utils, designed to appear as a legitimate helper library for the existing keythereum package.
2. Invocation of Node.js’s require function to load and execute the newly introduced dependency.
Analysis of the keythereum-utils package revealed heavily obfuscated JavaScript code that, when deobfuscated, spawned a hidden PowerShell process. This process downloaded and executed a batch script from a public file-hosting service.
Implications and Response
The attack’s effectiveness was amplified by VS Code’s automatic extension update feature, which distributed the malicious code to nearly 6,000 users without their knowledge. ReversingLabs researchers promptly notified Microsoft’s Visual Studio Marketplace administrators, leading to the removal of the compromised extension by June 26.
The 7finney organization released a corrective update, ETHcode version 0.5.1, on July 1, removing the malicious dependency and restoring the extension to the marketplace. Investigations into the second-stage payload’s capabilities are ongoing, with suspicions that it aimed to steal cryptocurrency assets or compromise Ethereum smart contracts under development.
Broader Context of Malicious VS Code Extensions
This incident is part of a growing trend of malicious activities targeting VS Code extensions:
– Cryptojacking Campaigns: In April 2025, researchers discovered a sophisticated cryptojacking campaign involving malicious VS Code extensions. These extensions, published under various author names, amassed over one million installations. Once installed, they downloaded and executed PowerShell scripts that disabled Windows security features, established persistence, and installed XMRig cryptominers. The extensions masqueraded as popular tools, with artificially inflated install counts to appear credible. ([infosecurity-magazine.com](https://www.infosecurity-magazine.com/news/microsoft-vs-code-cryptojacking/?utm_source=openai))
– Password Theft Vulnerabilities: In August 2023, a flaw in VS Code allowed malicious extensions to retrieve authentication tokens stored in Windows, Linux, and macOS credential managers. These tokens are used for integrating with various third-party services and APIs, such as Git and GitHub. The flaw was due to a lack of isolation in VS Code’s ‘Secret Storage,’ enabling any extension to access stored tokens. Despite the discovery, Microsoft decided against fixing the issue, as extensions are not expected to be sandboxed from the rest of the environment. ([bleepingcomputer.com](https://www.bleepingcomputer.com/news/security/microsoft-visual-studio-code-flaw-lets-extensions-steal-passwords/?utm_source=openai))
– Impersonation of Trusted Applications: In January 2025, a malicious VS Code extension impersonated the Zoom application, enabling cybercriminals to steal sensitive cookies from Google Chrome. The extension was uploaded to the VS Code Marketplace and contained code targeting Chrome’s cookie storage, allowing attackers to access users’ sessions on various online platforms. The extension’s uploader included a link to the official GitHub repository for the Zoom Meeting SDK, enhancing its credibility. ([gbhackers.com](https://gbhackers.com/weaponized-vs-code/?utm_source=openai))
Recommendations for Developers
These incidents highlight the critical need for vigilance when installing and managing VS Code extensions:
1. Scrutinize Extensions: Thoroughly review the number of installs and user reviews before adding any extension. Low install counts or lack of reviews may indicate untrustworthiness.
2. Monitor Updates: Regularly review the version history of installed extensions to spot unexpected changes or updates that may signal malicious intent.
3. Implement Security Tools: Incorporate additional security tools and practices, such as browser security extensions and real-time monitoring for unusual behavior, to bolster protection against threats.
4. Educate Teams: Provide ongoing training about the risks associated with Integrated Development Environment (IDE) extensions and best practices for maintaining secure development environments.
The weaponization of VS Code extensions illustrates a growing threat landscape where trusted software environments are targeted for malicious activities. As cyber threats continue to evolve, developers and users must remain vigilant, prioritizing security alongside productivity in their workflows.