In recent developments, cybercriminals have been capitalizing on the widespread interest in artificial intelligence (AI) tools, such as ChatGPT and Luma AI, to orchestrate sophisticated malware distribution campaigns. By creating deceptive websites that mimic legitimate AI resources, these threat actors aim to lure unsuspecting users into downloading malicious software.
Exploitation of AI Enthusiasm
The surge in AI tool popularity has provided cybercriminals with a fertile ground for social engineering attacks. By leveraging the public’s curiosity and trust in AI technologies, attackers have developed fraudulent websites that closely resemble authentic AI platforms. These sites are meticulously designed to appear credible, often featuring content that mirrors legitimate blog posts and informational resources.
Search Engine Manipulation
To maximize their reach, these malicious actors employ Black Hat Search Engine Optimization (SEO) techniques. By poisoning search engine results, they ensure that their deceptive websites rank prominently when users search for popular AI tools. For instance, queries like Luma AI blog may lead users directly to these harmful sites. This manipulation significantly increases the likelihood of users encountering and interacting with malicious content.
Sophisticated Malware Delivery Mechanisms
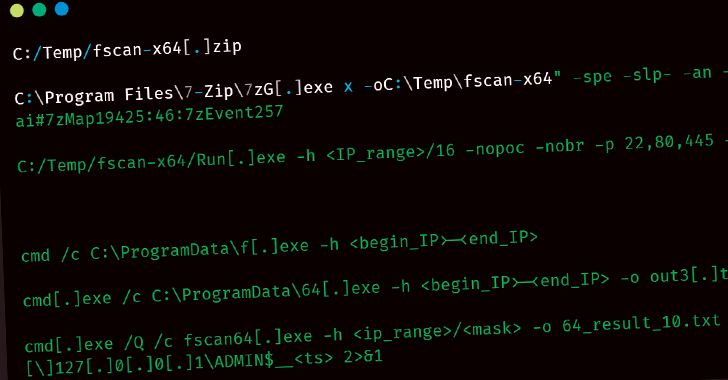
Researchers from Zscaler have identified a complex redirection chain utilized by these campaigns. Upon visiting a compromised site, users are subjected to a series of redirects that ultimately deliver dangerous payloads, including Vidar Stealer, Lumma Stealer, and Legion Loader. These malware variants are designed to steal sensitive information, such as login credentials and financial data, from infected systems.
Technical Sophistication and Evasion Tactics
The technical prowess of these campaigns is noteworthy. Attackers employ multiple layers of obfuscation and evasion techniques to avoid detection by security solutions. The infrastructure behind these attacks has generated over 4.4 million hits since January 2025, indicating the massive scale and potential impact of this ongoing campaign.
JavaScript-Based Infection and Evasion Mechanisms
The core infection mechanism relies on sophisticated JavaScript code that demonstrates advanced evasion capabilities and precise targeting methodologies. When a victim lands on one of the malicious websites, the JavaScript performs comprehensive browser fingerprinting operations, collecting detailed information about the victim’s system configuration, browser details, and network environment. This data is then encrypted and transmitted to attacker-controlled infrastructure for validation and processing.
Implications and Recommendations
The exploitation of AI tool popularity underscores the evolving tactics of cybercriminals. Users are advised to exercise caution when searching for and downloading AI-related tools. It is crucial to verify the authenticity of websites and avoid downloading software from untrusted sources. Employing robust security solutions and staying informed about emerging threats can significantly reduce the risk of falling victim to such sophisticated attacks.