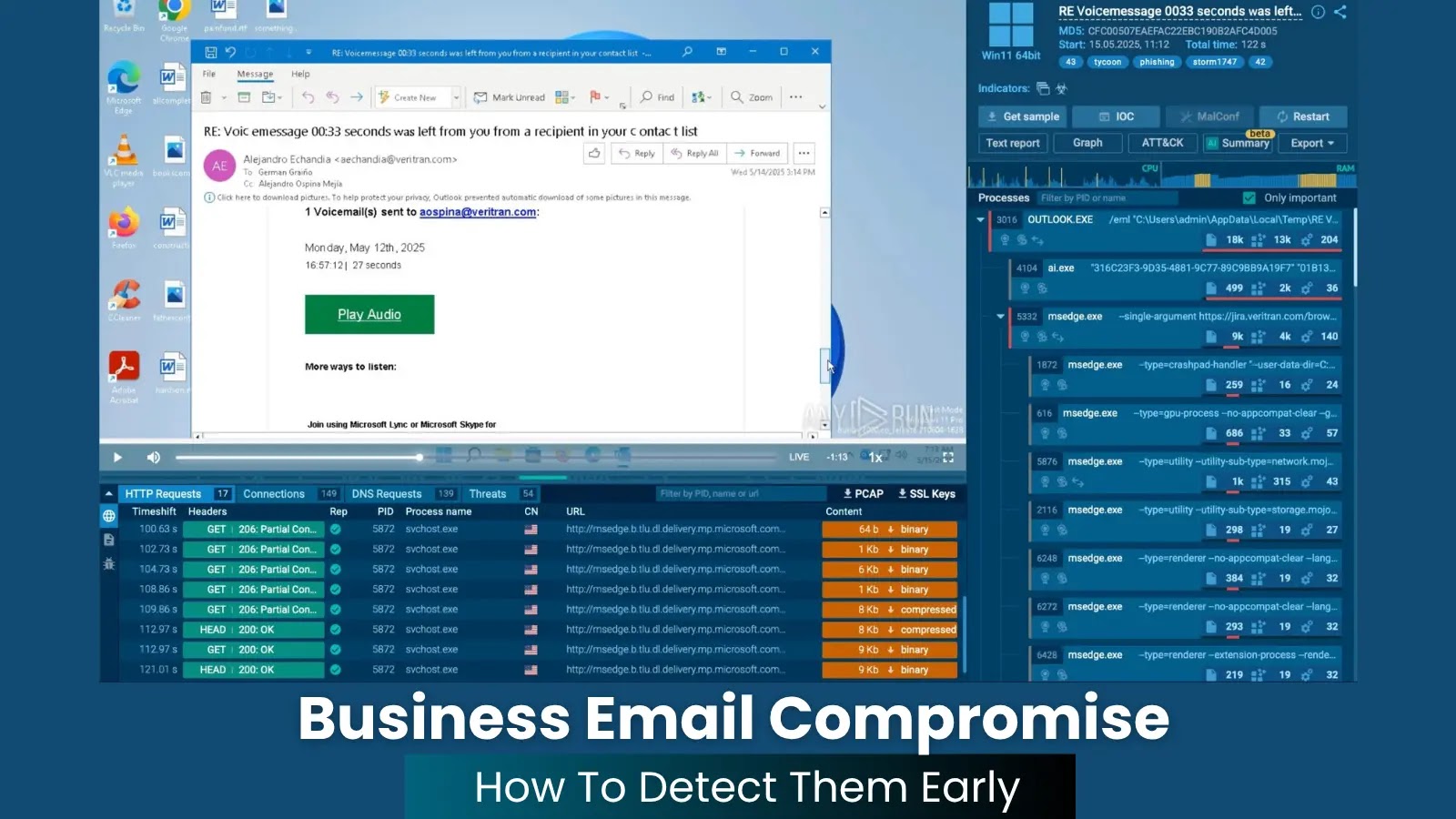
Business Email Compromise (BEC) attacks have emerged as a significant threat to organizations worldwide. Unlike traditional cyberattacks that rely on malware, BEC schemes exploit human trust and social engineering to deceive employees into divulging sensitive information or authorizing fraudulent financial transactions. The subtlety and sophistication of these attacks make them particularly challenging to detect and prevent.
Understanding the Mechanics of BEC Attacks
BEC attacks typically involve cybercriminals impersonating trusted figures within an organization, such as executives or vendors, to manipulate employees into performing actions that compromise security. These actions often include transferring funds to fraudulent accounts or disclosing confidential information. The attackers meticulously research their targets, crafting messages that appear legitimate and contextually appropriate, thereby increasing the likelihood of success.
The Escalating Threat Landscape
Recent data underscores the growing prevalence and impact of BEC attacks:
– Surge in Incidents: Social engineering-based BEC attacks have risen by 1,760% in the past year, largely driven by advancements in generative artificial intelligence (GenAI). This technology enables attackers to create highly convincing and targeted emails that are difficult to distinguish from genuine communications. ([cybernews.com](https://cybernews.com/news/ai-behind-surge-in-bec/?utm_source=openai))
– Rapid Execution: Investigations reveal that BEC attacks can unfold within a matter of hours. From the initial compromise of credentials to the execution of fraudulent activities, attackers operate swiftly, leaving minimal time for detection and response. ([bleepingcomputer.com](https://www.bleepingcomputer.com/news/security/microsoft-business-email-compromise-attacks-can-take-just-hours/?utm_source=openai))
– Financial Impact: The financial repercussions of BEC attacks are staggering. In 2023 alone, the FBI’s Internet Crime Complaint Center (IC3) reported adjusted losses of $2.9 billion attributed to BEC incidents. This figure highlights the substantial economic damage inflicted by such schemes. ([origin-www.paloaltonetworks.com](https://origin-www.paloaltonetworks.com/cyberpedia/what-is-business-email-compromise-bec-tactics-and-prevention?utm_source=openai))
Challenges in Detecting BEC Attacks
Several factors contribute to the difficulty in identifying BEC attacks:
– Absence of Malware: Traditional security measures often focus on detecting malicious software. However, BEC attacks typically do not involve malware, relying instead on deceptive communications, which can bypass standard detection tools.
– Use of Trusted Platforms: Attackers frequently utilize reputable services like OneDrive or Google Forms to host phishing content, exploiting the inherent trust associated with these platforms to evade suspicion.
– Sophisticated Social Engineering: By leveraging detailed knowledge of organizational structures and internal processes, attackers craft messages that are contextually relevant and convincing, making it challenging for employees to discern fraudulent communications.
Strategies for Early Detection and Prevention
To mitigate the risks associated with BEC attacks, organizations can implement the following strategies:
1. Employee Training and Awareness: Regularly educate staff on recognizing phishing attempts, suspicious emails, and unusual requests. Emphasize the importance of verifying unexpected communications, especially those involving financial transactions or sensitive information.
2. Multi-Factor Authentication (MFA): Implement MFA across all email accounts to add an additional layer of security. This measure ensures that even if credentials are compromised, unauthorized access is significantly more difficult.
3. Email Authentication Protocols: Deploy protocols such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) to verify the authenticity of incoming emails and reduce the risk of spoofing.
4. Payment Verification Processes: Establish procedures that require multiple levels of verification for financial transactions, including direct confirmation with the requesting party through a separate communication channel.
5. Advanced Threat Detection Tools: Utilize interactive sandboxing solutions that allow security teams to analyze suspicious files or URLs in a controlled environment, enabling real-time observation of potential threats without risking the organization’s network.
6. Regular Security Audits: Conduct periodic reviews of security protocols and systems to identify vulnerabilities and ensure that defenses are up to date against evolving threats.
Conclusion
The rise of BEC attacks necessitates a proactive and comprehensive approach to cybersecurity. By understanding the tactics employed by cybercriminals and implementing robust detection and prevention measures, organizations can significantly reduce their vulnerability to these insidious threats. Continuous education, technological investment, and vigilant monitoring are key components in safeguarding against the financial and reputational damages associated with BEC attacks.