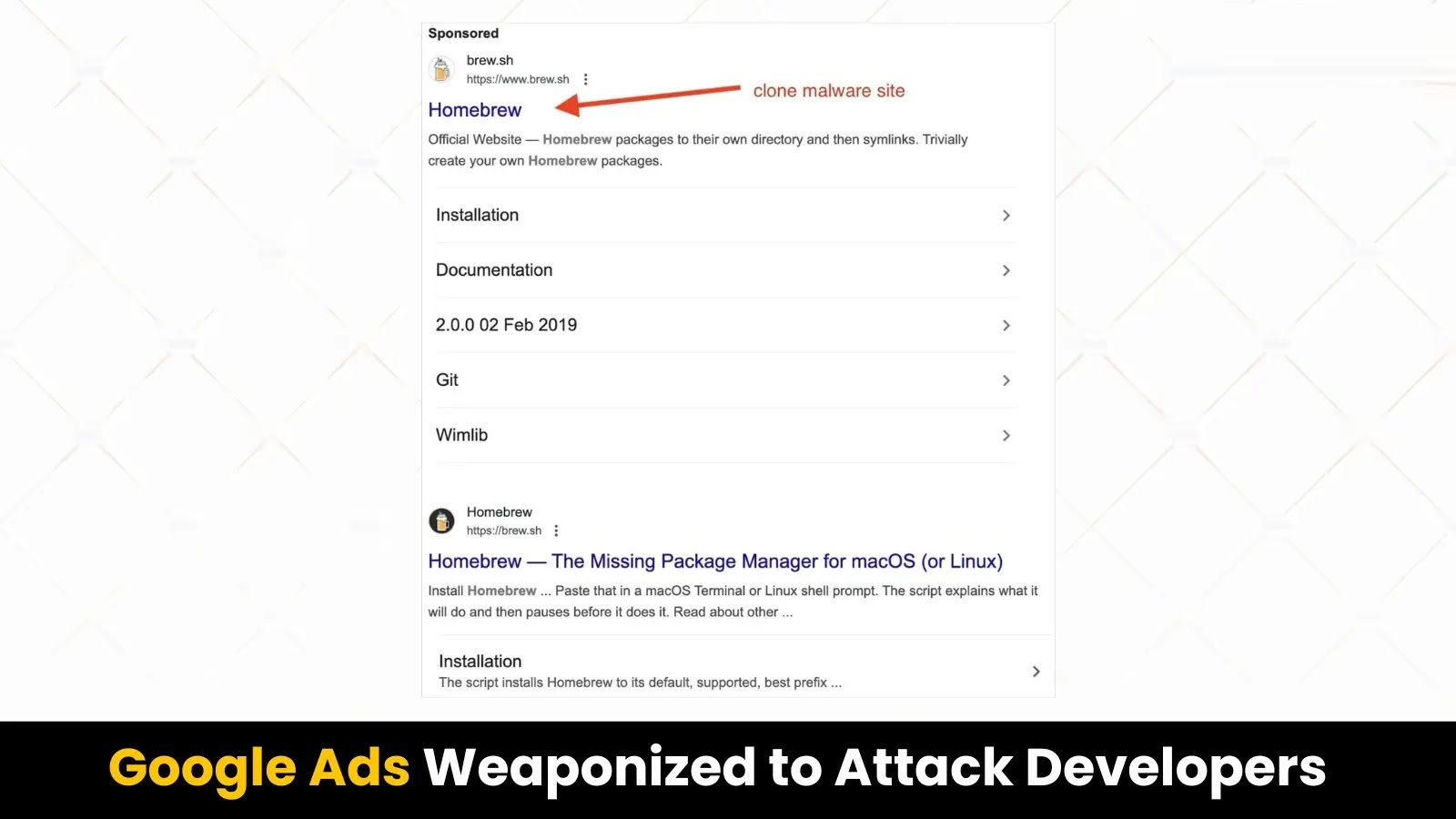
In a recent and sophisticated cyberattack, malicious actors have been leveraging Google Ads to deceive macOS and Linux users into downloading the AmosStealer malware through a counterfeit Homebrew website. This campaign underscores the evolving tactics of cybercriminals who exploit trusted platforms to disseminate harmful software.
Discovery of the Malvertising Campaign
On January 18, 2025, developer Ryan Chenkie identified a deceptive Google Ads campaign targeting users searching for Homebrew, a widely-used open-source package manager. The malicious advertisement displayed the legitimate Homebrew URL, brew.sh, but redirected users to a fraudulent site, brewe.sh, differing by only one letter. This subtle alteration is a common tactic in phishing schemes, designed to mislead users into believing they are accessing a legitimate website.
Technical Execution of the Attack
Upon visiting the counterfeit site, users were presented with installation instructions that closely mirrored those of the authentic Homebrew website. The site prompted users to execute a command in their terminal, ostensibly to install Homebrew. However, running this command resulted in the download and execution of AmosStealer, also known as Atomic Stealer, a potent information-stealing malware tailored for macOS systems.
Capabilities of AmosStealer
AmosStealer is a sophisticated malware-as-a-service offering, available to cybercriminals for a monthly subscription fee of $1,000. Its capabilities include:
– Credential Theft: Extracting usernames and passwords stored on the infected device.
– Browser Data Harvesting: Collecting cookies, browsing history, and other sensitive information from web browsers.
– Cryptocurrency Wallet Targeting: Accessing and exfiltrating data from over 50 cryptocurrency extensions and desktop wallets, including popular platforms like Binance, Coinomi, Electrum, and Exodus.
The malware’s focus on cryptocurrency assets highlights the financial motivations driving such attacks.
Response from the Homebrew Project
Mike McQuaid, the project leader of Homebrew, acknowledged the issue but emphasized the project’s limited ability to prevent such attacks. He criticized Google’s ad review process, stating, Google seems to like taking money from scammers. While the clone site has since been taken down, the incident highlights a recurring problem: Google’s inability to effectively police its ad platform.
Broader Implications and Ongoing Concerns
This incident is part of a larger trend where cybercriminals exploit online advertising platforms to distribute malware. By manipulating search engine optimization (SEO) and utilizing malicious advertisements, attackers can effectively reach a broad audience. The use of legitimate-looking URLs that redirect to malicious sites is a particularly insidious tactic, as it can deceive even vigilant users.
The campaign also underscores the challenges faced by online platforms in detecting and preventing such malicious activities. Despite efforts to monitor and remove harmful content, the dynamic nature of these attacks makes it difficult to provide comprehensive protection.
Recommendations for Users
To mitigate the risk of falling victim to similar attacks, users are advised to:
1. Verify URLs Carefully: Before clicking on links, especially those in advertisements, ensure the URL is correct. Be cautious of subtle misspellings or variations.
2. Avoid Sponsored Links for Software Downloads: Whenever possible, navigate directly to the official website of the software by typing the URL into the browser or using a trusted bookmark.
3. Implement Robust Security Measures: Utilize comprehensive endpoint protection solutions that can detect and block malicious activities.
4. Stay Informed: Keep abreast of the latest cybersecurity threats and tactics employed by malicious actors.
By adopting these practices, users can enhance their security posture and reduce the likelihood of falling prey to such deceptive campaigns.
Conclusion
The exploitation of Google Ads to distribute malware through a fake Homebrew site highlights the sophisticated methods employed by cybercriminals to target users. This incident serves as a stark reminder of the importance of vigilance and proactive security measures in the digital age.