In a sophisticated cyberattack campaign, dubbed Payroll Pirates, threat actors are leveraging malicious Google Ads to deceive employees into divulging sensitive payroll information, resulting in the redirection of paychecks to fraudulent accounts. This campaign primarily targets users of Workday and employees of prominent organizations such as the California Employment Development Department (EDD), Kaiser Permanente, Macy’s, New York Life, and Roche.
The Mechanism of the Attack
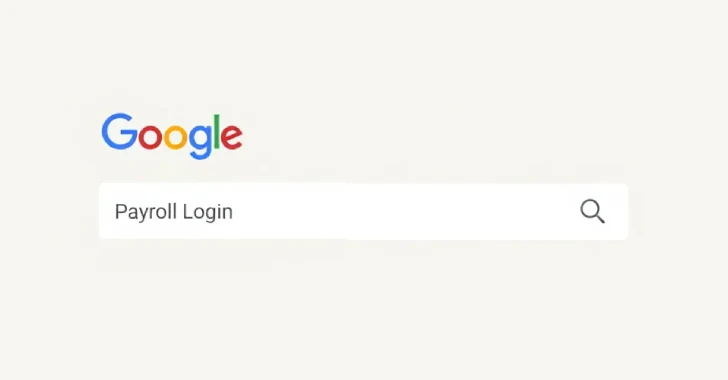
The attackers purchase search ads using brand-specific keywords to position their phishing websites at the top of search engine results. When employees search for their company’s payroll portal, they may inadvertently click on these sponsored links, leading them to counterfeit HR login pages that closely mimic legitimate portals. Once employees enter their credentials, the attackers gain unauthorized access to payroll systems. Armed with additional personal information, such as Social Security numbers—likely obtained from underground forums—the cybercriminals alter direct deposit details, redirecting salaries to accounts under their control.
Tactics and Tools Employed
To facilitate rapid deployment of these phishing sites, the attackers utilize website builders like Mobirise, Wix, and Leadpages. They register domains through popular providers such as Dynadot, Porkbun, and Namecheap, and often host phishing content in directories like /online to mimic legitimate HR portal structures. Additionally, the attackers exploit compromised home office routers and mobile networks to mask their activities, making detection more challenging. By targeting employee mobile devices, which often lack enterprise-grade security measures, they further evade traditional security defenses.
Broader Implications and FBI Warnings
This campaign is part of a broader trend where cybercriminals target online payroll accounts across various industries to divert funds. The Federal Bureau of Investigation (FBI) has issued warnings about such schemes, emphasizing the need for heightened vigilance. The FBI advises organizations to educate employees on recognizing phishing attempts, implement multi-factor authentication, and monitor for unauthorized changes to direct deposit information.
Mitigation Strategies
To defend against these evolving threats, organizations should adopt a multi-layered security approach:
1. Employee Training: Regularly educate staff on identifying phishing attempts, emphasizing the importance of scrutinizing email addresses, URLs, and unexpected requests for sensitive information.
2. Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security, ensuring that even if credentials are compromised, unauthorized access is prevented.
3. Advanced Email and Web Filtering: Deploy AI-powered tools to detect and block phishing emails and malicious links before they reach employees.
4. Regular Software Updates: Keep all systems and software up to date to patch vulnerabilities that cybercriminals might exploit.
5. Monitor Payroll Changes: Establish protocols to verify any changes to direct deposit information, such as requiring in-person confirmation or additional authentication steps.
6. Restrict Access: Limit internet access on systems handling sensitive information and consider adopting two-factor authentication for access to critical systems.
Conclusion
The Payroll Pirates campaign underscores the increasing sophistication of phishing attacks and the importance of proactive cybersecurity measures. By combining employee education, robust security protocols, and vigilant monitoring, organizations can better protect themselves against these evolving threats.