A sophisticated malware campaign, dubbed ‘Desert Dexter’, has been uncovered, targeting nearly 900 victims across the Middle East and North Africa (MENA). The attackers exploit Facebook ads and Telegram channels to trick users into downloading a trojanized version of the AsyncRAT malware, granting them full control over compromised systems.
How the Attack Works
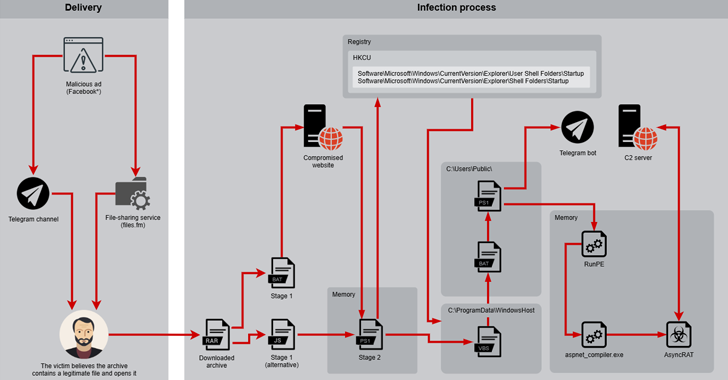
Cybercriminals behind Desert Dexter use social engineering tactics to manipulate users into infecting their devices. Their methods include:
- Fake News & Leaks: Fraudulent Facebook pages and Telegram groups masquerade as news outlets, promoting exclusive “leaked” documents or confidential reports that entice users to click.
- Malicious Downloads: Victims unknowingly download ZIP or RAR files containing scripts disguised as documents or utilities.
- Stealthy Execution: Once executed, a hidden PowerShell script disables security measures, modifies system settings, and installs AsyncRAT.
- Persistent Control: The malware injects itself into system processes, enabling remote access, keystroke logging, and data exfiltration.
What Makes This Malware Dangerous?
Unlike conventional RATs (Remote Access Trojans), this attack does not rely on traditional command and control (C2) servers. Instead, it leverages Telegram bots, making detection more challenging. Key capabilities include:
- Offline Keylogging: Records keystrokes even without an internet connection.
- Cryptocurrency Theft: Specifically targets crypto wallets and exchange extensions.
- File & Screenshot Theft: Periodically captures screenshots and exfiltrates sensitive documents.
- Device Hijacking: Allows attackers to remotely control the victim’s device for espionage or financial fraud.
Why This Matters
The campaign appears strategically designed to exploit users in industries such as oil production, construction, technology, and finance—sectors crucial to the MENA economy. The malware’s code includes Arabic-language comments, hinting at possible ties to Libyan cybercriminal groups.
With geopolitical tensions high in the region, misinformation campaigns and cyberattacks have become a preferred weapon. Desert Dexter exemplifies how threat actors weaponize social media and human curiosity to deploy sophisticated malware.
How to Stay Safe
- Avoid Clicking Suspicious Links – Be skeptical of “exclusive leaks” or documents claiming to reveal hidden truths.
- Verify Sources – Ensure news comes from credible platforms and not newly created or unknown Facebook/Telegram accounts.
- Use Multi-Layered Security – Enable two-factor authentication (2FA) on sensitive accounts and install reputable antivirus software.
- Keep Software Updated – Malware often exploits system vulnerabilities. Keeping your OS and apps updated helps close security gaps.
This cyberattack demonstrates the increasing intersection between social media manipulation and cybercrime, proving that vigilance is more critical than ever.