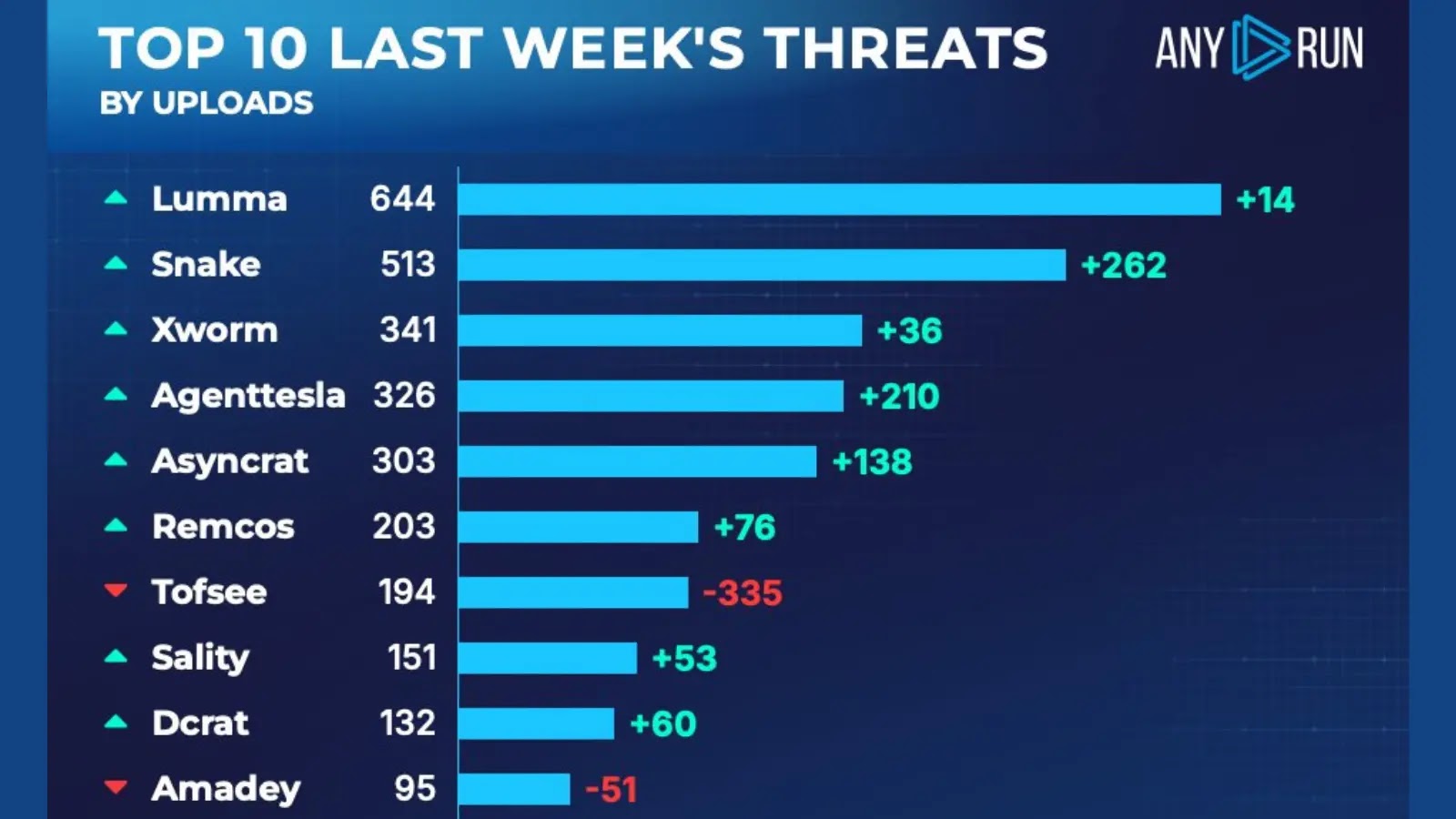
A new cybercrime operation led by the threat actor EncryptHub is ramping up attacks using ransomware, info stealers, and trojanized applications. The group has been active since mid-2024, employing increasingly sophisticated techniques to target individuals and organizations worldwide.
EncryptHub’s primary attack method includes phishing campaigns that use fake websites and social engineering tactics to trick victims into downloading malware. These phishing sites, hosted on bulletproof hosting services, often impersonate trusted applications such as Google Meet, WeChat, Microsoft Visual Studio, and Palo Alto GlobalProtect.
Once a victim downloads and installs one of these trojanized applications, the malware executes PowerShell scripts that deploy information stealers like Fickle, StealC, and Rhadamanthys. These tools silently extract passwords, banking credentials, cryptocurrency wallets, and session tokens, handing them over to attackers.
EncryptHub isn’t just relying on phishing. The group is also using Pay-Per-Install (PPI) services, a tactic where cybercriminals pay third-party distributors to spread malware in bulk. These services allow the attackers to infect thousands of devices quickly and efficiently, making it difficult for cybersecurity teams to detect and block infections.
A More Dangerous Evolution: EncryptRAT and Ransomware
In addition to stealing information, EncryptHub has been linked to ransomware attacks, locking victims’ systems and demanding hefty payments in cryptocurrency. To further expand its operations, EncryptHub is developing a new remote access tool called EncryptRAT, designed to remotely control infected systems, execute commands, and exfiltrate stolen data.
This development suggests that EncryptHub is evolving from a malware distributor to a full-fledged cybercrime operation, with the capability to steal sensitive data, hijack accounts, and extort victims at scale.
How to Stay Protected
- Avoid downloading software from unofficial sources – Always verify applications from legitimate websites.
- Be cautious of phishing links – Hover over links before clicking and look out for misspellings in URLs.
- Use endpoint protection – Install anti-malware software that detects and blocks malicious scripts.
- Monitor for unusual activity – Unexpected login attempts and unauthorized access could indicate an infection.
As EncryptHub continues refining its attack techniques, organizations and individuals must remain vigilant. This group’s combination of ransomware, stealers, and remote access tools marks a growing cyber threat that requires strong security practices and rapid incident response.