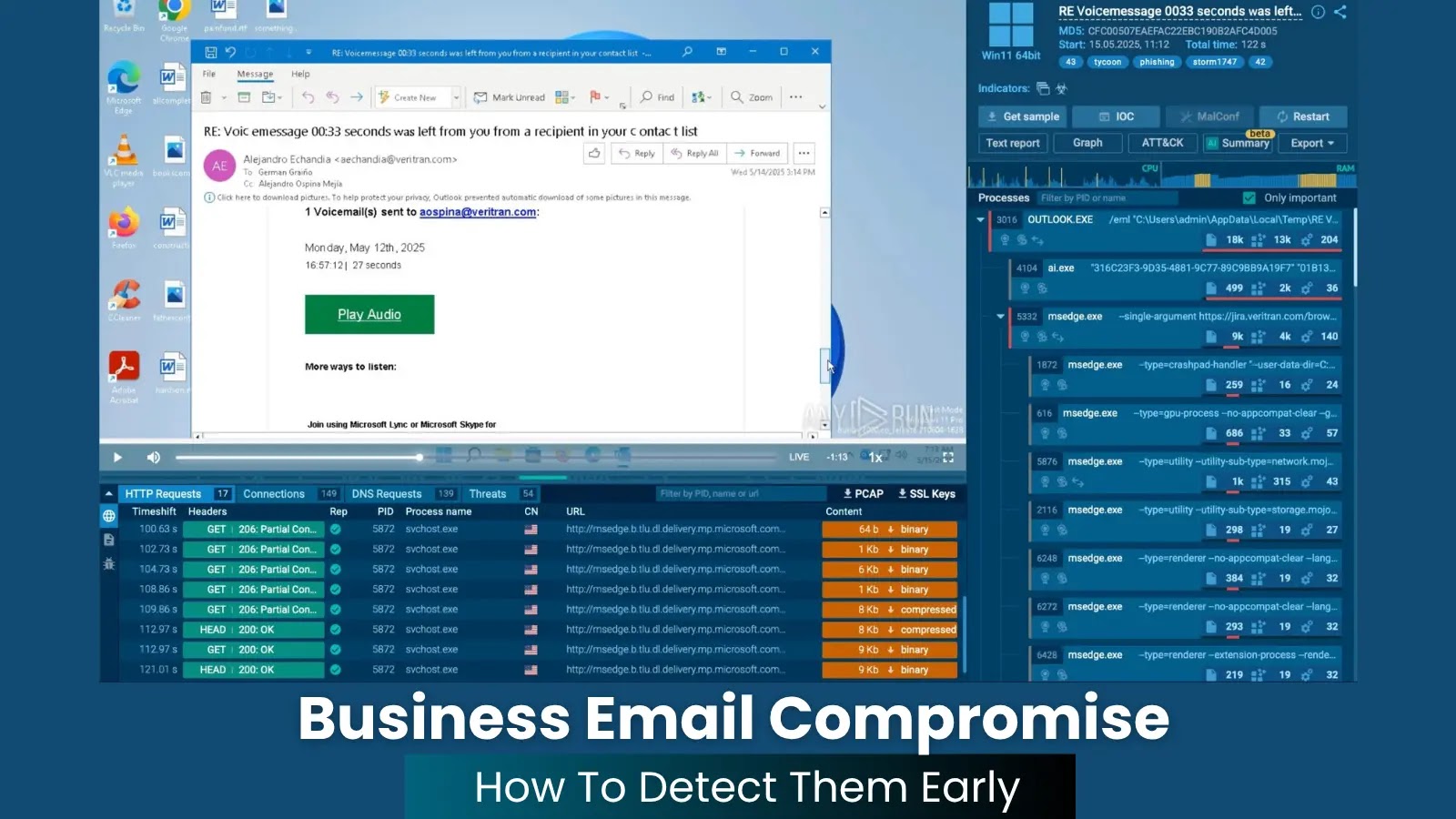
Escalating Cyber Espionage Threats Target Defense Sector’s Supply Chains
In today’s interconnected world, the defense sector is increasingly vulnerable to sophisticated cyber espionage campaigns. State-sponsored actors and cybercriminal groups are intensifying their efforts to infiltrate defense contractors, aerospace manufacturers, and associated supply chains. These attacks aim to steal sensitive data, disrupt critical logistics, and undermine national security.
Evolving Attack Vectors
Cyber adversaries are shifting their strategies to exploit edge devices and employ advanced social engineering tactics. By targeting unmonitored virtual private networks (VPNs), firewalls, and manipulating hiring processes, attackers can bypass traditional enterprise security measures. This approach allows them to gain initial access and maintain long-term presence within high-value networks without triggering standard detection systems.
The INFINITERED Malware: A Case Study
A notable example of this evolving threat landscape is the INFINITERED malware, deployed by the China-linked group UNC6508. This malware exemplifies stealthy, long-term espionage tactics against research and defense institutions. INFINITERED functions as a recursive dropper, embedding itself within legitimate system files of the REDCap application to survive software updates. This persistence mechanism ensures that even as administrators patch their systems, the malicious code is automatically reinjected into core files, maintaining a foothold for the attackers.
Stealthy Data Exfiltration Techniques
Once inside a network, attackers utilize specific methods to exfiltrate sensitive communications without generating standard network traffic noise. They abuse legitimate email filtering rules, modifying them to automatically forward messages that match specific keywords related to national security, military equipment, or foreign policy. By using regular expressions to scan email bodies and subjects, the malware quietly redirects critical intelligence to actor-controlled accounts. This technique allows the espionage campaign to remain undetected for extended periods, as it leverages authorized administrative tools rather than introducing noisy external code.
Mitigation Strategies
To counter these advanced threats, organizations must adopt proactive measures:
1. Enhanced Monitoring: Implement rigorous monitoring for edge devices and enforce strict behavioral analytics for email forwarding rules.
2. Verification Processes: Strengthen verification processes for remote personnel to prevent social engineering attacks.
3. Network Segmentation: Segment critical supply chain networks to limit the potential impact of a breach.
4. Regular Updates: Ensure all systems and applications are regularly updated and patched to mitigate vulnerabilities.
5. Employee Training: Conduct regular cybersecurity training for employees to recognize and respond to potential threats.
By implementing these strategies, defense sector organizations can significantly reduce the risk of successful cyber espionage campaigns and protect national security interests.