Critical n8n Vulnerability Allows Remote Code Execution via Malicious Workflows
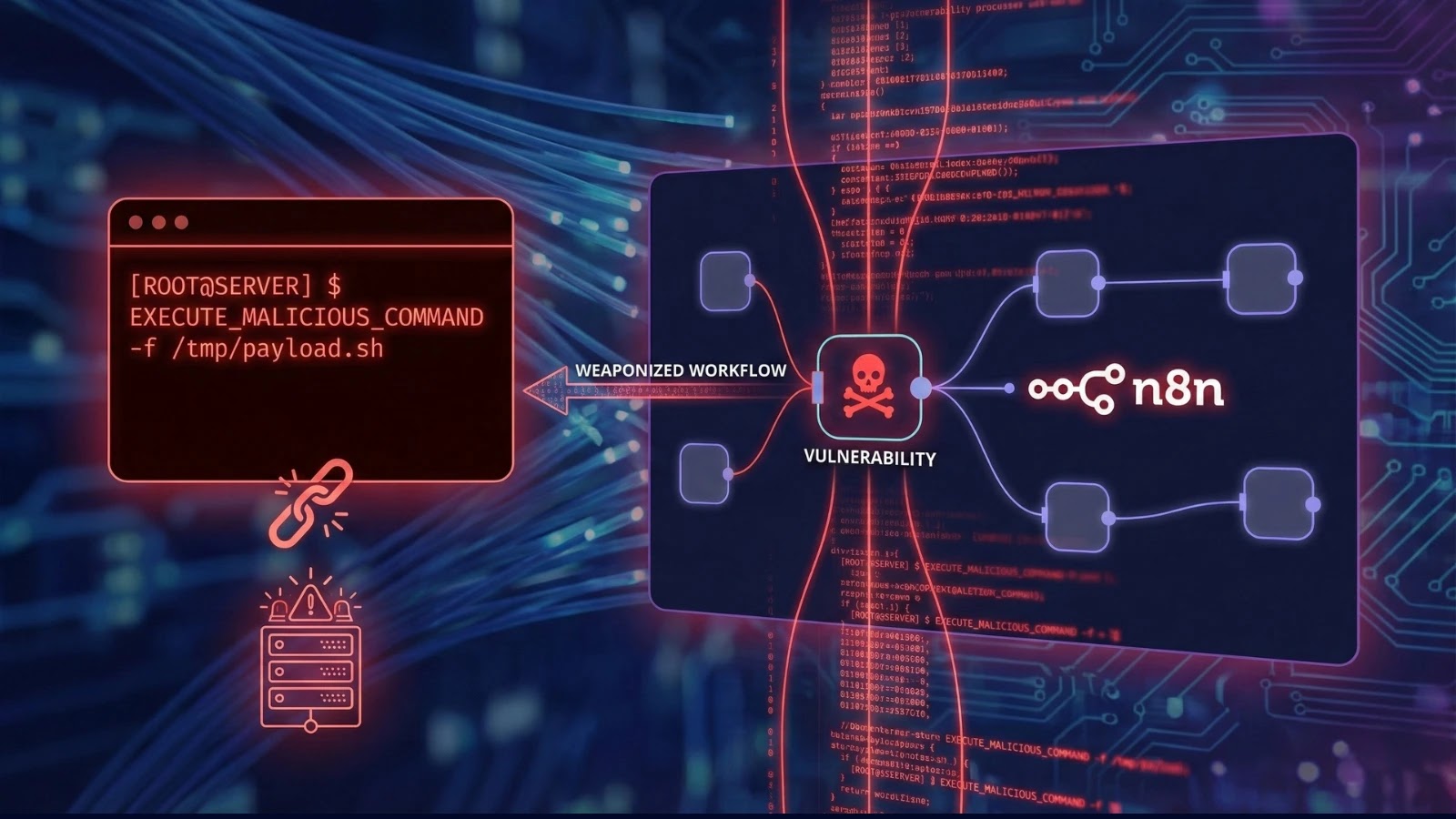
A critical remote code execution (RCE) vulnerability has been identified in n8n, a widely used open-source workflow automation platform. This flaw enables authenticated users to execute arbitrary system commands on the host server by crafting malicious workflows. The vulnerability, a regression of the previously identified CVE-2025-68613, underscores ongoing security challenges within n8n’s expression evaluation engine.
Understanding the Vulnerability
n8n facilitates the creation of automated workflows by connecting various applications and services. Users can incorporate dynamic expressions within workflow nodes to process and transfer data between steps. However, this functionality has been exploited by attackers who, with valid authentication credentials, can inject malicious code into these expressions. By doing so, they can bypass input sanitization measures and execute system-level commands.
The risk is particularly acute for self-hosted n8n instances operating with default configurations and broad permissions. Once a compromised workflow is activated—either manually or through automated triggers—the injected code runs with the same privileges as the n8n process. This can lead to:
– Complete control over the host server.
– Unauthorized access to internal networks.
– Theft of sensitive API keys and credentials stored within n8n’s credential management system.
Remediation and Patching
In response to this critical issue, the n8n development team has released patches in versions 1.123.17 and 2.5.2. These updates enhance the validation processes for expression evaluation, effectively preventing the execution of unauthorized shell commands within workflow parameters.
Organizations utilizing n8n are strongly advised to upgrade to these patched versions without delay. For those unable to implement the update immediately, the following interim measures can help mitigate risk:
– Restrict Workflow Permissions: Limit the ability to create or modify workflows to trusted users only.
– Enhance Network Security: Deploy n8n within a secured environment, restricting its network access to minimize exposure.
– Monitor System Activity: Regularly review system logs for any signs of unauthorized processes initiated by the n8n service.
While these steps can reduce the immediate threat, they are not substitutes for applying the official security patches.
Broader Implications
This vulnerability highlights the critical importance of securing automation platforms like n8n, which often serve as central hubs connecting various services and data sources. A compromised n8n instance can act as a gateway for attackers to infiltrate an organization’s broader digital infrastructure.
The recurrence of such vulnerabilities emphasizes the need for continuous vigilance and proactive security measures. Organizations should:
– Regularly Update Software: Keep all software components up to date to benefit from the latest security patches.
– Conduct Security Audits: Periodically review system configurations and access controls to identify and address potential weaknesses.
– Educate Users: Train staff on best practices for security, including recognizing phishing attempts and the importance of using strong, unique passwords.
By implementing these strategies, organizations can enhance their resilience against similar vulnerabilities in the future.