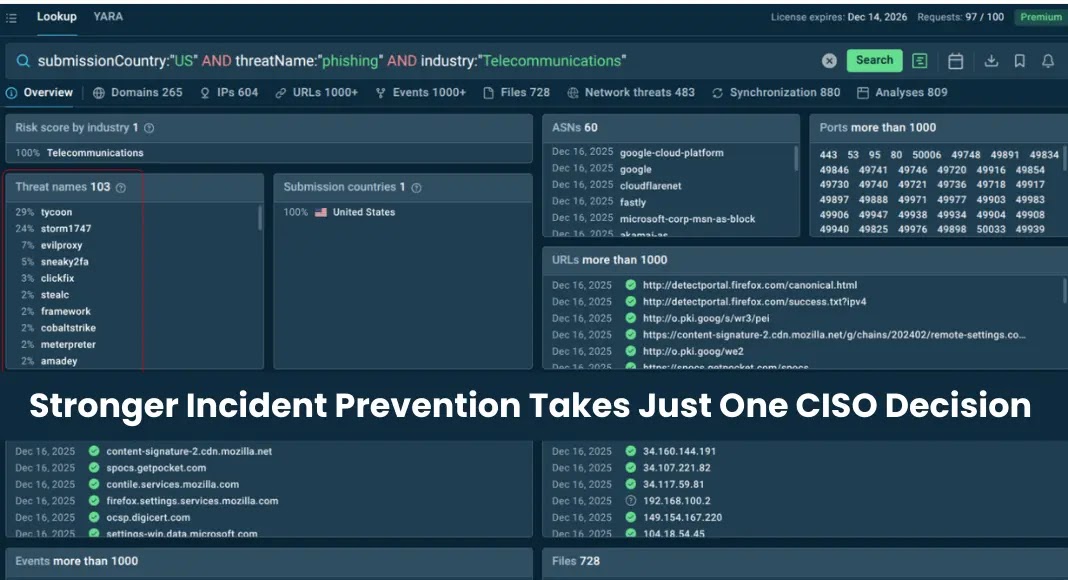
Enhancing Incident Prevention: A Strategic Shift for CISOs
In the realm of cybersecurity, a prevalent misconception suggests that increasing staff numbers equates to enhanced security. However, this approach often overlooks the core issue: the quality and timeliness of threat intelligence. Security Operations Centers (SOCs) frequently grapple with inefficiencies not due to a lack of personnel but because of inadequate, outdated, or irrelevant threat data.
The Pitfall of Overstaffing
Many organizations respond to escalating cyber threats by expanding their security teams. While this may seem proactive, it doesn’t necessarily translate to improved security outcomes. The cybersecurity industry faces a persistent talent shortage, making it impractical to rely solely on hiring as a solution. Instead, the focus should shift towards enhancing the quality of threat intelligence, enabling existing teams to operate more effectively.
Common SOC Challenges and Strategic Solutions
1. Alert Overload
Problem: SOCs are inundated with alerts from various security tools, leading to significant time spent distinguishing genuine threats from false positives.
Why Hiring Fails: Adding more analysts doesn’t reduce the volume of low-quality alerts; it merely distributes the workload without addressing the root cause.
Strategic Solution: Implementing high-fidelity threat intelligence feeds can enrich alerts with real-time, behavior-based indicators. This approach helps analysts prioritize genuine threats, reducing false positives and enhancing decision-making speed.
2. Delayed Threat Detection
Problem: Prolonged detection times increase the risk and potential impact of security incidents.
Why Hiring Fails: Detection speed is more dependent on the freshness and relevance of threat data than on the number of analysts.
Strategic Solution: Utilizing continuously updated threat intelligence feeds allows SOC tools to recognize and respond to threats earlier, thereby reducing dwell time and preventing escalation.
3. Analyst Burnout and High Turnover
Problem: Repetitive tasks and constant pressure lead to analyst fatigue, resulting in high turnover rates and loss of institutional knowledge.
Why Hiring Fails: Replacing experienced analysts with new hires resets the learning curve and doesn’t address the underlying issues causing burnout.
Strategic Solution: Providing actionable, reliable threat intelligence reduces cognitive load, allowing analysts to focus on meaningful work and improving job satisfaction and retention.
4. Reactive Security Posture
Problem: Organizations often find themselves reacting to incidents rather than proactively preventing them.
Why Hiring Fails: Without timely and relevant threat data, even a larger team remains in a reactive mode.
Strategic Solution: Integrating real-time threat intelligence feeds enables a proactive security stance, allowing teams to anticipate and mitigate threats before they materialize.
5. Inefficient Resource Allocation
Problem: Resources are often misallocated due to a lack of clear threat prioritization.
Why Hiring Fails: More personnel without improved intelligence leads to continued inefficiencies.
Strategic Solution: High-quality threat intelligence provides clarity, ensuring that resources are directed towards the most pressing threats, optimizing both time and effort.
Conclusion
For Chief Information Security Officers (CISOs), the path to stronger incident prevention lies not in expanding teams but in enhancing the quality of threat intelligence. By investing in real-time, behavior-based threat data, organizations can empower their existing security teams to operate more efficiently, reduce burnout, and adopt a proactive security posture. This strategic shift not only addresses current challenges but also positions organizations to better handle the evolving cyber threat landscape.