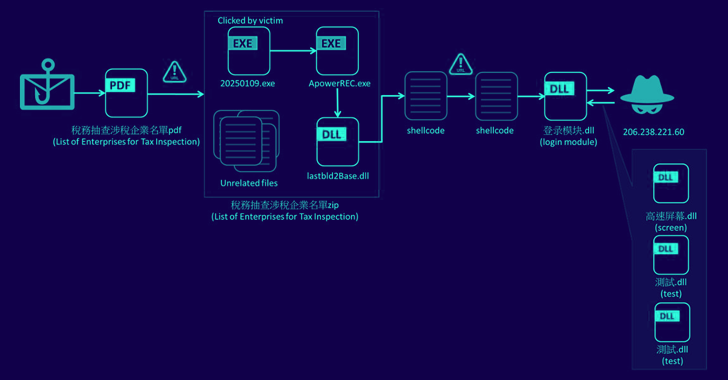
A sophisticated advanced persistent threat (APT) group, known as “Silver Fox,” has been observed deploying a newly identified malware strain called “WinOS 4.0” in targeted attacks. This malware, demonstrating advanced capabilities, poses a significant threat to organizations and individuals, highlighting the evolving tactics of state-sponsored and financially motivated cybercriminals.
Silver Fox, known for its targeted attacks against high-value targets, has adopted WinOS 4.0 to enhance its arsenal. This malware exhibits advanced features, including sophisticated evasion techniques, robust persistence mechanisms, and the ability to exfiltrate sensitive data. Its deployment signifies a significant escalation in the group’s capabilities.
WinOS 4.0 distinguishes itself through its ability to bypass traditional security measures. It employs advanced obfuscation techniques to mask its presence and evade detection by antivirus and intrusion detection systems. The malware’s developers have incorporated sophisticated anti-analysis techniques, making it challenging for security researchers to reverse-engineer and analyze.
Furthermore, WinOS 4.0 demonstrates robust persistence capabilities, ensuring that it remains active even after system reboots. It achieves this by establishing multiple persistence mechanisms, including modifying system registry entries and creating scheduled tasks. This allows the malware to maintain a foothold on compromised systems, enabling long-term surveillance and data exfiltration.
The malware’s data exfiltration capabilities are also noteworthy. WinOS 4.0 is capable of collecting a wide range of sensitive information, including documents, credentials, and other confidential data. It employs encrypted communication channels to exfiltrate this data to remote command-and-control servers, ensuring that the data remains secure during transmission.
The deployment of WinOS 4.0 by Silver Fox highlights the ongoing threat posed by APT groups. Organizations should take proactive steps to protect themselves from these advanced threats. This includes:
- Implementing multi-layered security: Employing a comprehensive security approach that includes firewalls, intrusion detection systems, and endpoint protection.
- Regular threat intelligence: Staying informed about the latest threats and vulnerabilities.
- Security awareness training: Educating employees about phishing and other social engineering tactics.
- Incident response planning: Developing and testing incident response plans to ensure that they can effectively respond to security incidents.
- Zero Trust Architecture: Implementing a Zero Trust security model to restrict access and limit lateral movement.
The discovery of WinOS 4.0 underscores the importance of continuous vigilance and adaptation in the face of evolving cyber threats.