Mastering Cybersecurity: Implementing Continuous Threat Exposure Management
In the rapidly evolving landscape of cybersecurity, organizations are moving beyond isolated assessments of threats and vulnerabilities. The focus has shifted to understanding how these elements intersect within specific environments, leading to real, exploitable exposures. This approach raises critical questions: Which exposures are truly significant? Can attackers exploit them? Are our defenses effective?
Continuous Threat Exposure Management (CTEM) offers a structured methodology to address these concerns, guiding cybersecurity teams toward a unified management of threats, vulnerabilities, and exposures.
Understanding CTEM
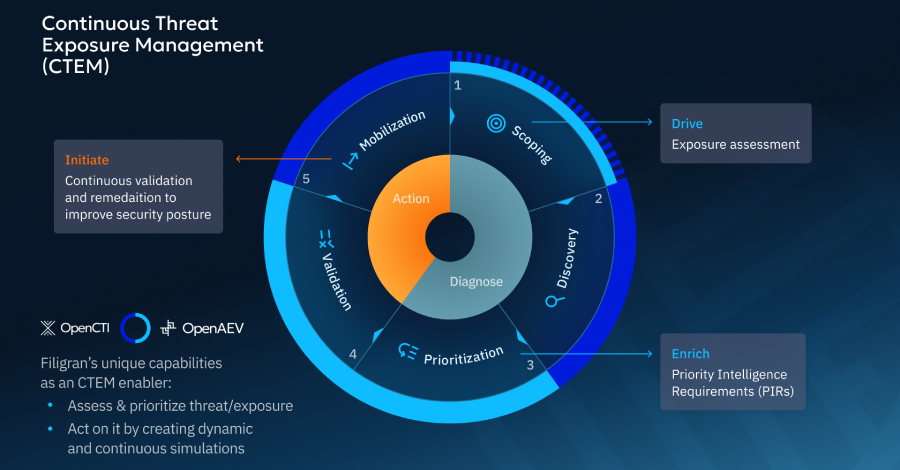
As defined by Gartner, CTEM emphasizes a continuous cycle of identifying, prioritizing, and remediating exploitable exposures across an organization’s attack surface. This process enhances overall security posture through a five-step operational model:
1. Scoping: Evaluate threats and vulnerabilities to identify critical assets, processes, and potential adversaries.
2. Discovery: Map exposures and attack paths within the environment to anticipate adversarial actions.
3. Prioritization: Concentrate on exposures that attackers can realistically exploit and determine necessary fixes.
4. Validation: Test assumptions through controlled attack simulations to assess the effectiveness of defenses.
5. Mobilization: Implement remediation and process improvements based on gathered evidence.
The Real Benefit of CTEM
CTEM shifts the focus to risk-based exposure management, integrating various sub-processes and tools such as vulnerability assessment, attack surface management, testing, and simulation. By unifying exposure assessment and validation, CTEM enables security teams to record and report potential impacts on cyber risk reduction. This approach challenges the traditional siloed view of threats and vulnerabilities, advocating for a comprehensive perspective that addresses truly exploitable exposures to reduce overall cyber risk.
Role of Threat Intelligence in CTEM
With over 40,000 vulnerabilities reported in 2024, yet less than 10% exploited, threat intelligence becomes crucial in identifying those that matter most to an organization. By connecting vulnerabilities to adversary tactics, techniques, and procedures (TTPs) observed in active campaigns, threat intelligence helps specify Priority Intelligence Requirements (PIRs). This prioritization focuses remediation efforts on exploitable vulnerabilities within the specific environment, rather than theoretical possibilities.
Organizations should assess whether they are optimizing the value from the threat data they collect, making this a primary area for improvement.
Validation-Driven Risk Reduction
Prioritized threat intelligence should be followed by testing and validation to evaluate how security controls withstand probable exploitations and attack paths. A comprehensive security validation program must encompass technology, processes, and personnel. Even well-configured tools like EDR, SIEM, or WAF offer limited protection if incident workflows are unclear, playbooks are outdated, or escalation paths fail under pressure. This necessitates a convergence of breach and attack simulation, tabletop exercises, and automated penetration testing toward Adversarial Exposure Validation (AEV).
Avoiding Buzzwords
CTEM is not a product but a strategic approach utilizing outcome-driven metrics for exposure management. Its implementation requires leadership-driven initiatives that break down silos and enhance security workflows across teams. Starting with the ‘Scoping’ stage, organizations should define the scope of their exposure management program by addressing questions such as:
– What are our top business risks that cybersecurity can directly influence?
– Which environments (on-premises, cloud, IT/OT, subsidiaries) and asset types (critical assets, endpoints, identity systems, data stores) are in scope?
– Do we have an accurate inventory of these assets?
– Which threat actors and attack methods are most relevant to our industry and technology stack?
– How will we incorporate existing threat intelligence and incident data to refine the scope?
– How will we define ‘critical exposure’ based on exploitability, business impact, data sensitivity, and potential impact radius?
– Are we capable of validating tools, processes, and personnel today?
– What is our initial capacity to remediate issues within this scope, considering resources, tools, and service level agreements (SLAs)?
Addressing these questions helps define a realistic, risk-aligned CTEM scope that can be executed and measured effectively, avoiding overly broad and unmanageable efforts.
Conclusion
CTEM is effective when it provides evidence-based answers to critical questions:
– What can harm us?
– How could it happen?
– Can we prevent it?
By adopting CTEM, organizations can proactively manage their threat exposures, ensuring that security efforts are focused on the most significant risks and that defenses are validated against real-world attack scenarios.