Cybercriminals Exploit Stolen Credentials to Deploy LogMeIn RMM for Stealthy System Access
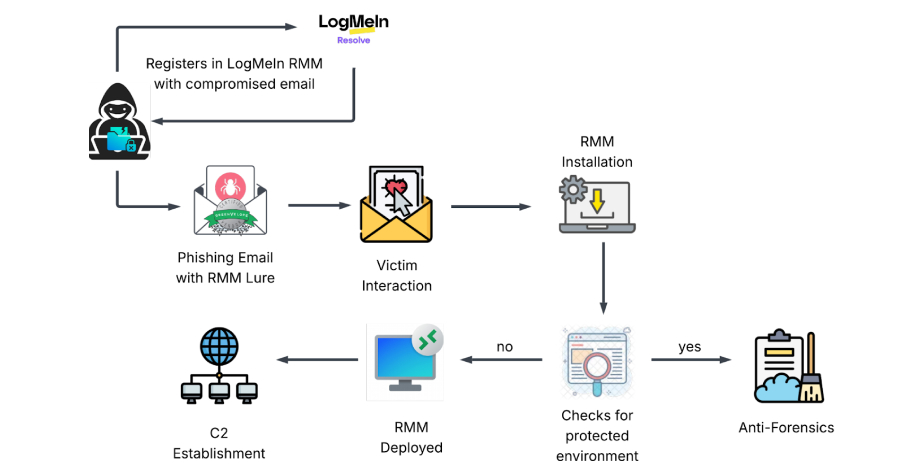
In a sophisticated cyberattack, malicious actors are leveraging stolen user credentials to install legitimate Remote Monitoring and Management (RMM) software, specifically LogMeIn, to gain persistent and covert access to compromised systems. This method allows attackers to bypass traditional security measures by utilizing trusted administrative tools as backdoors.
The attack is executed in two primary stages. Initially, victims receive deceptive emails masquerading as invitations from Greenvelope, a legitimate online invitation service. These emails contain links that direct recipients to phishing sites designed to harvest login credentials for Microsoft Outlook, Yahoo!, and AOL accounts. Once the attackers obtain these credentials, they proceed to the next phase.
In the subsequent stage, the cybercriminals use the stolen email credentials to register with LogMeIn, generating RMM access tokens. They then deploy an executable file named GreenVelopeCard.exe, which is signed with a valid certificate to avoid detection. This file silently installs LogMeIn Resolve (formerly known as GoTo Resolve) on the victim’s system, establishing a connection to an attacker-controlled server without the user’s knowledge.
Once the RMM tool is in place, the attackers manipulate its service settings to ensure it operates with unrestricted access on Windows systems. They also create hidden scheduled tasks that automatically relaunch the RMM program if it is terminated, thereby maintaining persistent access to the compromised system.
To mitigate such threats, organizations are advised to monitor their networks for unauthorized RMM installations and unusual usage patterns. Implementing robust email filtering, educating employees about phishing tactics, and enforcing multi-factor authentication can further enhance security and reduce the risk of credential theft and unauthorized system access.